Install and configure email handling solutions on TMG 2010 Firewall - Part 5
Network Administration - In Part 5 of this series, I will show you how to configure the Edge Subscription feature on the TMG 2010 firewall.
 Install and configure the solution to handle email on TMG 2010 Firewall - Part 1: Installation
Install and configure the solution to handle email on TMG 2010 Firewall - Part 1: Installation
 Install and configure email handling solutions on TMG 2010 Firewall - Part 2: E-Mail Policy
Install and configure email handling solutions on TMG 2010 Firewall - Part 2: E-Mail Policy
 Install and configure email handling solutions on TMG 2010 Firewall - Part 3: Anti-spam
Install and configure email handling solutions on TMG 2010 Firewall - Part 3: Anti-spam
 Install and configure email handling solutions on TMG 2010 Firewall - Part 4:
Install and configure email handling solutions on TMG 2010 Firewall - Part 4:
In this section, which will be the final part of the series, I will show you how to configure the Edge Subscription feature. Edge Subscription is a very useful feature, which allows you to block predefined mail for users who are not in your Exchange organization. This is a very valuable tool, because if you look at your spam statistics, you will certainly find that the overwhelming majority of spam is targeted at users who do not exist in your organization. Locking such 'address-exploiting' emails can help us take a big step in improving the overall performance of Exchange Server.
Finally, we will also test our configuration and try to see if the entire configuration process we have done is working well. We have set up a basic Exchange Server 2010 server behind the TMG firewall. What we will do is try sending some spam from a computer in the Internet through the TMG firewall, then send out some spam through the TMG firewall.
Create an Edge Subscription file and configure the Edge Subscription
The first thing you need to know is not to create an Edge Subscription. However, this method will help your email handling solution become more efficient. It will improve the anti-spam features, allow the lookup of recipients so that mail sent to users who are not in the organization (non-user) will be rejected, besides allowing the collection of lists. safe. Information about users in your Active Directory forest will be sent to an Active Directory LDS database located on the TMG firewall via a secure LDAP connection. In addition, Safe Senders lists and recipient information are hashed so that they are not blocked during transmission.
Information transmitted between Active Directory and TMG Active Directory LDS database includes:
- Edge subscription information
- Configuration information
- Receiver's information
- Information about network topology
EdgeSync services use secure LDAP connections over TCP port 50636 to synchronize directory information between Exchange Hub Server and the TMG firewall's Exchange Edge server.
With some background knowledge, let's create the Edge Subscription file. In the TMG firewall console, click E-Mail Policy in the left pane. In the right pane of the interface, click Generate Edge SubscriptionFiles , as shown in the figure below.
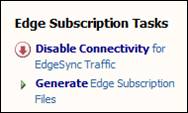
Figure 1
Your above action will bring up the Browse For Folder dialog box. Create a new folder called SubFiles , using the Make New Folder button. Click OK after creating a new folder on the C: drive.
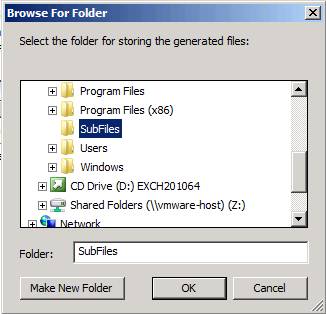
Figure 2
If everything works properly, you will see a dialog box that says 1 Edge Subscription file (s) was created in directory C: SubFiles. , as shown in the image below.
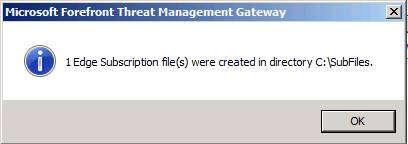
Figure 3
If you open the file, you'll see something like the one shown in the image below. You can see the file is saved as clear text, so make sure that after importing these settings into the Hub Transport Server, you need to delete the file immediately. Failure to do this may lead to some malicious problems if an intruder can access the file. You also need to know that the subscription file is only good for 24 hours. If you do not use it before the timeout time, you need to create another request.
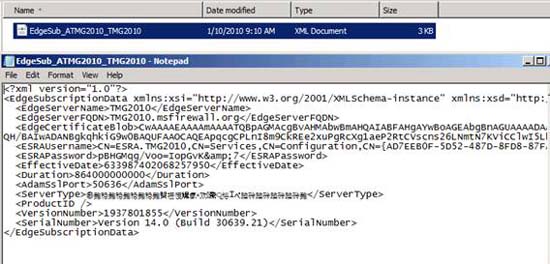
Figure 4
Now copy the file to the Exchange Hub server. Since we only have one Exchange Server in our test network, we will copy it to that server. At Exchange Server, open Exchange Management Console and click Organization Configuration in the left pane. Click Hub Transport as shown in the figure below.
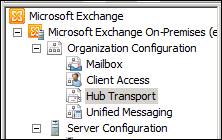
Figure 5
In the right pane of the console, click the New Edge Subscription link , as shown in the figure below.
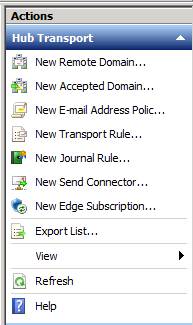
Figure 6
This will bring up the New Edge Subscription page. Click the Browse button in the Active Directory site section of this page. You will see the Select Active Directory Site dialog box appear. Select Default-Site-Site-Name and click OK .
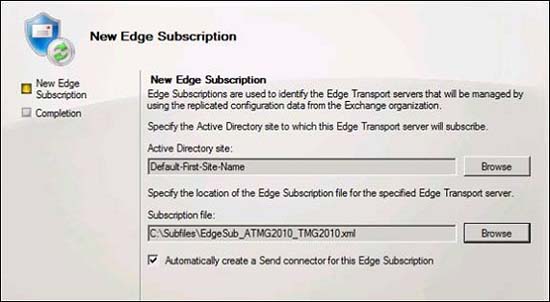 Figure 7
Figure 7After the wizard is complete, you will see what is shown in the picture below. Note that there is a warning:
EdgeSync requires that the Transport Hub servers print in Active Directory site msfirewall.org/Configuration/Sites/Default-First-Site-Name be able to resolve the IP address for TMG2010.msfirewall.org, and be able to connect to that host trên cổng 50636
We always have to create name identification and this is another example of how important DNS is to the TMG firewall scenario.
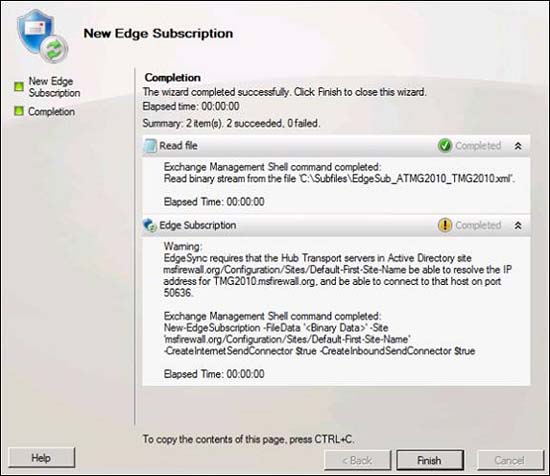
Figure 8
Check if the system policy supports email communication
When you configure the TMG firewall as an email security gateway, the program automatically configures some of the settings in System Policy. In the figure below, you can see that three System Policy Rules have been created to allow SMTP communication:
- Allow SMTP from Forefront TMG to trusted servers
- Allow SMTP traffic to the local host to filter and protect mail
- Allow SMTP traffic to Internet to filter mail protection
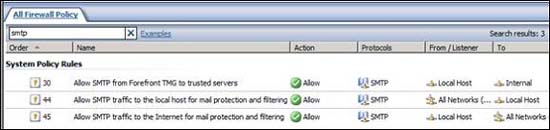
Figure 9
When you enable EdgeSync traffic, you will see the System Policy Rule created to allow EdgeSync traffic. This is Allow LDAP / LDAPS traffic to the local host for the Exchange Server EdgeSync Protocol . In the picture below, you will see Protocol Definition allowing TCP port 50636 to be sent.
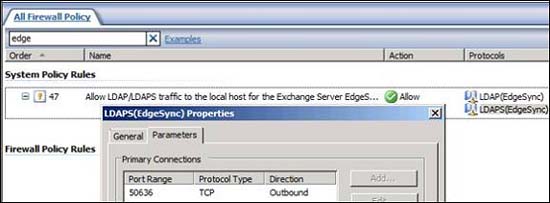
Figure 10
Now what happens if we send a clean email through the firewall? Here is the log file entry for such an email:
TCP2 / 28/2010 8:57:43 AM 10.0.0.1 10.0.0.3 25 SMTP Closed Connection Inspected [System] Allow SMTP from Forefront TMG to trusted servers 0x80074e20 FWX_E_GRACEFUL_SHUTDOWN Local Host Internal - TMG2010RTMB - Firewall
We highlighted the fact that this connection was exposed by the Network Inspection System. The SMTP filter is no longer used in TMG when using integrated email protection features. Instead, you will benefit from NIS, Exchange Edge and Forefront Protection for Exchange (FPE). The end result is a safer email protection configuration than what you can get with just one SMTP filter.
The next test will be to send some malware to Exchange Server through the TMG firewall. With this test, we used the previous test file that you downloaded from here. We have found that log files are not really interesting for processing test files, details you can see in the picture below.
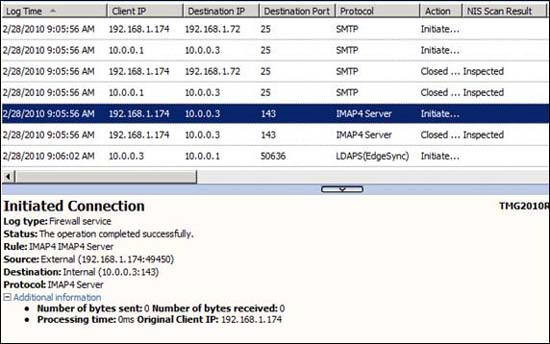
Figure 11
In fact, we have not found any information regarding SMTP logs. Checking on TechNet you can find a fairly comprehensive article on how this email protection feature works here, but the article does not mention how to find information recorded for malware. detected. In addition, the FPE interface does not reveal when you install email protection on TMG, so you cannot check the malware information found here.
However, if you check the email message, you will see that TMG has done what it is intended to do.
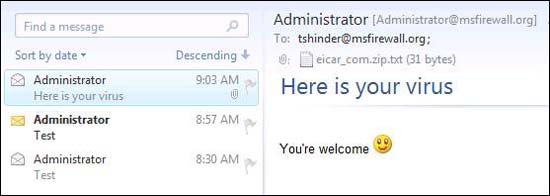
Figure 12
If you open the file eicar_com.zip.txt , you will see the following:
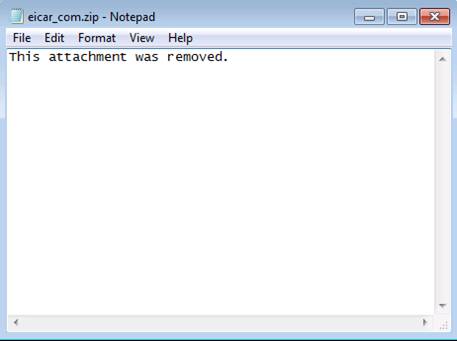
Figure 13
Admittedly there is nothing interesting, but remember that you can customize this message by activating the notification feature, as shown in the image below.
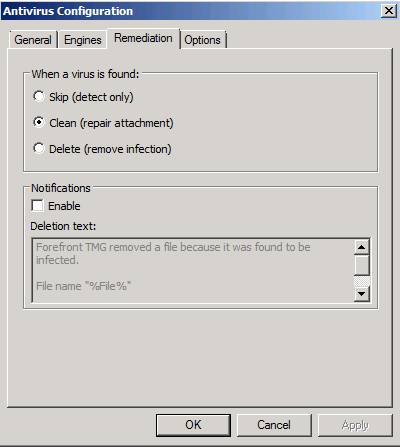
Figure 14
Conclude
In the final part of this article series, I showed you how to configure EdgeSync feature by creating a file on the TMG firewall and then using this file to automatically configure Exchange Hub server for receiving. and keep the mail in and go through the TMG firewall.
You should read it
- ★ Install and configure the solution to handle email on TMG 2010 Firewall - Part 1: Installation
- ★ Install and configure email handling solutions on TMG 2010 Firewall - Part 2: E-Mail Policy
- ★ What is a firewall? General knowledge about Firewall
- ★ Routing and filtering network traffic - Part 2: Windows Firewall
- ★ How to turn firewall (Firewall) on Win 7