How to detect strangers opening your computer
Detecting strangers using your computer when you are not around will help you manage your computer more effectively. To do this, follow these steps.
Instructions for detecting strangers opening your computer
Step 1 : Go to Start , type Gpedit.msc in the search box, then press Enter
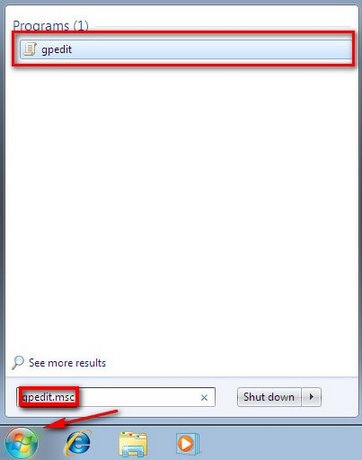
Step 2 : The Local Group Policy Editor windowwill open. Access the path: Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy.
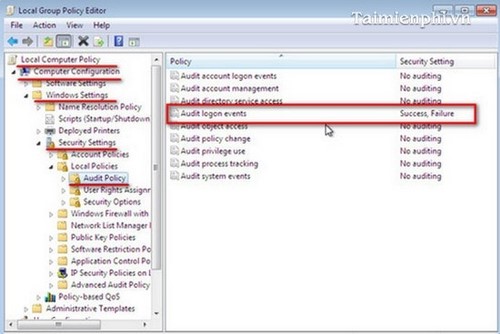
- In the Policy frame on the right, select Audit logon Events
Step 3 : In the Audit logon events Properties window, in the Local Security Setting tab , select both Success and Failure in the Audit these attempts section . Click OK to save the changes.
- From now on, Windows will record all login sessions to the system, whether successful or not.
Step 4 : Check login sessions
- Go to Start , type Event Viewer in the search box , press Enter
- In the Event Viewer window , access the path Event Viewer (Local) > Windows Logs > Security
- Event ID 4624 indicates that Windows has logged the login sessions into the system. Accessing it will tell you the login time and whether it was successful or not.
After setting up your computer following the steps above, you can control who can access and use your computer when you are away, helping you manage your children effectively. In addition, you should set a password to prevent strangers from accessing your computer. Whether you are using Windows 7, 8 or 10, you can set a password. Refer to how to set a password for Windows 7 or Windows 10 if needed.
You should read it
- Science reveals 5 simple ways of detecting lies
- British researchers train dogs to detect signs of a Covid-19 infected person
- FBI agent shared 8 ways to detect liars
- Detect 2 serious security holes in the Zoom application
- How to Detect Remotely Accessed Computers
- Marvel the instruments to detect enemy aircraft before the radar
- How to detect keyloggers on smartphones
- Adobe uses machine learning to detect photos with Photoshop
- 10 ways to detect and eradicate computer viruses
- Ways to detect hidden cameras in motels and hotels
- Tips to detect spyware stealing information on the phone
- 7 ways to fix Windows not detecting microphone error
Maybe you are interested
Free Lorenz ransomware decryption tool helps victims recover stolen data The surprising relationship between climate change - birth rate and consequences How to use Wandriver to update computer drivers Acer wants to lower the price of Ultrabook to compete with the iPad How to encrypt files on Windows using Simple Encryptor Google reinforced Google Drive data protection encryption
