How to check the extension using J2TEAM Extension Checker
Bank account hijacking, Gmail, Facebook, . most recently occurred because users accidentally installed fake extensions, containing malware to attack the system and steal personal information. Therefore, it is necessary to thoroughly examine the extensions before installing, especially check if the extension contains malware.
In response to this situation, the J2TEAM team released a tool to assist in scanning the extensions installed on the system, called Extension Checker. This tool provides two types of Desktop App that support checking on Windows and the extension installed from Chrome Store running Windows, Linux or Mac. The following article will guide you how to use J2TEAM Extension Checker in two different installation tools.
1. Chrome Extension Checker:
This is J2TEAM's Desktop App installed on Windows that checks the reliability of all the extensions you have installed on your computer.
Step 1:
First, download Chrome Extension Checker according to the link below.
- https://github.com/J2TeaM/chrome-extension-checker/releases/tag/v1.0.2
We will download Chrome Extension Checker as .rar to the computer.

Step 2:
Next, users will proceed to extract the downloaded tool file .
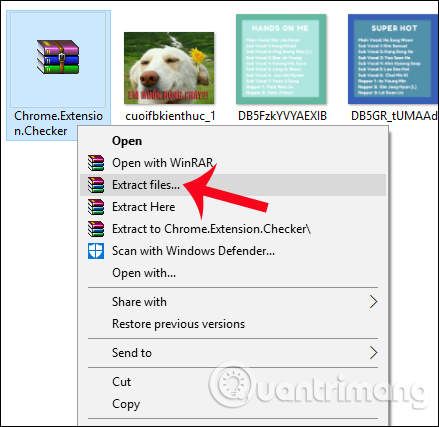
Step 3:
After the extract is complete, click on the Chrome Extension Checker tool to launch the program. The interface of Chrome Extension Checker will look like the image below. Above the Path to Extensions section will be the path of the default folder extension on the computer.
To conduct an extension scan, press the Start button.
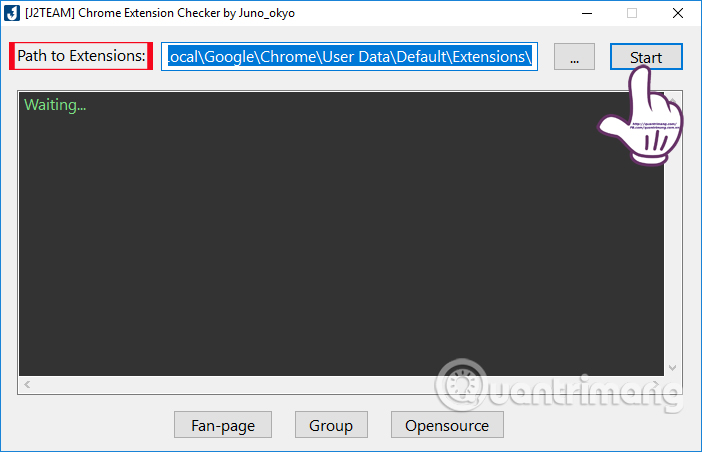
The result will immediately appear. If you receive the OK message as shown, the extension is installing safely for the system. If you notice Malware Extension or Fake IDM Extension, then you need to check the extension and proceed to remove it from the system, then quickly change all personal online account passwords.

2. J2TEAM Extension Checker utility:
This utility will support more diverse than the above tool, because it can be installed directly from Chrome Store, running on Windows, Mac or Linux. In addition, the scanning speed of this utility is fast, especially allowing removal if a dangerous extension is found with just one click.
Step 1:
To download the J2TEAM Extension Checker utility, click on the link below.
- Download the J2TEAM Extension Checker utility
Step 2:
Then click the Add to Chrome button to install the extension.
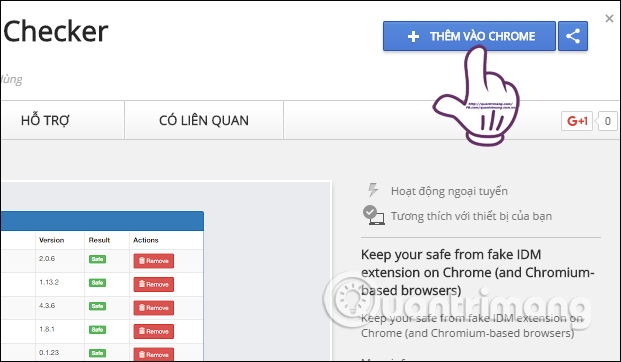
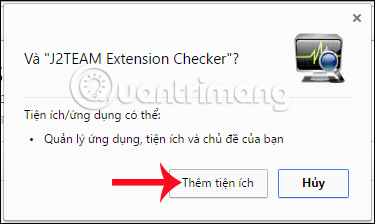
Finally click Add utility to complete the installation.
Step 3:
To test the entire installation utility on the browser, click on the J2TEAM Extension Checker icon at the bottom of the access bar to the website address.

Step 4:
A list of extensions currently installed on the system, along with the safety or danger status that the J2TEAM Extension Checker utility checks, in the Result column. Each add-on will include the latest version in use.
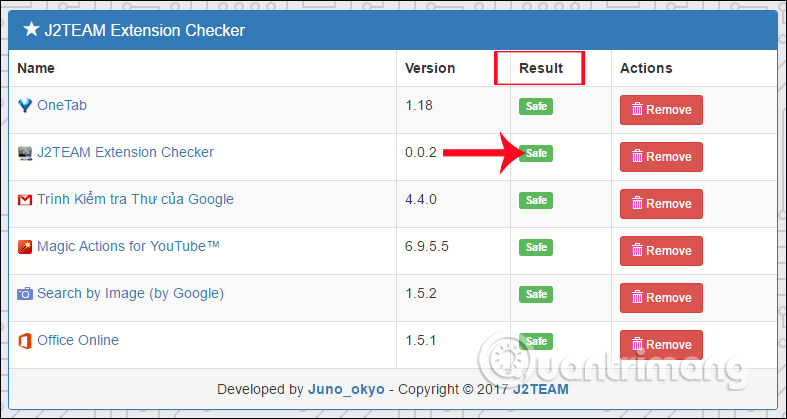
If you receive dangerous results for the system, users can proceed to remove the extension, click the Remove button. Click Delete to remove the utility on the system.

So with the Extension Checker utility from J2TEAM, we will know where the extension is safe for the system. From there, it is possible to quickly remove dangerous utilities, prevent the impact of sticks to the system.
Hope the above article is useful to you!