How to Open a Gate
Open the firewall port on the router

Find the router's IP address. You need your router's IP address to access the router configuration page.
Windows - Open Start , click the Settings wheel , click Network & Internet, click View your network properties , and view the address in the "Default gateway" field.
Mac - Open the Apple menu , click System Preferences > Network > Advanced > TCP/IP , and look for the "Router:" field. .
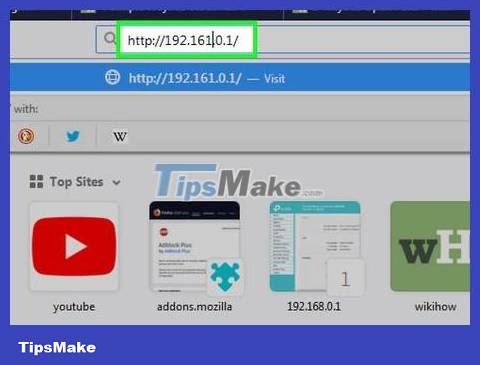
Go to the router setup page. Open a web browser and enter the router's IP address in the address bar.

Enter username and password. If you have configured your router's security, enter the username and password you set yourself. If not, consult the instructions that came with your router or online for the root username and password.
If you forget your login information, you may need to factory reset your router.

Find the Port Forwarding section. Since each router arranges its configuration page differently, look for these options (or variations thereof):
Port Forwarding
Applications _
Gaming (Game)
Virtual Servers (Virtual Servers)
Firewall _
Protected Setup
You can find Advanced Settings .
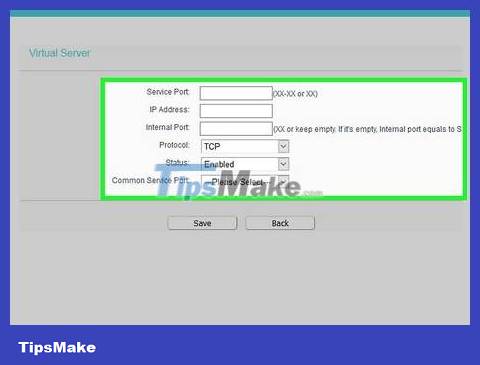
Open the port you want. Each router has a different way of doing things, although the necessary information is the same:
Name or Description - Enter the name of the application.
Type or Service Type - This can be TCP, UDP or both. If you're not sure which one to choose, click Both or TCP/UDP .
Inbound or Start - Here you enter the port number. If you have multiple ports open, enter the highest number.
Private or End - Retype the port number here. If you have multiple ports open, enter the highest number.

Luigi Oppido
Computer Repair Technician & Owner, Pleasure Point Computers
Luigi Oppido is the owner and operator of Pleasure Point Computers in Santa Cruz, CA. He has more than 25 years of experience in general computer repair, data recovery, virus removal and upgrades.

Luigi Oppido
Computer Repair Technician & Owner, Pleasure Point Computers
Expert warning: When opening a port, make sure you don't open a standard remote monitoring port that someone else could use to attack your computer. For example, ports numbered 80 and 85 are almost always blocked on routers, as they are often remote ports and an easy means for hackers to get into your network.
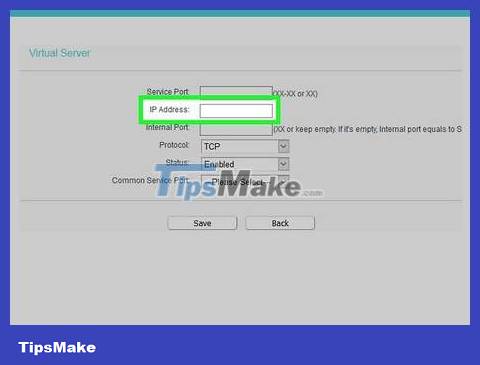
Enter your computer's private IP address. Enter in the "Private IP" or "Device IP" field. You can find the IP address of your PC or Mac.
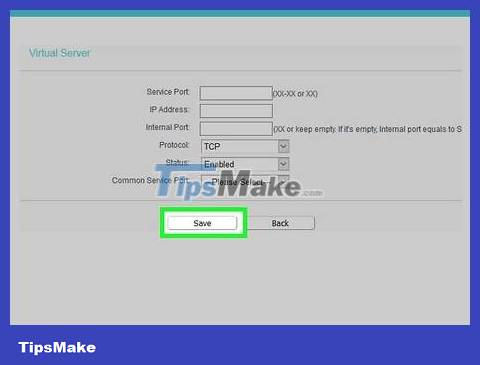
Save settings. Click the Save or Apply button . If required, you need to restart the router to apply the changes.
You can now check the "Enabled" or "On" box next to the forwarding port.
Open the Windows firewall port

Open Start . Click on the Windows logo in the lower left corner of the screen.
Type windows firewall with advanced security(windows firewall with advanced security) into Start. This is the operation to search for the firewall installation program on the computer.
Click on Windows Firewall with Advanced Security . You'll see the program at the top of the Start window.

Enter your password if requested. If you are not the administrator of this computer, you will need to enter the administrator password to continue.
Click on Inbound Rules . This item is located in the upper left corner of the window.
Click New Rule . You will see this option on the right side of the window.
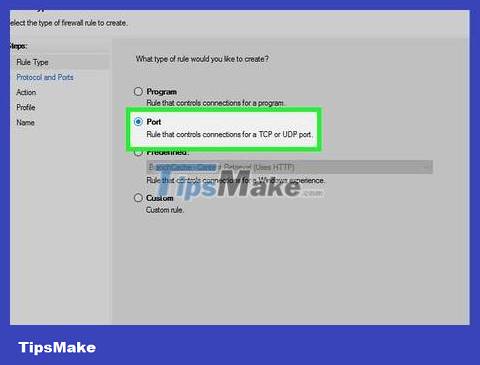
Check the "Port" option, then click Next . You can choose the port you want to open.
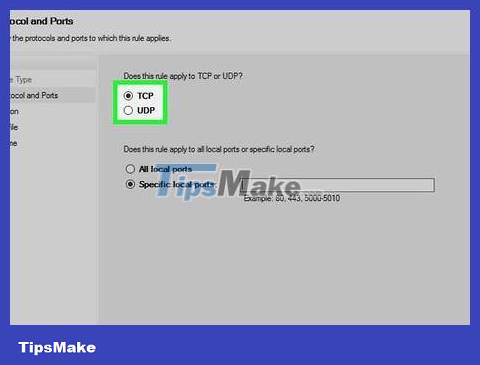
Select TCP or UDP. Check the TCP or UDP dialog box . Unlike on most routers, you need to choose between TCP or UDP to create rules.
Check your program's support documentation to make sure you're using the correct protocol.
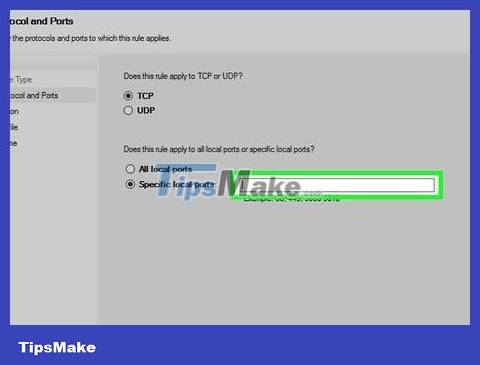
Enter the port range. Don't forget to select "Specific local ports" then enter the port you want to open in the dso field. You can enter multiple individual ports by using dots, or enter a series of ports by using a dash between the two ends of the range.
For example, you can enter 8830to open port 8830, 8830, 8824to open ports 8830 and 8824, or 8830-8835to open ports 8830 through 8835.
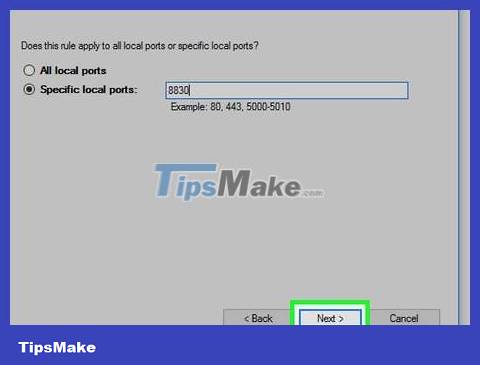
Click Next . This button is at the bottom of the window.
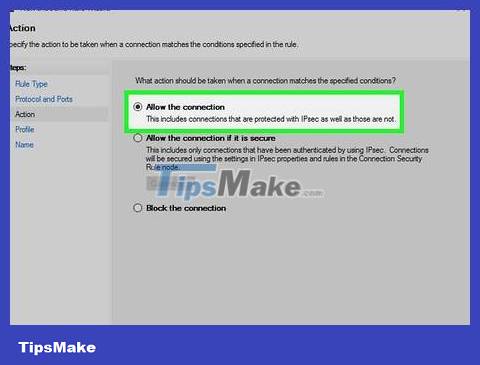
Don't forget to check "Allow the connection" then click the Next button . If this option is not checked, click on the dialog box before continuing.

Remember to check all 3 dialog boxes on the "Profile" page. Includes "Domain", "Private", and "Public" dialog boxes.
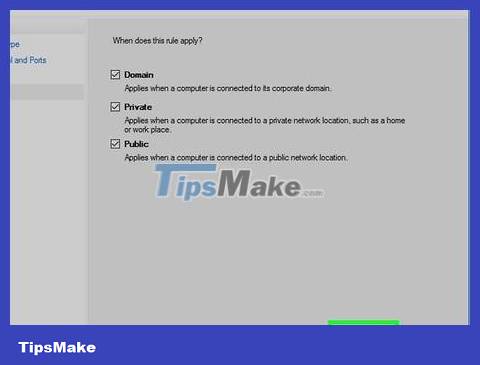
Click Next . The button is at the bottom of the screen.
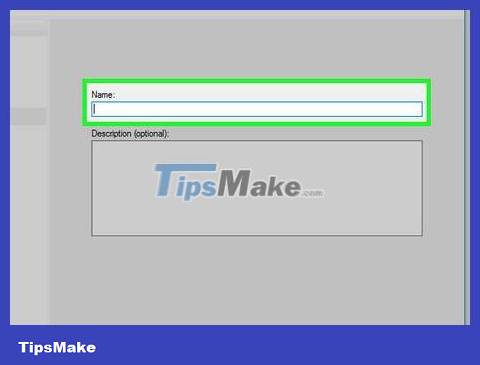
Enter a name for the rule, then click Finish . This saves the settings and opens the port.
Allow Apps on Mac

Open the Apple menu. Click on the Apple logo in the upper left corner of the screen.
Remember, by default, the Mac firewall is disabled. If you do not have a firewall enabled, this process is not necessary.
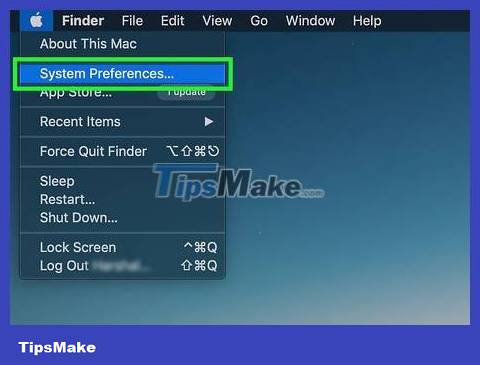
Click System Preferences . It's in the Apple drop-down menu.
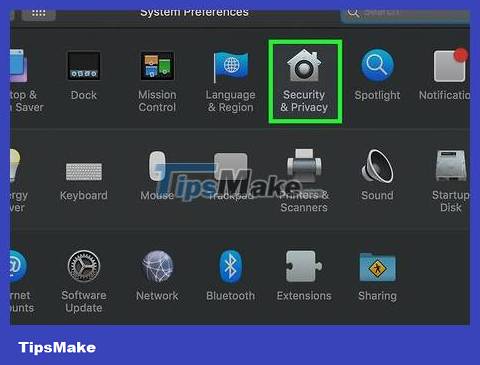
Click on Security & Privacy . This option has a house icon at the top of the System Preferences window.

Click the Firewall tab . This tab is located at the top of the Security & Privacy window.

Unlock the Firewall menu. Click the padlock icon, enter your Mac administrator password, and click Unlock .
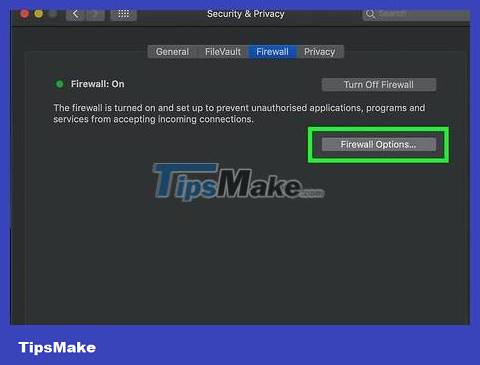
Click Firewall Options . Located on the right side of the Firewall page.
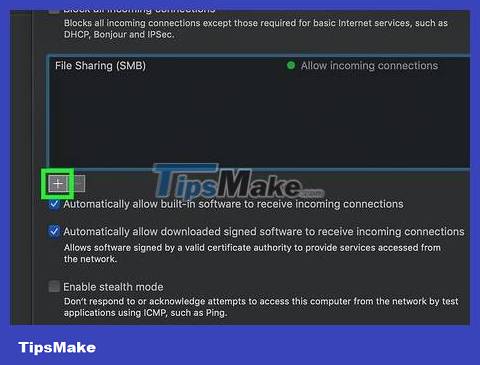
Click the + button . You'll see the option below the window, in the center of the page.
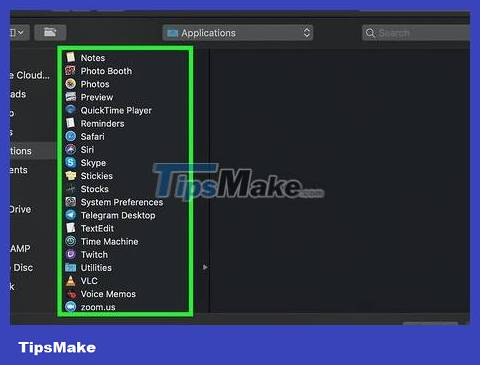
Select applications that allow bypassing firewalls. You just need to click on the application to select it.

Click Add . This button is near the bottom of the window. This will add the program to the firewall's exceptions list.
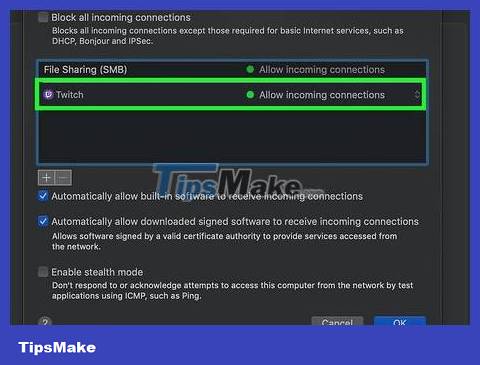
Don't forget to check the "Allow incoming connections" box displayed next to the application name. If you don't see this dialog box to the right of the application name, hold down Controland click on the application name, then check Allow incoming connections .
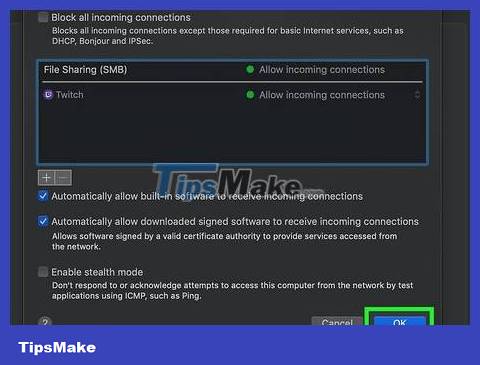
Click OK . This saves the settings and allows the application to bypass the firewall.