Configure advanced firewall in Windows Server 2008 using the MMC snap-in
David Davis
Since its inception, the Windows Server 2003 SP1 firewall has become the basic and necessary option for servers although it only blocks incoming attacks. In Windows Server 2008, the preinstalled firewall has been greatly upgraded. Let's explore the new functions and how to configure the new firewall using the MMC snap-in.
The reason to use a firewall for Windows base server
Today, many network security companies use "outside / subjective precautions" inside. They set up a fence to cover the network with firewalls and IPS systems to avoid any malicious attacks on the Internet. However, if an attacker has the ability to penetrate external barriers and continue to attack the intranet, only the Windows authentication authority can stop further intrusion into the data. important.
This is because most IT corporations do not secure their networks with server firewalls. Why is that? We see that server firewalls are becoming "more and more problematic than reality".
After reading this article, I hope that many of you will be more concerned with the Windows server firewall. With Windows Server 2008, the firewall is integrated and preinstalled in Windows with many functions and much easier to configure. A firewall is really the best way to secure an important base server. So what are the benefits for Windows Server Advanced firewall? Let me find out.
Help from the new advanced firewall
The new built-in firewall for Windows Server 2008 is now an 'advanced' firewall. This 'advanced' version is called Microsoft 'Windows Firewall with Advanced Security' (WFAS for short).
New function:
- New GUI interface - The MMC snap-in is available to configure the firewall.
- Bi-directional - Filters traffic in and out.
- Works better with IPSEC - The rules of firewalls and IPSec encryption configurations have been integrated together.
- Advanced Rules configuration - You can set rules for Windows Active Directory (AD) accounts, groups, and destinations for dynamic IP addresses, protocol numbers, sources, and destinations for TCP / UDP ports , ICMP, IPv6, and Windows Server interface.
With the addition of firewall filters, a nice interface and advanced configuration, Windows Advanced firewall is gradually becoming a firewall for traditional base servers (such as ZoneAlarm Pro).
Often the first point of concern for any network administrator using a basic server firewall is: What happens if it affects the performance of server infrastructure applications? This is always a possibility for any security method, WFAS will automatically configure new rules for each new feature added on the server. However, if you start any network connection application that does not belong to Microsoft on the server, you will have to create a new rule yourself.
When using a firewall for highly configurable operating systems, you can better protect the server from attack and fully capture the in / out traffic on the server.
Configuration options for Windows Firewall with Advanced Security?
Previously, on the server operating system you could set up a firewall when configuring the network adapter or from the control panel. The configuration job is very simple.
With Windows Firewall with Advanced Security (WFAS), most administrators will configure the firewall from Windows Server Manager or from MMC with just a WFAS snap-in. Both ways come to the following result:
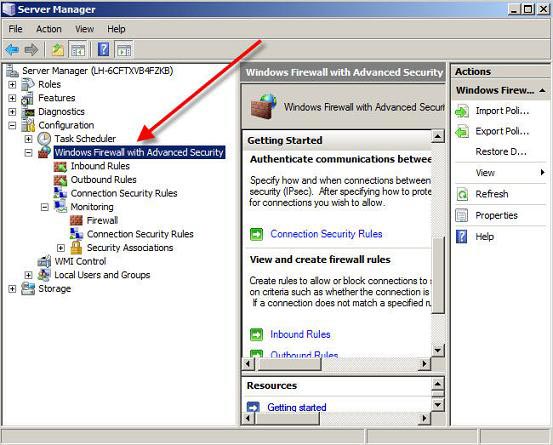
Figure 1: Managing Windows 2008 Server

Figure 2: Windows 2008 Firewall with Advanced Security
The easiest and fastest way to start WFAS MMC is to type from the firewall in the Start bar at the Search menu, as follows:

Figure 3: Windows 2008 Firewall with Advanced Security
How to configure the WFAS MMC snap-in?
There are many features to be able to configure the WFAS MMC snap-in that I can't list all here. If you have ever seen the configuration of the user interface (GUI) of Windows 2003 built-in firewall, you will immediately see how many options will appear with WFAS. However I will list some of the most typical options.
By default, when you open the WFAS MMC snap-in, you see that WFAS is turned on and the internal block connections do not correspond to the outside. Moreover, the external firewall is not activated.
You also note that WFAS has other information (see Figure 4).
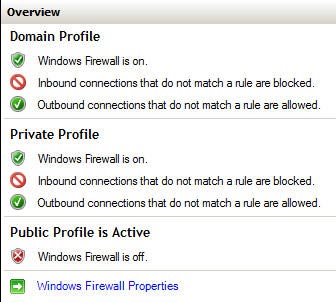
Figure 4: Information displayed by Windows 2008 Firewall with Advanced Security.
WFAS includes domain information, personal information and general information. These different information allow you to set up a lot of internal and external rules so you can apply those firewall rules to your computer when you connect to the network.
Regardless of the outstanding features of WFAS that we know above, my personal difference is the complex security rules. See the option to add the rules of the Windows 2003 Server firewall in Figure 5.
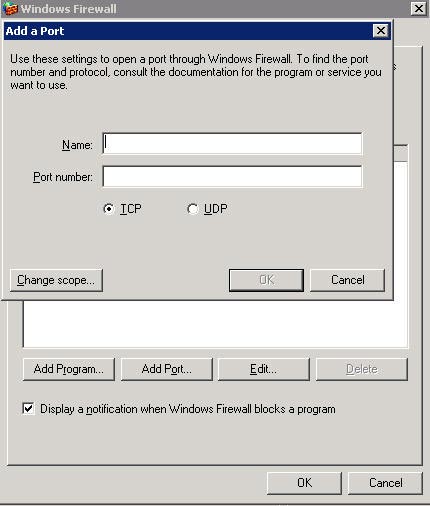
Figure 5: Windows 2003 Server Firewall Exception window
Compare it with Windows 2008 Server:
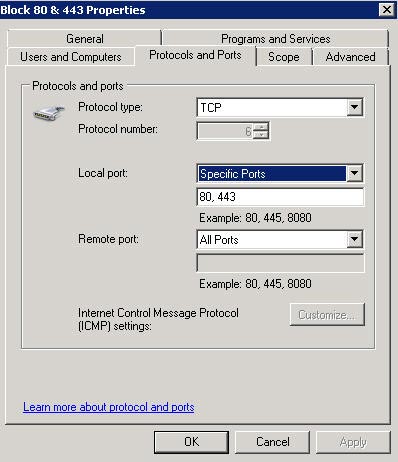
Figure 6: Windows 2008 Server Advanced Firewall Exception window
Note that the Protocols and Ports tab takes up a small portion of the window with many different tabs. You can also configure options for Users & Computers, Programs and Services, and IP address Scopes. With this configuration, Microsoft developed WFAS much better than Microsoft's IAS server.
The number of WFAS default options is amazing. In Windows 2003 Server there are 3 default rules. Unlike in Windows Server. WFAS provides about 900 defaults for internal firewalls and at least 40 defaults for external firewalls.

Figure 7: Default rules for the internal firewall of Windows 2008 Server Advanced Firewall
Create a custom protected firewall rule in
Follow these steps to create a rule in Windows Advanced Firewall.
You have installed Apache web server for Windows on Windows 2008 Server. If you already use IIS installed on Windows, this port will automatically open. But if you are using a third-party web server and have an internal firewall enabled, you must open the port yourself.
Here are the steps to take:
- Identify the protocol you want to filter - can be TCP / IP protocol (as opposed to UDP / IP or ICMP protocol)
- Identify the source IP address, source port, destination IP address and destination port - Intrusion is likely to come from any IP address and at any port, enter the server through port 80. ( Note that you can also create rules for a certain program like apache HTTP Server).
- Open Windows Firewall with Advanced Security MMC
- Adding Rules - Click the New Rule button in Windows Firewall with Advanced Security MMC to open the New Inbound Rule Wizard table
Figure 8: New rule creation button of Windows 2008 Server Advanced Firewall MMC
- Select the type of rule you want to create for a port.
- Configure the protocol and port number - to default to TCP then enter the port number eg 80 and then click the Next button.
- Leave the default 'allow this connection' and click Next.
- To default, apply this rule to all profiles and click Next.
- Name and click the Finish button.
You get the following result:
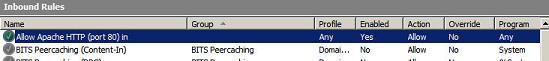
Figure 9: Windows 2008 Server Advanced Firewall MMC after it has been set up
I learned that installing a new Apache web server will not work when only installed with an active firewall. But after this rule, it will work normally.
Conclude
During the development process, along with complex configuration rules and 30 times the default rule compared to previous versions, the Windows 2008 Server firewall is actually the right name for the 'advanced' firewall like Microsoft confirmed. I believe that with this free, pre-installed firewall on the base server, Windows servers will also be more secure in the future. It is not safe unless your server uses a firewall. Therefore, I hope that you will try to use this new Windows Advanced Firewall feature.
You should read it
- ★ Configure advanced firewall in Windows 2008 using NETSH CLI
- ★ Overview of Windows Server 2008 Firewall with advanced security features - Part 3
- ★ What is a firewall? General knowledge about Firewall
- ★ Overview of Windows Server 2008 Firewall with advanced security features - Part 2
- ★ Overview of Windows Server 2008 Firewall with advanced security features (continued part 3)