Want to secure your Google account? Do not ignore the following!
With a Google account in hand, we can use many other services with huge amounts of data such as sending Gmail email, online Google Data storage, image storage with Google Photos , . If your Google account accidentally falls into the hands of others, which means that all the information and data in the above service applications will also be overlooked.
Therefore, the protection of all personal information on Google accounts is necessary to avoid situations of hacked accounts. And big Google also offers many solutions, to increase user account security. Here are 4 methods to limit your ability to hack Google accounts.
1. Restore Google account:
The first thing that we introduce to you is the option to restore the system. With this setting, we can avoid the account being hacked and quickly restore the personal account.
Step 1:
At the Google interface, click on My Account (My Account).

Step 2:
At My Account interface, click on Login and Security (Sign-in & Security).

Step 3:
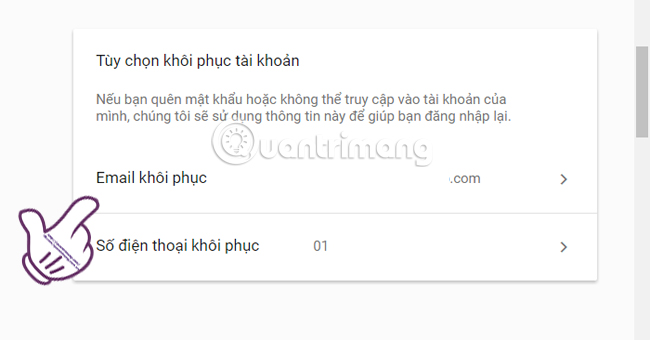
At Login and security interface, we scroll down under Sign in into Google and find the Account recovery options (Account recovery options) section. Here, we proceed with the steps to set up email recovery (email recovery) and recovery phone number (recovery phone).
2. Activate 2-step Google account verification:
Two-layer verification is considered the best security method to protect personal accounts such as double-layer security for Facebook, secure two-layer Gmail, and with Google personal information you should also follow the steps This secret.
When a user activates 2-step verification will receive a password and a random code sent to the phone to access his account. This will prevent hackers from detecting passwords based on your information such as identification number, date of birth, home address, .
Step 1:
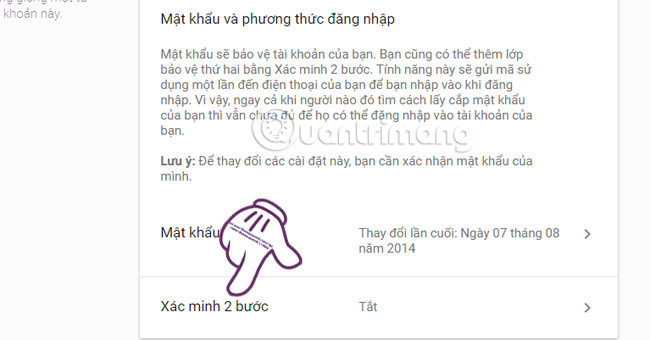
Also in the Login and security interface (Sign-in & Security). Scroll down to Sign in to Google (Singing into Google) and go to Password and sign-in method. Here, click on 2-Step Verification.
Step 2:
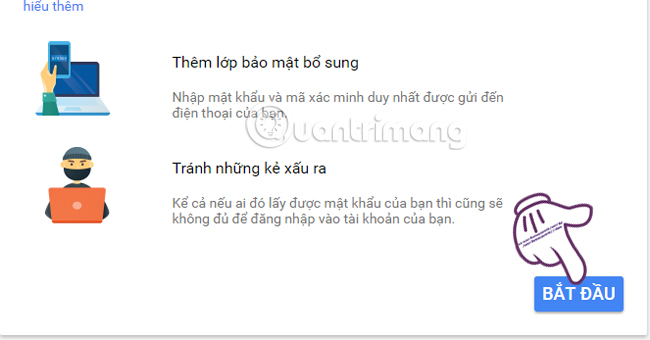
At the new interface, we choose Start .
Step 3:
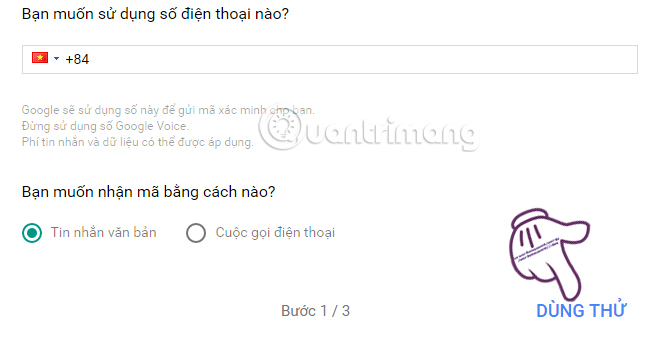
Next, we enter the phone number that is in normal use and choose the method of receiving the code in writing or phone. Then press Try .
Step 4:
Enter the Google code sent to your phone and click Next .
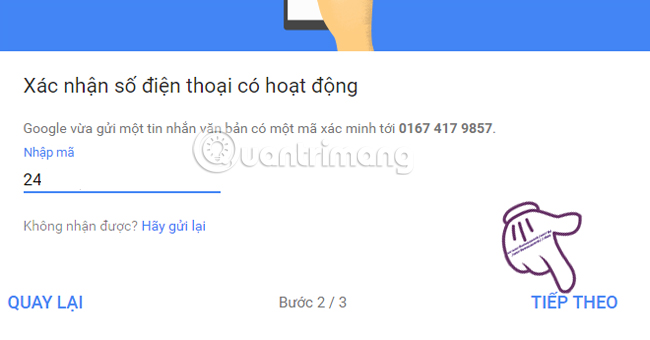
You will receive a 2-Step Verification message for the account. Click Enable to enable this feature.
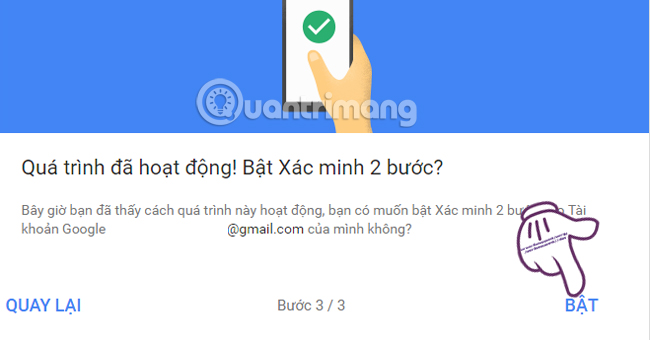
- See also Activating Google Prompt to improve 2-layer security
3. Disable Allow Less Secure Apps option:
When a third-party application identified by Google is unsafe, it will block it when trying to access your account. But what if we have to use that application?
In this case, you can enable the Allow unsafe applications (Allow Less Secure Apps) access to your personal Google account. However, more dangerous when we enable this feature, all less secure applications can access your account. Therefore, it is best to disable this option by following these steps:
Step 1:
At Google Sign-in & Security interface, select Applications and connected websites (Connected apps & sites).
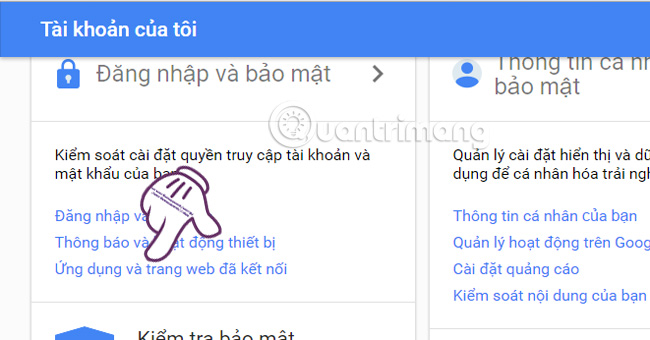
Step 2:
At this interface, scroll down and select Allow less secure applications (Allow Less Secure Apps) and push the horizontal bar to the left to turn off this mode.
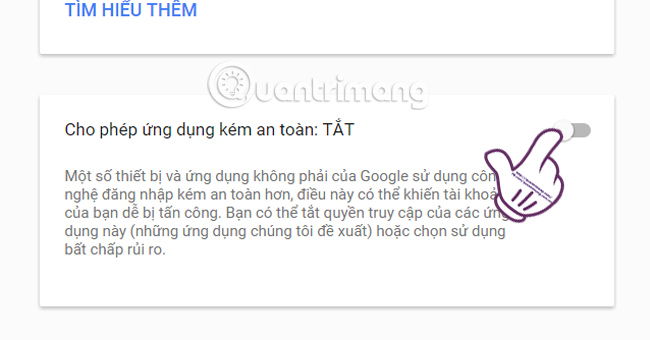
4. Check the security status of your account with Google Security Checkup:
Finally, you should check the overall security of everything with the Google Security Checkup option.
Step 1:
Click on the link below:
- https://security.google.com/settings/intro/security/secureaccount
If you have not logged in to your Google account, click Sign in to start to start. If you are logged in, you can use this feature right away.
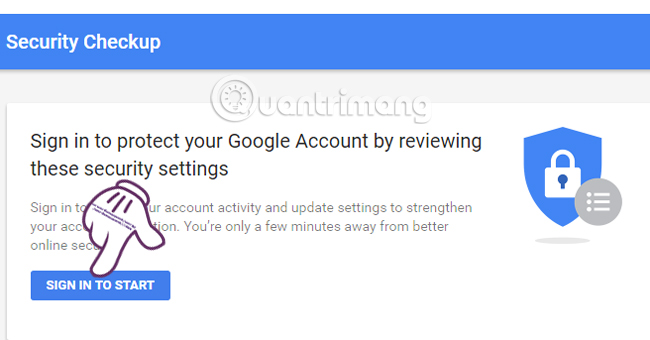
Step 2:
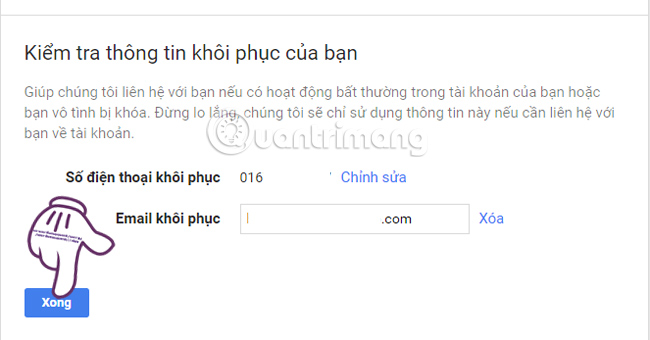
Next, you will proceed with the confirmation according to the 6 security content required by Google . You just need to confirm the information and click Done .
The above are 4 things that confirm and protect important Google information that you should not ignore. Best in the process of securing information on Google, you should use two-layer security and receive codes via phone to prevent the loss of personal account passwords.
Refer to the following articles:
- Fix Flash Plugin errors on Firefox and Coc Coc
- Instructions for fixing common errors in web browsers
- Fix errors not typing Vietnamese on Chrome
I wish you all success!
You should read it
- ★ Enable Google Prompt to improve 2-layer security
- ★ Google Account security guide with Google Authenticator
- ★ What is Google Authenticator? How to use Google Authenticator to secure your Google account
- ★ Google's new advanced security turn-on guide to not be hacked
- ★ How to log out of your Google account on devices