Google's new advanced security turn-on guide to not be hacked
When attacked by the network, it is not uncommon for you to panic. Google has many features to help secure your Google account, but if you're still unsure, use this new tool.
Google has just introduced the most powerful security feature ever, called Advanced Protection, to help users easily lock their Google accounts.
'We do this because a minority has not been focused when they are vulnerable to online attacks,' Google said. With this feature, even if hackers get your password in any way, they cannot access the account.
How to enable the Advanced Potection feature of Google
To use this feature, users need to have 2 security keys of FIDO Universal 2nd Factor (U2F) for 2-step authentication without using SMS or email. If you want to log in to your account on your computer or laptop, you will need a special USB, and on a tablet and a phone you need a Bluetooth dongle.
See also: How to secure your accounts with U2F security key?
Google Advanced Protection brings 3 features to ensure Google account security:
- Physical Security Key: Use the security code U2F to log in to the account, preventing others (even if they have a password) to log in.
- Limited access and data sharing: only allow Google applications to have immediate account access, while other applications are gradually added.
- Blocking account fraudsters: if U2F code is lost, the account recovery process will take a few more steps, including additional information about why the account is lost.

Advanced Protection has a more complex security process than usual
Advanced Protection is not for everyone but only for those who are easily targeted by hackers, such as journalists and government officials . and are willing to sacrifice convenience to be safe.
Currently, if you want to join Advanced Protection Program, you need Chrome because only Chrome supports U2F standard for Security Keys.
Google added ESET malware detection tool to Chrome
In partnership with ESET, Google also wants to expand the malware protection identifier in the browser through the Chrome Cleanup feature.
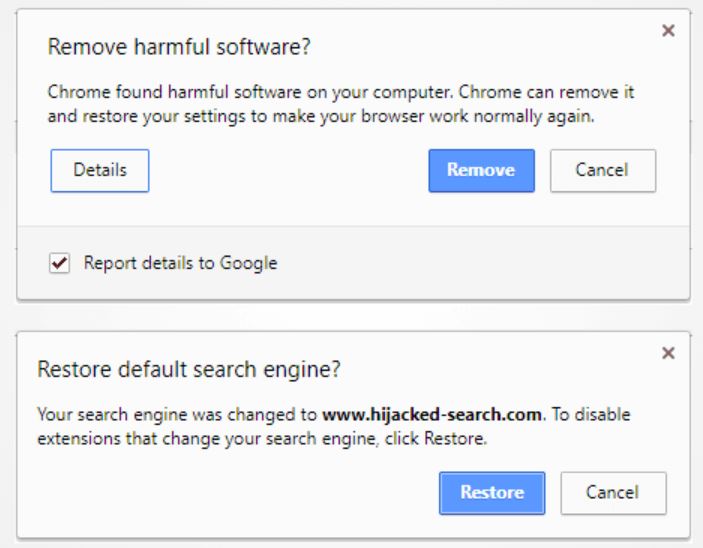
Chrome Cleanup combines ESET's malware detection engine with Chrome's sandbox technology
'We can now detect and remove unwanted software,' Google said. 'This engine is not the same as normal antivirus software but only removes software that is not compatible with our unwanted software policy'.
You can register for Google Advanced Protection here.http://g.co/advancedprotection