Reduce the attack side of administrator accounts
We have seen a new trend coming to the corporate network that network administrators want to limit what an 'administrator' account can do in a network environment. Not only administrators from Active Directory but also administrators on workstations and servers throughout the enterprise . There are quite a few configurations that we can do to limit them, in other words, to control these accounts. But the important thing is what to do, what configurations mean to you and what should not be done when it comes to admin accounts throughout the organization. Here, we will answer all those questions to make sure you can create the appropriate configuration and know what you can open.
Where are the admin accounts located?
Before starting to restrict admin accounts on the network, you need to understand where they are located and what privileges they have. First we have to start by looking at the workstations and servers in the organization. All computers running Windows have an administrator account configured at the installation. This account is the highest-level account you have on each computer. This account has membership in the admin group, granted the highest control on that computer.
There are also admin accounts configured in Active Directory. The first domain configured in your enterprise Active Directory has a special administrator account. The reason it is especially because of the groups it has membership in. This initial admin account has membership in the main security groups below:
- Administrators
- Domain Admins
- Enterprise Admins
- Schema Admins
The initial domain includes both the Enterprise Admins and Schema Admins groups. Each additional domain will have an administrator account as a member in the Domain Admins and Administrator groups
What can administrators do?
Now that we know where the admin accounts reside, what can they do? Local administrator accounts have full access on the computer that it exists in. That means they can change any resources on the computer such as services, accounts, resources, applications and files stored on the computer.
Administrator accounts in Active Directory have the same rights. When such accounts have control over the domain level or higher, they not only control the services, accounts, resources, applications and files stored in the domain controller, but also with any computer. Which in the corresponding domain. Administrators in the original Active Directory domain also have this power on each individual computer in the entire account network. And corporate governance can control all aspects of this account network.
Control of administrator accounts
As you can see, the administrator account has a lot of power. Therefore you need to protect this account. There are many options to reduce the risk associated with being attacked or compromised on this account. These suggestions may seem like extensive work, inefficient methods or concepts that can make you less productive. When considering any security concept you will have to have a certain plan. Security is not easy at all, if it is easy then we don't have to worry too much about it. So what do you have to do to protect administrator accounts in your environment?
First , do not use administrator accounts. These accounts should only be used to set up the initial environment, after setting up you need to include 'normal user accounts' into the administrator group or one of the members of the different administrative groups. . This will achieve the same results and do not need to use the 'real administrator account'.
Secondly , do not use the 'normal user account' set in Administrator or one of the other administrative groups periodically and standard user tasks. Check email, write memos, document references, etc. should be done with a standard user account without an administrator account. This requires a parallel account for administrators. An alternate solution to doing that is to use Vista with UAC enabled. At Vista, UAC is an ideal technology for solving this problem.
Third , disable the administrator account - Administrator. You can only do this with Windows XP and Server 2003, represented by a setting in the Group Policy Object, see Figure 1.
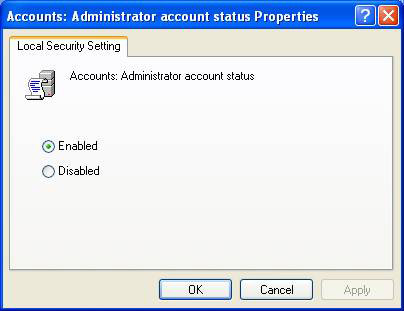
Figure 1: With Group Policy Object, you can disable any administrator account
I will have to give some warnings before you disable this account. First, you need to make sure you create another admin account before disabling this account. If you do not do this, you will lock yourself outside the system when creating an account of another administrator type. Next, you need to consider what will have to be done for recovery plans when a bad situation occurs. Without an administrator account, you may not have access to certain disaster recovery files, services, and tools.
Fourth , set up Active Directory and the delegated component of Group Policy instead of just throwing user accounts into the domain administrator group. In most cases, you can use the trust tool and techniques to give the administrator control over Active Directory and Group Policy. Figure 2 and Figure 3 show you the interface for trust control areas.
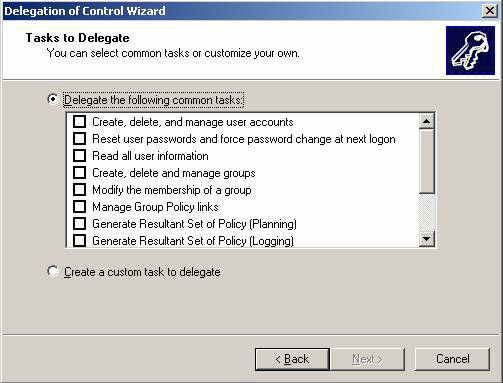
Figure 2: Entrusting Active Directory
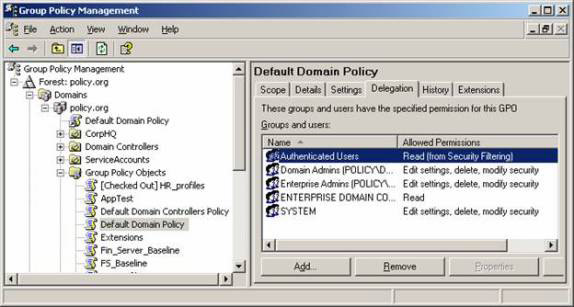
Figure 3: Trust Group Policy
Fifth , you should enable auditing of resources, where administrators do not have access, and should not accept their own access. What will have to be done is to help protect resources where administrators should not have direct access. This can be a smart solution for files related to HR, finance, governance, corporate shares, etc. Remember what we discussed in the previous section for managing accounts. other administrators and their access. An administrator who is not listed on a resource does not mean that they cannot add themselves. You can enable authentication on any computer using Group Policy as shown in Figure 4.
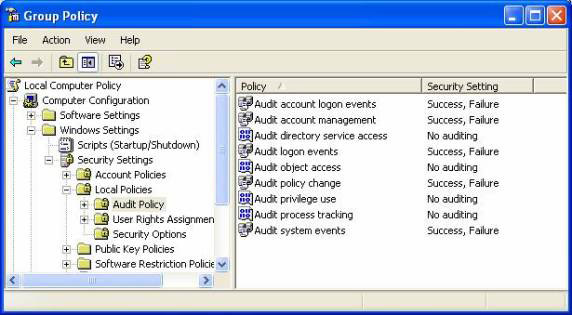
Figure 4: Verification to check the access of administrators
Sixth , the administrator accounts and all user accounts configured with administrator privileges need to have good password protection. Those passwords should also be changed often. Not giving the expiration date of the password will not be good for security here.
Finally , a trick to show you is not really a configuration or setup, but simply protecting the company and its resources with all possible costs. If there is a bad feeling about an administrator or someone with administrator rights, you must take measures against them, which can be strong enough to eliminate. It is really a difficult thing but if someone cannot trust them they must be replaced from your environment to ensure safety for the entire company.
Conclude
Administrators and administrative group accounts are very powerful in the Windows environment. These accounts have more power than what you often think about it. You can protect your environment means you have to strictly control those accounts. So you need to pay attention to all the attention that we have introduced to protect them, although some options may reduce efficiency and may generate many stages for all. administrator every time they want to perform a task that requires high access. But overall, to control administrator-type accounts, that's a necessity. You need to take this protective action immediately before your network is destroyed as in the case of 'losing a new cow to make a cage'!