Learn about MD5 code
If you download files with small capacity, short transmission time, there is not much error in the transmission process. However, for large files, the long transmission time is likely to fail during the file download process. So you need to check the MD5 code and compare it with the original MD5 code. So what is MD5 ?
1. What is MD5?
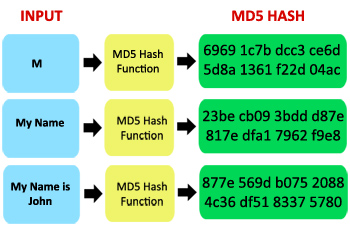
MD5 (short for Message- Digest algorithm 5 , message digest algorithm 5 ) is a cryptographic hash function according to RFC 1321 standard, has a 128bit hash value. MD5 was developed in 1991, by Professor Ronald L. Rivest to replace the previous MD4 hash function. MD5 is not a fast algorithm like MD4 algorithm , but data security on MD5 is more secure. MD5 is used in many security applications and to check the integrity of the data file, verify whether the file has been changed or not.
You can imagine, you have 2 datasets and need to compare whether they are completely the same, if there is no MD5, you will have to compare the raw data of those two datasets. MD5 does not do that, it creates a checksum on 2 datasets and compares this checksum to decide if the 2 data sets are the same.
Although safer than MD4, MD5 still has some security holes, so it is not useful for advanced encryption applications and is often used to check whether a file is standard or not.
2. History and vulnerability on MD5
MD5 is just one of three algorithms of Ronald Rivest. The first hash function created was MD2 in 1989, built for 8bit computers. Although MD2 is still in use, it is not for applications that need a high level of security, because it is very vulnerable to common hack types.
MD2 was later replaced by MD4 in 1990. MD4 was created for 32-bit machines and much faster than MD2. However, MD4 has some weaknesses and has been judged obsolete by the Internet Engineering Task Force.
MD5 was released in 1992 and also for 32-bit machines. MD5 is not as fast as MD4 but safer. MD5 still has security vulnerabilities and SHA-1 is proposed to replace this hash function.
Carnegie Mellon University is part of the Software Engineering Institute talking about MD5: "Software developers, Certification Authorities, website owners and users should avoid using MD5 algorithms whenever possible. Previous research has shown that MD5 can be broken in terms of encryption and not suitable for use ".
In 2008, MD6 was proposed to the National Institute of Standards and Technology as an alternative to SHA-3.
Explore more:
- How to convert PDF files to Word Online very fast
- How to open locked files in Office 2013
Good luck!
You should read it
- ★ Instructions for checking MD5 code when downloading files
- ★ Check MD5 and SHA1 to check file integrity
- ★ What is MD5, why check MD5
- ★ How to check the origin, where iPhone is manufactured through IMEI code, model
- ★ There is a generation of children who learn to write code before they can talk to people in India