Is Explorer.exe a virus?
What is Explorer.exe?
Explorer.exe is an operating system file. The explorer.exe process is commonly known as Windows Explorer and it is used to explore the graphical user interface of Windows, as well as display the files of the hard drive.
This is an application window that launches and allows the user to navigate the contents of folders, as well as view file information. Explorer.exe belongs to Microsoft Windows operating system software and is developed by Microsoft Corporation.
 Explorer.exe is an operating system file
Explorer.exe is an operating system file The file explorer.exe size ranges from 1,0321,292 bytes to 3,194,368 bytes. Cybercriminals write a malware program and named it explorer.exe to spread via the Internet.
- Affected platform : Windows operating system
How to see if the system is affected by the explorer.exe malware?
Explorer.exe is a Windows file and is stored in C: Windows. If you suspect that the system is affected by explorer.exe, then check its location by going to the task manager. This can be done by pressing the CTRL+ DEL+ key combination ALT, then right-clicking on the file explorer.exe and selecting the option to open the location.
If you find it in C: / Windows then the system is not affected. Conversely, if the file is located in a different location, then the system has been affected by the virus. If you find more than 6 processes running in your task manager and use a lot of CPU, then you can conclude that the system has been affected by the virus.
How to remove explorer.exe
In case explorer.exe is a malware designed to hide on your computer, by masquerading as the Internet Explorer folder, it should be removed from your computer as quickly as possible. If not, virus files can wreak havoc on your system by damaging important files in Microsoft Windows. How to remove explorer.exe is as follows:
Step 1 : Click the Start buttonin the lower left corner of the screen. From the menu that appears, click Run. A small search window with a single search bar will appear.
Step 2 : Enter Regedit to open the Windows Registry Editor.
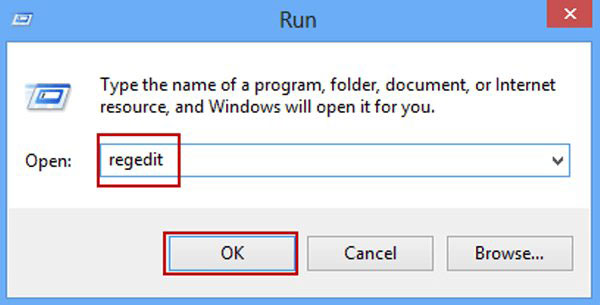 Open Windows Registry Editor
Open Windows Registry Editor Step 3 : Select the folder HKEY_LOCAL_MACHINE. A series of other program files will appear.
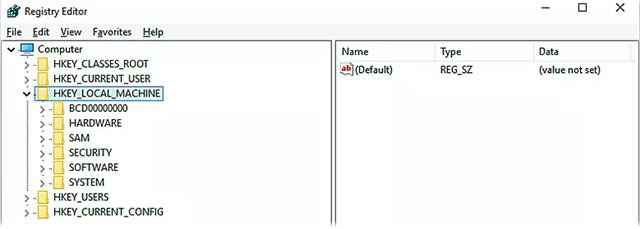 Select the folder HKEY_LOCAL_MACHINE
Select the folder HKEY_LOCAL_MACHINE Step 4 : Open the Software folder > Microsoft> Windows> CurrentVersion> Run> IEXPLORER "="% System and select iexplorer.exe.
Step 5: Click the Delete buttonand you will be asked if you are sure you want to delete the file. Click on OK.
Step 6 : Open the file HKEY_CURRENT_USER > Software and delete the mmtest folder .
Step 7 : Close the Registry Editor and restart the computer.