How to uninstall Chromium Malware with 4 easy steps
Program developers easily bundle their software with adware to earn extra money. If you don't pay attention, you may end up paying more for installing new software, because malware is pre-packaged.
Chromium malware is a popular option for fake developers. Chromium malware may look almost like a real package. But don't be fooled! You need to remove it if you want your PC to be safe. Learn how to uninstall Chromium malware with the following 4 easy steps!
What is Chromium Malware? How to uninstall it?
- What is Chromium malware?
- How to uninstall Chromium malware
- Step 1: End the running processes and try uninstalling
- Step 2: Start scanning malware thoroughly
- Step 3: Delete the Chromium user data directory
- Step 4: Reset the standard Chrome settings
What is Chromium malware?
Chromium is Google's open source browser project, used as a Google Chrome platform. Chromium malware is named after the project because malicious developers use that code to create fake Chrome web browsers.
They will have their own names (like BeagleBrowser and BoBrowser) but look outside will be very similar to Chrome. There are other legitimate Chromium browsers that you can install, but these fake browsers aren't. They are not designed to benefit end users.
If you're a new Windows user, you may not even notice something has happened. Chromium malware may also infect settings in other browsers or infect your own Chrome installation through third-party spoofing extensions.
You may accidentally install these browsers (or malicious extensions) from your browser's pop-up window or they may be pre-packaged with other software.
How to uninstall Chromium malware
Step 1: End the running processes and try uninstalling
Before starting to learn how to remove Chromium malware, you will need to check that the software is not running. Some malware is 'stubborn' and can continue to run in the background, when you close it. These malware are designed to prevent you from being uninstalled.
Open the task manager on Windows PC by pressing Ctrl + Shift + Esc . You will see a list of running processes and open applications. Search for anything called Chromium or Chrome.
Select unwanted progress and press Del. If it is not closed, right-click the process and select End Task. If the processes are not closed, move on to the next step, as you will need some additional software to solve the problem.

If the software is closed, you can start uninstalling the malware. If you use Windows 10, press Win + X> Settings before selecting Apps in the screen that appears. In the Apps list & features , find the name of the malicious malware and select Uninstall.
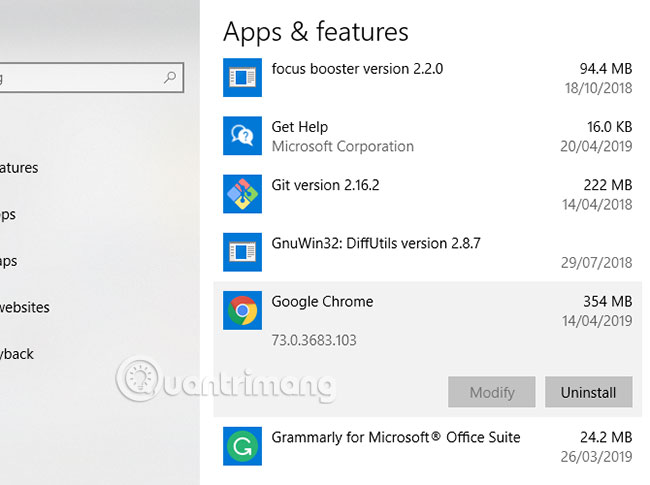
Step 2: Start scanning malware thoroughly
Assume that any malware you installed will not uninstall itself when you ask. For that reason, you will need to scan the entire PC to find another malware, virus or PUP (Potentially Unwanted Program).
Start by installing a number of tools to help you find and remove malware on your system, especially if you find processes that won't end on your PC. Software like Rkill will stop everything stubborn and won't stop when you use the task manager. Then you can try uninstalling Chromium malware using the above method.
You also need to make sure that you have the updated antivirus program installed. If you haven't done so already, install one of the best antivirus software available, free or paid, for your PC.

Get started with scanning for malware. If you use RogueKiller, open the software and select Standard Scan. After that, RogueKiller will scan the PC for malware files and processes.
When the process is complete, you will be asked if you want to review the results and delete any malware found, so confirm these software if they appear.
If you are using Malwarebytes, this process is similar. Click Scan Now in the main control panel menu or go to the Scan section and select the desired scanning method. Threat Scan options are recommended here.
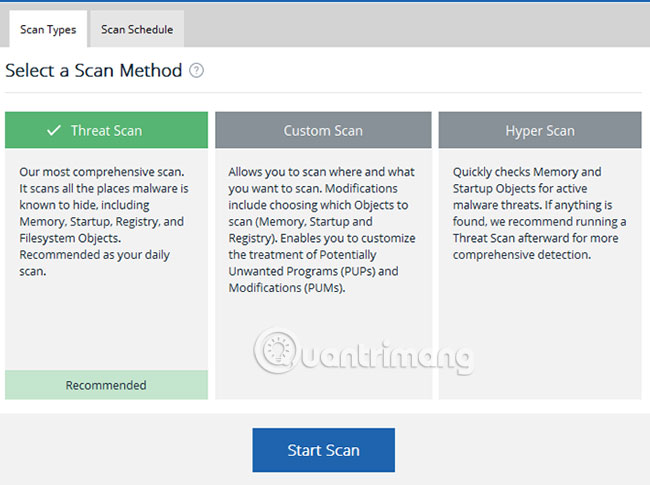
Run the same scanning process with the antivirus software you are using, including full scan at startup. If you have only recently installed malware and virus removal software, you should now actively scan your PC on a regular basis to help avoid any future infections.
Step 3: Delete the Chromium user data directory
Although the malware scanning process will remove any malicious Chromium malware it finds, there may still be some leftover files, including fake settings and profiles.
Please delete the Chromium installation directory. Don't worry about this, because the standard Chrome browser will re-create the folder when you run the program again.
As long as your Chrome browser is not running, press Win + R and enter % appdata% before clicking OK. You will be taken to the AppData Roaming folder for Windows users. Search for a folder with the name Chromium or, if your standard Chrome settings are infected with malware, look for GoogleChrome.
Delete the folders, then do the same in the AppData Local folder with Win + R and % localappdata%.
Step 4: Reset the standard Chrome settings
This step may not be necessary if you have been able to successfully remove malware on your PC and have deleted your installation directory, but for complete peace of mind, you should still do so. If you're running Chrome as a standard browser, you can reset it to the original settings within Chrome.
This step will remove any extensions or add-ons, browser history, and log you out of any account. You can start over with the new Chrome installation.
Click the menu icon (three vertical dots) at the top right and go to Settings> Advanced> Reset and Clean Up . Select Restore settings to their original defaults . Click Reset settings to confirm.
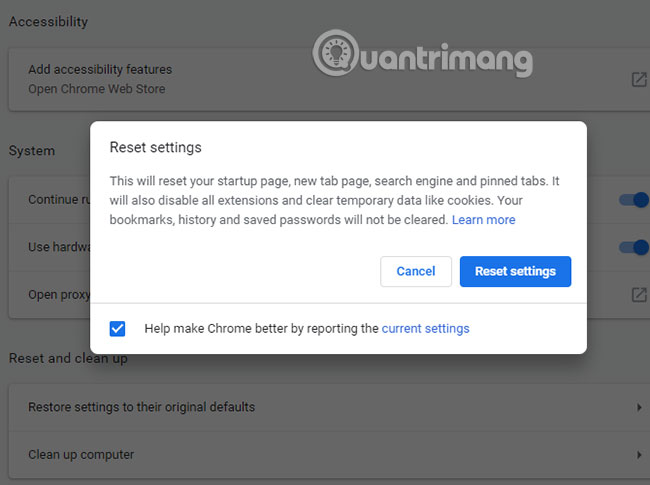
After that, installing Chrome will return to its original state. Note, only try this if you use the standard version of Google Chrome or a secure Chromium browser alternative.
Chromium malware is not always easy to detect, but there are some obvious signs if you take care. If the browser you are using does not use Google or another popular search engine, or you have not installed the browser from trusted sources, then you most likely have been infected with malware.
The best way to avoid future infections is to keep the system up to date and install the best malware protection for Windows PCs.
Hope you are succesful.
You should read it
- ★ Microsoft releases a new Windows 10 update, Microsoft Edge will be hidden if you install Edge Chromium
- ★ 8 best Chromium browsers to replace Chrome
- ★ How to run Chromium OS on Windows 10
- ★ These Android apps with more than 100,000 downloads contain Joker malware, please remove immediately
- ★ How to see which tabs consume RAM on Edge Chromium