How to enable processor-based security
PCs operating under Windows operating systems have the same level of protection as those used by high-performance servers. This technology - known under different names for each manufacturer, such as NX (No eXecute), EVP (Enhanced Virus Protection), XD (eXecute Disable) or DEP (Data Execution Protection) - allows The processor itself can detect when there is malicious code (such as virus or Trojan horse) and automatically disable that code. In this short tutorial, we will show you how to enable this feature.
This technology works by creating a separate zone for executing programs and for storing data in the computer's RAM, if a certain code in the area has been set aside for data storage. If it tries to run, the processor will assume that it is malicious and will prevent execution of that code.
You need to be aware that the processor itself does not have the ability to eliminate viruses from computers. If a PC using NX technology is infected with the virus, the processor will warn you (via the operating system) that your computer may be infected and will not allow the virus to work, however You still have to run an antivirus program to remove the virus from your computer and avoid infecting others (for example, when you send email with attachments).
To get this level of security in your computer, you need to have three prerequisites later. The first condition is that your processor must have this security technology. Secondly, your operating system must be able to recognize it and thirdly it must be enabled in the operating system.
Therefore, the first thing to do is check whether your CPU has this technology. This can be done with the help of a hardware identification utility, such as Sandra or Hwinfo .
With Sandra, click on Hardware, Processors and the program will list all the features provided for that CPU. This list will be very long, you must drag the scroll bar to ' Extended Features ' and find the feature ' XD / NX - No-execute Page Execution Protection '. You will see a word ' yes ' next to it if your CPU supports this level of security.
In Figures 1 and 2, we give two examples. The CPU on Figure 1 is an AMD CPU (Athlon 64 3800+) and the CPU on Figure 2 is Intel (Core 2 Extreme X6800). As you can see, the new CPUs from both manufacturers support this technology.

Figure 1: AMD CPU with NX feature
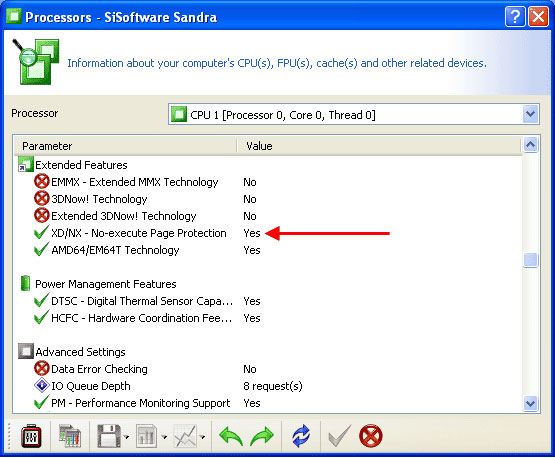
Figure 2: Intel CPU with NX feature
If your CPU does not have this feature, it will not be able to activate this protection feature.
The next step is to configure Windows to allow it to match this feature
Operating system configuration
For operating systems, both Linux and Solaris have adopted this technology in the last few years, but for Windows operating systems, this technology is only available on Windows XP SP 2. So if you If you use Windows XP, you need to upgrade to SP2. You can check if SP2 is installed by clicking on the System icon in Control Panel. If your operating system is SP 2, it will be listed under 'System'. If not, you need to install SP2.
In Windows XP SP2 and Windows Vista, you can check whether NX technology is enabled correctly by clicking the System icon in Control Panel. On the window that appears, click the Advanced tab, as shown in Figure 3.
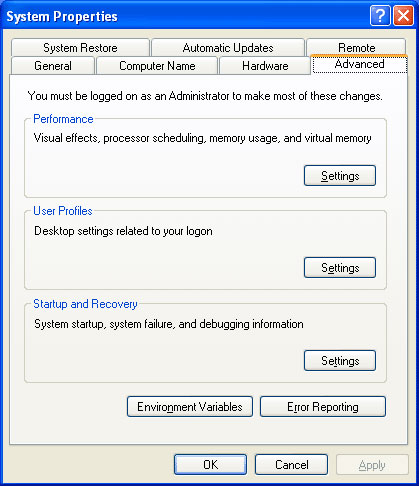
Figure 3: Advanced system configurations
In this window, click the first Settings button in the ' Performance ' field. The Data Execution Prevention tab will appear on the window that appears. This is where NX technology is configured or not.
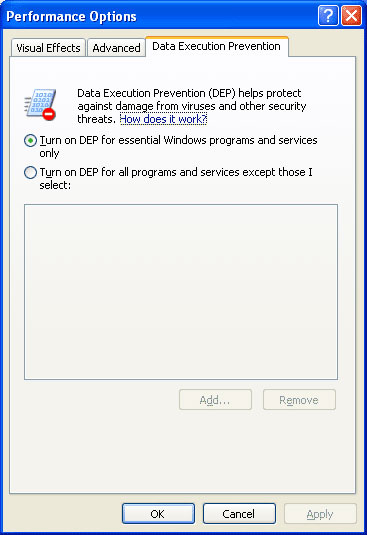
Figure 4: Configuring NX technology
As you can see, there are two options: ' Turn on DEP for essential Windows programs and services only ' ( Turn on DEP for necessary Windows programs and services ) and ' Turn on DEP for all programs and services except those I select '( Turn on DEP for all programs and services except the ones you choose ). This means that this technology will only protect the necessary Windows programs and services. With this configuration, NX technology will not protect you against viruses or Trojan Horse if they attack with a certain program.
Therefore, we recommend using the second option, which will work for all programs and services. If in the future you make a mistake - for example, Windows warns that a program that you know is not infected is trying to execute the code in the mapped memory location as the data area. then you can simply enter this window and add that this is a good program in its exclusion list, done by clicking the Add button.
Click OK , restart the computer, then your computer is protected with NX technology. However, as we said, although with this technology, you still have to use an antivirus program and remember to regularly upgrade the program. This is just a feature added to the extended security layer for computers.