Multi-factor authentication in Windows - Part 2: Prepare devices for XP and Windows 2003
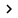 Part 1: USB tokens and smart cards
Part 1: USB tokens and smart cards
Martin Kiaer
Why do you need a CSP client
In the previous article, we made sure that the OS chip on the smart card is fully compatible with the CSP you want to use. Before starting with an example of deployment, we will show you what CSP is and why it is such an important component when working with multifactor authentication in Windows.
Basically, Cryptographic Service Provider (CSP) is a software component located between the security device and the Windows operating system. Figure 1 below shows it in Windows XP and Windows Server 2003:

Figure 1: CSP Role in Windows XP and Windows Server 2003
As you can see in the image above, communication between an application using multifactor authentication and cryptographic devices is done through the CryptoAPI functions. Some vendors have other functions and advanced features in their own CSP, while others take advantage of the functionality and features already available in Windows. This is an important concept that you need to understand, because it is the difference between Windows XP / Server 2003 and Windows Vista / Server 2008, and we will explain more in the next article of this series. .
For example, Windows versions that are currently supported by Microsoft have built-in support for many different smart cards. This means that you do not need to install a separate CSP. All communications to and from smart cards are done via CryptoAPI as mentioned previously. However, if the smart card solution you like is not on the list, you need to be sure to add a CSP that is supported by the card maker, so that you can use the smart card solution. with Windows. So what is important to note here? This is the CSP function that is always needed, even if you use the supported features that come with or use some of its features in the security device.
Now that we will learn the basics of CSP, first take a look at how CSP can be implemented in the real world.
How to prepare a third party CSP client for Windows XP and Windows Server 2003
We will not go into the basic step-by-step instructions on how to do it. However, we will show you a few different ways that include CSP and how you install a third party CSP client, when you attach a policy to the CSP client.
For this example, we want to follow the steps below:
- Implementing a smart card solution to prepare the card we can use Windows XP and Windows Server 2003 by integrating it with a Microsoft PKI.
- Include a activated security policy when users enter their pin code to access content on the smart card.
- Creating a CSP client can easily be installed on computers or servers in an enterprise environment.
To help fulfill the requirements listed above, we will use a SafeNet product called 'Borderless Security'. We do not want to focus on the application itself, only use it to present the principle behind implementing smart cards, so you can get an idea of how to configure a third-party CSP for Its multifactor authentication solution. With all of the above information, let's start to go into our example.
1. We installed the SafeNet Borderless application on a server and prepared to create and configure a CSP client for Windows XP and Windows Server 2003-based computers.
2. We start the management interface with SafeNet Borderless Security. The first thing to do is to link an existing PKI with your smart card solution. This is a very important step in our example, because certificates will be used to authenticate and configure smart cards for users in the infrastructure. A typical smart card solution in Microsoft's infrastructure requires a PKI to provide certificates with private and public key pairs that can map accounts in Active Directory. However, you need to be aware that each PKI is not necessarily required when implementing this solution, and this depends on the third-party CSP solution. Some vendors support password security with the content stored inside the security chip. Certificates are useful, including allowing us to disable a smart card by retrieving the relevant user certificate from Active Directory. Notice the following arrows in Figure 2.
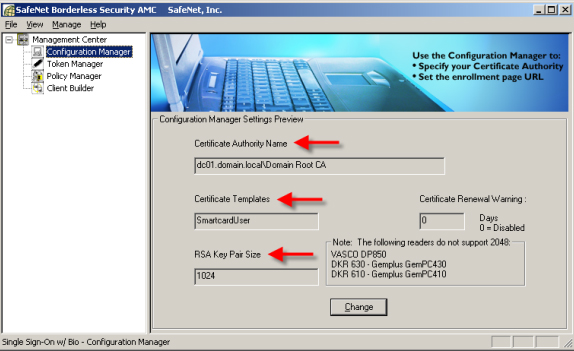
Figure 2: This is a smart card solution link with an existing PKI
- The Certificate Authority Name is configured to point to a CA issued in our Microsoft PKI.
- Once linked to the CA, it is possible to choose one of the available certificate templates in our PKI. For example, choose one of the default certificate templates called 'Smart Card User', but it can also be in the multi-purpose certificate template on version 2 (Windows Server 2003) or version 3 (Windows Server 2008 ).
- Better yet, you should choose a key pair of size 1024kb or more to protect the certificate that will be used during the preparation of the smart card. Lock with 512KB size for a certificate should not be used here.
3. Whenever the user needs to have a smart card issued, the smart card will be initialized (ie prepared) along with it is a security policy to control the pin length, number try, . In Figures 3 and 4 you can see some security options (policies) that we can associate with our CSP.

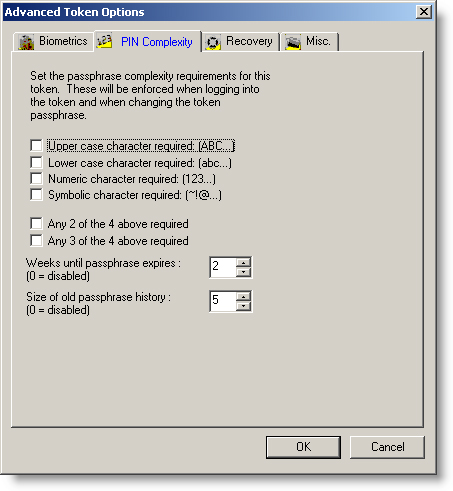
Figure 3 and 4: You can configure different policy settings for Pin code protection.
4. With this example, the last thing we need to do is prepare a CSP client package with settings from the previous steps. With SafeNet Bordless Security, we have many options to be configured. See Figures 5.6 and 7 for some possible options in your CSP client.

Figure 5

Figure 6
Figure 7
5. When you have selected the feature you want to include with the CSP client, the utility will create an MSI package, which can be provided to your client computers and servers, using the development method. Open your favorite software (see Figures 8 and 9).

Figure 8

Figure 9
6. The last thing you need to do is go to the server or client, where the smart card support is enabled.
a, Make sure that the latest driver for your multifactor authentication device is installed and working.
b, Install the CSP client package and make sure Windows can know the authentication device. Figure 10 shows you how it displays when our CSP client created in this example is installed on a computer.

Figure 10: Our CSP client is installed and ready to serve as a
a software that performs multi-factor authentication tasks in Windows.
Green card on the taskbar icon indicates that the smart card is plugged in.
7. CSP client is installed and ready for use with supported applications or multi-factor authentication required. One of these applications may be the ones we listed below:
a. MSGINA (i.e.) Windows login screen. Insert your smart card and enter your pin code for authentication. You can control how Windows works when using smart cards by adjusting some settings in Group Policy.
b, EAP-TLS or PEAP-TLS for authentication during VPN connections and wireless access, .
c, CMS (Card Management System) solution is used to provide smart cards. In this example we have used SafeNet's 'light' product, but if you need to provide 50 or more of these smart cards, you should consider Intercede's true CMS solution. (SafeNet), Microsoft, Entrust, Aladdin, .
d, There are many other solutions that use everything from readers' fingerprints to facial recognition.
A CSP can also be important in other scenarios that we didn't cover in this article. For example during the PKI implementation, you get the choice of using Microsoft's own CSP or third party. Usually you should use the third party's CSP when choosing an HSM solution to protect CA's private keys.
Conclude
In this article, we want to introduce you to the importance of software responsible for linking a multifactor authentication solution to Windows. In the next article, I will show you some changes with Windows Vista and Windows Server 2008 along with what you should care about and know about when implementing a multifactor authentication solution for this platform. .