Scripting and automatically customizing Group Policy
Derek Melber
Sometimes Group Policy Management Console (GPMC) will not provide enough flexibility to perform large tasks. In the case of establishing, changing or removing credentials for a large number of GPOs, the GPMC may cause some difficulties or can be said to be cumbersome. In this tutorial, we will show you another way that is much easier. The solution here is to use Microsoft's GPMC scripting. These scripts are quite numerous and have been updated, upgraded to support Windows Vista and Windows Server 2008. With them, you can change the permissions on one or all of the GPOs easily. easy.
Mandates for GPOs
Before starting the scripting and automating delegation for GPOs, there is an important issue to note that you must know which options (options) you have. All of the credentials listed below can be set using GPMC, but that method can be time consuming. With GPO management, you have the following options:
Create GPOs
This is a delegated task for the entire domain, however it is configured at the Group Policy Objects node within the GPMC, as shown in Figure 1.

Figure 1: Creation of GPOs is a central domain delegate
Link GPO
The ability to link GPOs to a node in Active Directory is very strong. When the GPO is linked, the objects under the node (domain, site, or organizational unit) will start automatically to receive the policy settings in the linked GPOs. Figure 2 illustrates the trust option for GPOs linked to a node.

Figure 2: Linked GPOs are delegated at the Site, domain or organizational unit level
Draft management of GPOs
The ability to edit GPOs is a great function, especially if that GPO is already linked to a node in Active Directory. Therefore, it is important to control who can edit. There are two editing levels, one that allows deleting and changing the security for GPOs. These credentials are done at the GPO level, as shown in Figure 3.
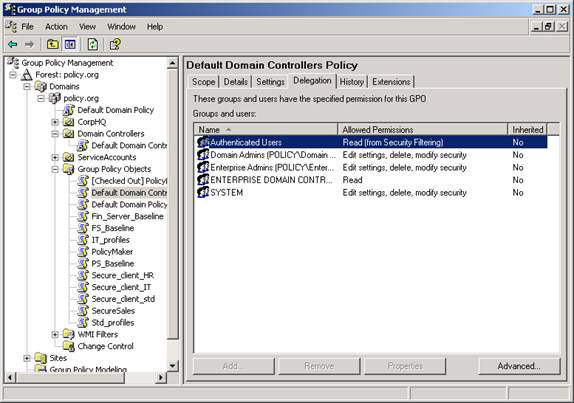
Figure 3: Edit and manage (completely) GPOs delegated on a GPO by the base GPO
Use GPMC scripts to automate GPO security delegation
GPMC scripts allow you to make similar changes to the GPO security that the GPMC GUI does, but it allows you to perform larger tasks with faster time. Assume that you have installed Microsoft Advanced Group Policy Management (AGPM). Before you can use AGPM, you must change the permissions for all GPOs within the GPMC to ensure that administrators cannot edit them through GPMC. If this is not done, the GPO in production (introduced in GPMC) can easily be lost in sync with the GPO that you import into the AGPM environment. To remove and reset permissions for multiple GPOs for setup purposes, this is purely a difficult task. However, with the GrantPermissionOnAllGPOs.wsf script, this task can be done quickly! Other GPMC scripts also perform the same functions as described below.
Note:
To download GPMC scripts, go to the address after Group Policy Management Console Sample Scripts.
GrantPermissionOnAllGPOs.wsf
This script will assume a certain clause for a user or a group in all GPOs located in the domain. This problem will appear for GPOs that are not even linked to the Active Directory node. This alternate switch is useful because it can remove existing permissions and replace them with new permissions. If a specified clause for a security group already exists on the list of permissions for the GPO, the two higher terms will be replaced in the security group (unless this alternate switch is used). )
Syntax
Usage: GrantPermissionOnAllGPOs.wsf GroupName / Permission: value [/ Replace] [/ Q] [/ Domain: value]
GroupName: The security principal to grant permissions to
Permission: The permission level to set. Can be 'Read', 'Apply', 'Edit', 'FullEdit' or 'None'
Thay đổi: Specifies mà có quyền hiện thời nên được thay đổi
Q: Quiet mode - not display a warning before executing the script
Domain: DNS name of domain
For example
cscript GrantPermissionOnAllGPOs.wsf "GPO Admins" / Permission: Edit
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Warning! Bởi executing script này, tất cả GPOs trong tên sở hữu sẽ được cập nhật với chế độ đặt quyền hạn.
Bạn có thể được cập nhật Both Active Directory and Sysvol portions of GPO will be. Đây sẽ được kết quả trong các tập tin Sysvol của mỗi GPO đang được sao chép vào các bộ điều khiển Domain replica, và có thể không tạo công báo traffic replication trong tên của bạn.
Nếu bạn có kết nối mạng Slow, hoặc chế độ bị hạn chế giữa các máy phục vụ của bạn, bạn nên kiểm tra các dữ liệu số trên các Sys, sẽ được tạo lại trước khi thực hiện câu lệnh này.
Bạn có muốn tiếp tục? [Y / N] y
Updated GPO 'Default Domain Policy' to 'Edit' for GPO Admins
Updated GPO 'Default Domain Controllers Policy' to 'Edit' for GPO Admins
SetGPOCreationPermissions.wsf
This script allows or removes the ability to create GPOs in a domain for a specific security group or user.
Syntax
Usage: SetGPOCreationPermissions.wsf Group [/ Remove] [/ Domain: value]
Group: The security group to grant GPO creation rights to
Gỡ bỏ: Ghi nhớ quyền hạn thay thế để Grant nó
Domain: DNS name of domain
Example and output
cscript SetGPOCreationPermissions.wsf "GPO Admins"
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Added 'GPO Admins' as having GPO creation rights in Fabrikam.com.
SetGPOPermissions.wsf
This script will set the permissions on a pre-defined GPO for the group defined. All other scripts must also have the syntax of the script and output. This script will fail if you do not define arguments for it.
Syntax
Usage: SetGPOPermissions.wsf: / Permission: [/ Replace] [/ Domain:]
Permission: The permission level to set. Can be 'Read', 'Apply', 'Edit', 'FullEdit' or 'None'
Thay đổi: Specifies mà có quyền hiện thời nên được thay đổi
Domain: DNS name of domain
Example and output
cscript SetGPOPermissions.wsf "Hardened Server GPO" "Server Operators" / Permission: Edit
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Modified GPO Hardened Server GPO to give Server Operators Edit rights.
SetGPOPermissionsBySOM.wsf
This script allows a certain provision for the security goal specified for all GPOs located in the SOM of the site, domain, or organization block that was targeted. Full control is allowed with this scenario and the conversion keys, as substitutes or not, recursive options allow you to modify the terms and scope of the terms.
Syntax
Usage: SetGPOPermissionsBySOM.wsf SOM Group / Permission: value [/ Replace] [/ Recursive] [/ Domain: value]
SOM: The name of the site, miền hay OU để tiến trình
Group: Tên tên của nhóm hoặc người dùng để Grant quyền
Permission: The permission to grant. Can be 'None', 'Read', 'Apply', 'Edit' or 'FullEdit'
Thay đổi: Rep thay đổi quyền hạn có có có quyền ghi ghi. Không thì, script này được kiểm tra xác thực cho phép yêu cầu có ít nhất số xác định quyền Grant
Recursive: Applies the changes to all child OUs as well
Domain: DNS name of domain
Example and output
In this example, there is an error but the script is still running, the / Recursive switch is used in the example and no GPO is previously linked in the Test OU.
cscript SetGPOPermissionsBySOM.wsf Servers "Server Operators" / Permission: Read / Recursive
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Đang cập nhật all GPOs đã được chọn vào máy phục vụ OU để đưa ra quyền sang Server Operators
Đang cập nhật các GPOs đã được kết nối đến OU Model Office để đưa ra quyền sang Server Operators
Updating permissions on linked GPO 'Hardened Server GPO'
Đang cập nhật các GPOs đã liên kết đến OU Production để đưa ra rights to Server Operators
Updating permissions on linked GPO 'Hardened Server GPO'
Đang cập nhật all GPOs đã liên kết đến OU Test để đưa ra quyền sang Server Operators
Error getting SOM CN = Servers, CN = Default-First-Site-Name, CN = Sites, CN = Configuration, DC = Fabrikam, DC = com
SetSOMPermissions.wsf
This scenario targets delegation that can be set up for Active Directory nodes, where GPOs can be linked. Since this is a function that only affects the appropriate permissions, only Windows Server 2003 or 2008 domain controllers, the RSoP Planning clause can be upgraded.
Syntax
Usage: SetSOMPermissions.wsf SOM Group / Permission: value [/ Inherit] [/ Domain: value]
Options:
SOM: The name of the site, miền hay OU để tiến trình
Group: Tên tên của nhóm hoặc người dùng để Grant quyền
Permission: The permission to grant. Can be 'LinkGPOs', 'RSoPLogging', 'RSoPPlanning', 'All' or 'None'
Inherit: Specifies the permissions that should be inherited by all child containers
Domain: DNS name of domain
Example and output
In these two examples, RSOPLogging has been added and then RSOPLogging is added to all GPOs.
cscript SetSOMPermissions.wsf Servers "server operators" / Permission: RSOPLogging / inherit
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Added the 'RSoP Logging Mode' permission for server operators.
cscript SetSOMPermissions.wsf Servers "server operators" / Permission: RSOPPlanning / inherit
Microsoft (R) Windows Script Host Version 5.7
Copyright (C) Microsoft Corporation. All rights reserved.
Added the 'RSoP Planning Mode' permission for server operators.
Conclude
GPMC scripts can save you a lot of time when you need to perform proxy issues on some GPOs and are almost necessary when you need to change GPOs in the domain. They are also easy to use, fully capable of managing all GPMC delegation aspects, and in addition you can download them completely for free. After downloading these scripts, what to do is decide which delegation you need to perform, launch the script, set up the switches.