How to change the encryption password LUKS
It's great if you've decided to protect your data with LUKS. But you need to change if you have chosen an inappropriate passphrase. Fortunately, unlike many encryption solutions, LUKS allows to change passphrases quite easily. However, this is not a solution for losing a passphrase, because you need to know the passphrase earlier. In general, this is just an effective way to change or remove inappropriate old passphrases.
Change the passphrase for LUKS
Changing the passphrase on LUKS drive only has a single passphrase extremely easily. Open the terminal and run the following command, replacing 'sdX' with the actual drive location. First, you will be prompted to enter an existing passphrase. Then you can create a new passphrase.
sudo cryptsetup luksChangeKey /dev/sdX 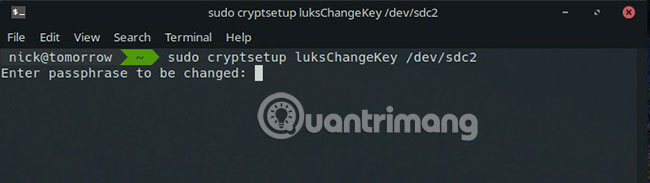
LUKS drive with many passphrases
LUKS drives can have multiple passphrases or main files associated with them, up to 8 passphrases. To get started, check your LUKS drive and see how many keys it has. Chances are, you will only see key slot 0 . That was the first key.
sudo cryptsetup luksDump /dev/sdX | grep -i key 
If there are empty slots open, you can always add another passphrase to your drive. Run the following command and a new key will be added to the first blank slot.
sudo cryptsetup luksAddKey /dev/sdX 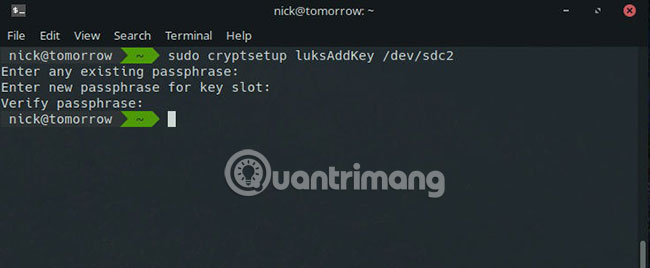
When you have to manage multiple keys on the same drive, you will need the ability to target specific keys. Again, you can do it quite simply with the -S flag . Just add the number of slots after the -S flag and select a key to change.
sudo cryptsetup luksChangeKey /dev/sdX -S 2 Delete the passphrase
When working with multiple keys, you may sometimes need to delete the old keys. There are several ways that LUKS allows you to handle this. The easiest way is to use the integrated command to delete the key and LUKS will prompt you to enter a passphrase. LUKS will automatically delete the key associated with the passphrase you entered.
sudo cryptsetup luksRemoveKey /dev/sdX 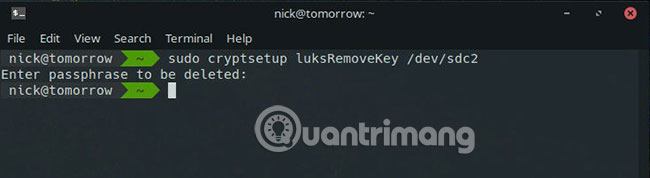
In case you want to specify yourself, you can use the KillSlot command to delete the key located in a certain slot. Just include the number of drive and key slots on that slot will be deleted.
sudo cryptsetup luksKillSlot /dev/sdX 2 Whichever way you choose to manage your LUKS passphrase, you will find that it is one of the most flexible encryption options available. Because LUKS allows to change, manage and delete keys, you can add new security layers to your drive. LUKS also allows you to control access for a group of people, instead of just you.
Hope you are succesful.
 How to install Pip in Ubuntu
How to install Pip in Ubuntu How to configure static IP addresses on Linux
How to configure static IP addresses on Linux 7 best antivirus programs for Ubuntu
7 best antivirus programs for Ubuntu How to check for simple Linux server performance
How to check for simple Linux server performance Check the current user on Linux
Check the current user on Linux How to display the date and time in Linux Terminal
How to display the date and time in Linux Terminal