How to encrypt partitions on Linux with dm-crypt
Hard drives and SSDs can be easily removed from a laptop or desktop computer. At this point, all security measures implemented by your operating system will have no more thoughts. If you have data to protect, you can create encrypted containers. You will store sensitive files there, the remaining files are saved on normal partitions.
The easiest is to set up an encrypted partition when you install the Linux distribution. The installer can guide you to do that. If you've skipped this stage, follow the steps in the following guide to create a secret secret partition.
How to encrypt partitions on Linux with dm-crypt
- Prerequisites
- Install cryptsetup
- Find the Block Device Name of the partition
- Set the title LUKS
- Create a file system on the partition
- Mount encrypted partitions
Prerequisites
You need an empty partition for this process. This means an unformatted partition (no file system on it).
If your formatted partition currently occupies all of the free space on the storage device, you will need to use GParted to shrink one of them.
Warning : You should back up your data first. When shrinking its partition and file system, there are certain risks. The computer may be faulty or lose power during processing, making the file system inconsistent and difficult to recover.
Follow the first steps in this tutorial to resize the partition using GParted. Or, if there is an unnecessary partition, you can delete it. (After you release some space and they show an "unallocated" status , skip the remaining steps in the tutorial). Specifically, do not create a partition named ext4. Instead, right-click on the unallocated space, as shown in the guide. In the dialog window that opens, you will see a field labeled 'File system'. Normally, ext4 will be selected as the default here. Click it and change it to "clear".
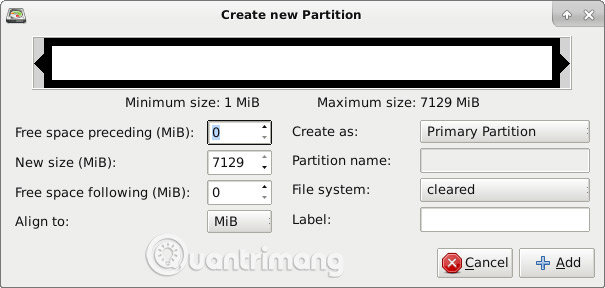
After you select 'Add', click on the green check mark to apply the changes.
Install cryptsetup
If you booted the operating system directly to edit your partition using GParted, reboot into the main Linux distribution.
Open the terminal emulator. On Debian-based systems, such as Ubuntu or Linux Mint, enter this command:
sudo apt update && sudo apt install cryptsetup 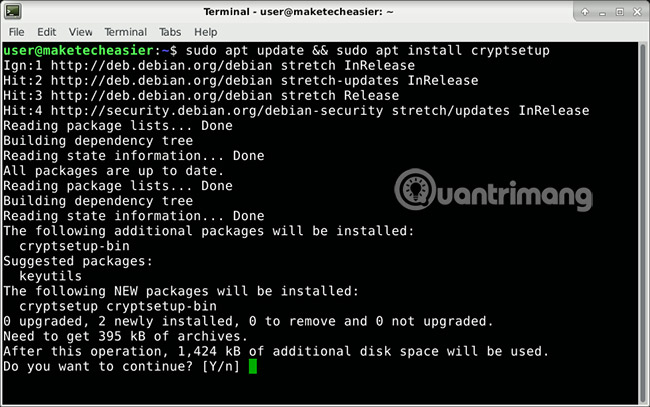
On distributions like Fedora or CentOS and other versions using RPM instead of DEB, you can install cryptsetup. If not, you can install it with:
sudo yum install cryptsetup On OpenSUSE, if cryptsetup is not preinstalled, you can install it with:
sudo zypper refresh && sudo zypper install cryptsetup And on Arch-based distributions, you will use this command:
sudo pacman -S cryptsetup Find the Block Device Name of the partition
Enter the following command:
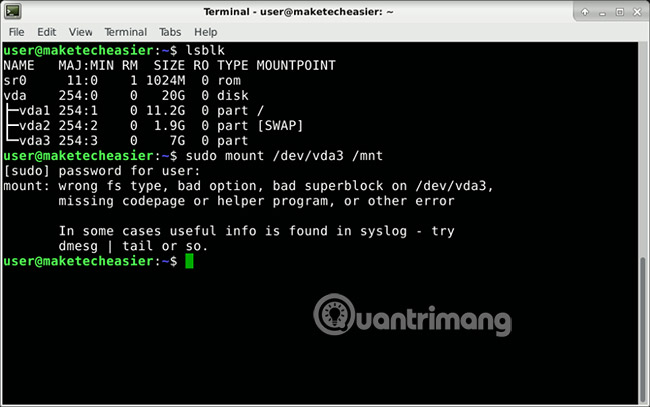
lsblk 
In the example provided in the picture, the storage device is 'vda'. 'vda1' to 'vda3' are partitions.
To find the partition you have prepared, remember the size you have preserved for it. You will find it among partitions that do not have mount points. In your case, this could be '/ dev / sda2' instead of '/ dev / sda3'.
Partition encryption will overwrite the data on it (if any), meaning that if you get the device name wrong, you may cancel the data useful. To ensure you have the correct device name, you can install GParted and review your partition layout. Device name will be listed in the graphical user interface. Do not use the name you saw in GParted when you boot from the system directly (if you did it). The layout displayed in the live system will be different from the layout you see when booting from the installed distribution.
There is another way to make sure you don't write on the wrong device. Try mount it. Normally, it will refuse to do so because there is no file system on it.
Important note : Remember to always replace "vda3" with your device name:
sudo mount /dev/vda3 /mnt In your case, the command could be sudo mount / dev / sda2 / mnt or something else.
This is the message you will receive.
Set the title LUKS
When you are sure you have the appropriate device name, add the LUKS header to the partition.
sudo cryptsetup luksFormat /dev/vda3 Enter 'YES' and then create a strong password for the encrypted partition. Re-enter the same password when asked to verify the passphrase.
Create a file system on the partition
You must map this physical device to the virtual device. What is written to the virtual device will be encrypted before being stored on the physical device.
sudo cryptsetup luksOpen /dev/vda3 encrypted-partition The partition needs a file system that can be used. Create an ext4 file system with this command:
sudo mkfs.ext4 /dev/mapper/encrypted-partition 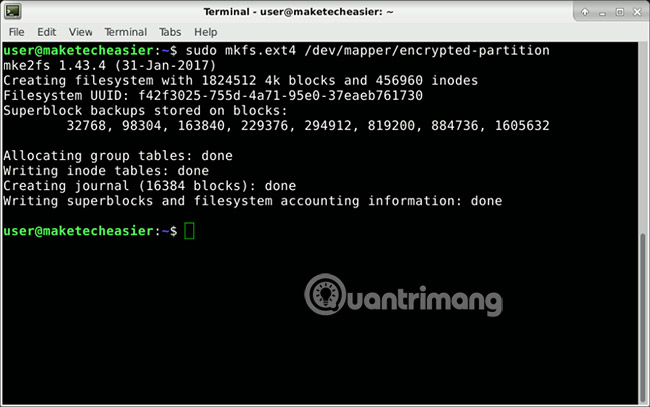
Mount encrypted partitions
Create a folder where you will mount the file system from the partition.
mkdir ~/encrypted-storage Mount the file system:
sudo mount /dev/mapper/encrypted-partition ~/encrypted-storage Change that directory:
cd ~/encrypted-storage Currently, only root users can write here. Allow your users to record in this file system by placing them as owners of higher level folders. Copy and paste the entire command, including " . " At the end.
sudo chown $USER:$USER . Restrict other users from reading or writing to this directory.
chmod o=. At this point, most file managers will show you the new encrypted device on the interface. The following figure shows how it looks in file manager Thunar, the default is used in the XFCE desktop environment.
If the drive is not mounted, when you click on it, you will be asked for the sudo drive password and password. The drive will be automatically mounted and you can browse it. The mount point will be different from '~ / encrypted-storage'. It may look like this: '/ media / user / f42f3025-755d-4a71-95e0-37eaeb761730 /'.
That does not matter. The rights you previously set still apply. It is important to remember to right click on it and disconnect when you successfully complete all tasks with the drive. Unmounting and closing the virtual device ensures that no one can read data from the encrypted partition, even from your operating system.
If for some reason, your manager file does not support this feature, you can mount it from the terminal:
sudo cryptsetup luksOpen /dev/vda3 encrypted-partition sudo mount /dev/mapper/encrypted-partition ~/encrypted-storage You can now access the drive by going to "/ home / username / encrypted-storage" in the file manager. When you're done, remove the file system mount and close the virtual device:
cd && sudo umount /dev/mapper/encrypted-partition sudo cryptsetup luksClose /dev/mapper/encrypted-partition Now your important files are safe. Knowing that no one can see what you store in your computer will make you much more secure. Good luck!
See more:
- How to encrypt LVM partitions when installing Kali Linux
- Select the Scheme partition in Linux
- How to hide the entire file system
You should read it
- ★ How to access Windows encrypted partitions using Bitlocker from Linux
- ★ How to access Linux Ext4 partition from Windows
- ★ Instructions for creating a master partition in Ubuntu
- ★ How to mount the hard drive and partition using the Linux command line
- ★ How to prevent and handle when Windows Update deletes Linux