Content of SCNP certificate curriculum
SCNP is a security certificate that large companies and corporations choose to train their employees, such as VNPT Corporation. In addition, this certificate is also loved by many young people, because the content that the program provides is close to reality, from basic to advanced, so learners or researchers easily grasp the content that the curriculum Out, and when finished learning, can apply immediately to your company or organization.
With lessons learned from the most basic part of the TCP / IP model, how to divide the Subnet (Subnet), the Subnet Mask addressing feature is presented in very easy-to-understand tricks, up to practical skills such as monitoring. Network monitoring, packet signature analysis, building firewalls, deploying HoneyPot systems, IDS intrusion detection systems or writing, applying and maintaining security policies for business models . makes SCNP a of current top choices when it comes to research on pragmatic security.
Now, Security365.Biz combined with QuanTriMang.Com to synthesize, compile and publish articles according to the official curriculum of SCNP for everyone to consult.
Advanced knowledge of TCP / IP
Overview : for computers to communicate with each other, they must use the same protocol as in a real environment, two people must use the same language to communicate. And there are many other protocol stack applied to the communication process among computers, but the most common and popular is the TCP / IP protocol, this is the main protocol used on the Internet as well as in the system side. LANs, WANs of current companies.
Topic 1A. The concept of TCP / IP
TCP / IP model : TCP / IP stands for Transmission Control Protocol / Internet Protocol, including a stack of protocols divided into four layers: Application Layer, Transport Layer, Internet Layer and Network Access as shown below:
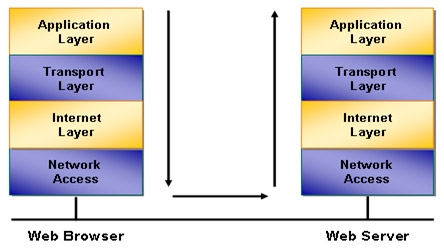
As shown in the figure above, for example, a computer that wants to view a web page on a web server, for example, www.quantrimang.com , will be divided into several separate stages, each of which will be one floor in the model. 4 TCP / IP layers are in charge, those 4 layers include:
- Application Layer : is the highest layer in the model, this floor will communicate with online software such as connecting and displaying www.quantrimang.com website in the above example, communicating with Users through applications such as Outlook, IE, and Zilla Files operate at this level
- Transport Layer : This layer is responsible for transporting packets and data required by the upper layer. There are two protocols operating at the transport layer: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). The main difference between the two protocols is that TCP is a reliable protocol with error checking and acknowledgment mechanisms so data sent is more secure than applications that use UDP, however With the above procedures, UDP will have advantages in terms of execution speed.
- Internet Layer : when data is transmitted on the network they need to specify the optimal route to be able to transfer from the transmitter to the receiver, and the network layer will take over the addressing function. as well as defining routes.
- Network Access Layer : This is where data will be transmitted and received during communication, devices at this level such as network cable or radio waves.
So in the above example, when a user accesses www.quantrimang.com using an IE or FireFox application from the application layer, this request will be moved to the lower layer of the transport layer to apply the appropriate protocols. TCP or UDP, thereby determining mechanisms for breaking down data into packets and placing appropriate flags, applying error checking mechanisms . Next, packets will be routed down to handle at the network layer. , to be able to identify the site's IP address and find the most appropriate route and eventually the data will be transferred to radio signals or electrical signals and transmitted on conductors such as network cables. , radio …
OSI model
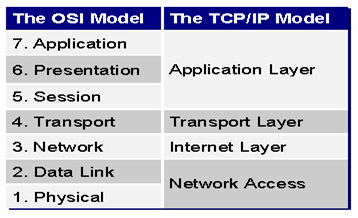
In addition to the TCP / IP model, we also have a 7-layer OSI model (Open System Interconnect by the International Organization for Standardization organization) including:
- Application Layer : communicate with software and network applications.
- Presentation Layer : responsible for compression and encoding services, presenting data.
- Session Layer : has setup and management functions (such as packet size) and ends communication sessions.
- Transport Layer : is responsible for controlling errors and recovering data between 2 computers participating in the communication. Both TCP and UDP protocols work at this level.
- Network Layer : is responsible for setting logical addresses, defining routes, transferring packets. IP protocol works here
- Data Link Layer : has the function of wrapping data frames during communication on conductors. The error checking information will be added to this layer normally through the Cyclic Redundancy Check (CRC) format. In addition, this layer is divided into 2 sub-layers: LLC (Logical Link Control) and MAC (Media Access Control). The MAC layer identifies the network device's physical addresses such as MAC Address, which is the only address for each device. The link between MAC Address and Logic Address (such as IP address) will be represented by LLC Layer.
- Physical Layer: this is the most logical and practical layer in the 7-layer model, responsible for transmitting data streams on the network.
Both the TCP / IP and OSI models are fully compatible, here is a comparison between the two models:
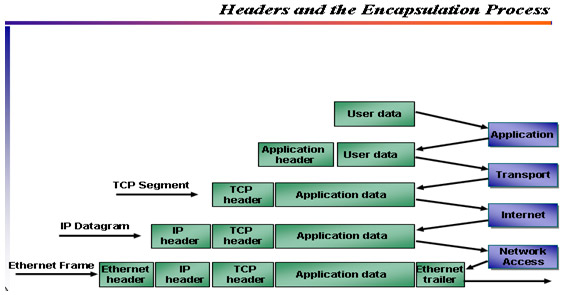
During the communication process when the data is transferred to the lower layer, it will be attached to a corresponding information form of that layer called a header, for example when the data moves to the Network layer, the header attached will be used to determine Specify the transmission and reception addresses of computers. The process of attaching these headers is called an encapsulation process.
RFC
All definitions of protocols that operate at all levels in the above models are defined and described in RFCs. We can refer to rfc at www.rfc-editor.org, here are some common rfc common on HTI exams:
- Internet Protocol (IP): RFC 791
- Internet Control Messaging Protocol (ICMP): RFC 792
- Transmission Control Protocol (TCP): RFC 793
- User Datagram Protocol (UDP): RFC 768
Function of IP Protocal
IP protocol works at Network layer in both OSI and TCP / IP models. The main function of IP is to identify the source and destination addresses for data during transmission and based on these addresses the packet will be routed to transport according to the appropriate routes. So we see that every machine on the network has only one address because if there are two machines with the same IP address, the data will not know which machine to transmit, because of that reason when we configure 2 duplicates will only appear IP conflict alarm. However, IP does not have a mechanism to check whether data or packets have been transmitted to the destination, if anything is lost . so the upper TCP protocol will take over this task.
Convert between Binary, Decimal, and Hexadecimal
When we access other servers or computers on the network, we often use DNS names like www.quantrimang.com or follow a decimal IP address in the form of 222.255.31.160 , however in the process of processing the name conversion computers The machine and the decimal number come in binary form consisting of bits 0 or 1. So mastering how to convert decimal numbers to binary is a necessity. There are many tools that support this conversion as easily as the calculator program on a computer, just switch to View -> Scientific mode.
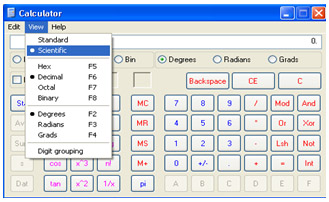
Here are some decimal to binary conversion results:
The 11000000 binary is decimal 192: 128 + 64 + 0 + 0 + 0 + 0 + 0 + 0
Binary 10000000 is decimal 128: 128 + 0 + 0 + 0 + 0 + 0 + 0 + 0
Binary 10000010 is decimal 130: 128 + 0 + 0 + 0 + 0 + 0 + 2 + 0
Binary 01011010 is decimal 90: 0 + 64 + 0 + 16 + 8 + 0 + 2 + 0
The current IP address we are using is IPv4, which is a sequence of 32 binary characters (32 bits) divided into 4 octets, each containing 8 bits as 11000000 (192), and to convert this decimal value To binary, we only need to multiply the number m by 2 caps n where n is the sequence number of m calculated from right to left with the increasing direction from 0 to 7 (m is 0 or 1). Therefore 01011010 will have a decimal value of 0 + 64 + 0 + 16 + 8 + 0 + 2 + 0
In addition, the IP address is also shown as HEX number like IP 192.168.10.1 with HEX value is C0-A8-0A-01. Here are some instructions on how to convert from decimal to HEX:
1. Divide 192 by 16. The result is 12, balance 0. Because the decimal value of 12 is equivalent to Hex and decimal 0 is Hex 0 so decimal 192 is equivalent to Hex C0.
2. Divide 168 by 16. The result is 10, balance 8. For decimal 10 is Hex A and decimal 8 is Hex 8, 168 is Hex A8.
3. Decimal 10 is Hex A.
4. Decimal 1 is Hex 1.
5. So decimal 192.168.10.1 has Hex C0A80A01 value.
Another calculation is to convert decimal numbers to binary and convert binary to Hex according to the following rules:
1. Decimal 192 is equivalent to 11 million binary.
2. Decimal 168 equivalent binary 10101000.
3. Decimal 10 is equivalent to binary 00001010.
4. Decimal 1 is equivalent to binary 00000001.
5. Binary 1100 is equivalent to Hex C.
6. Binary 0000 is equivalent to Hex 0.
7. Binary 1010 is equivalent to Hex A.
8. Binary 1000 Hex equivalent.
9. Binary 0000 is equivalent to Hex 0.
10. Binary 1010 is equivalent to Hex A.
11. Binary 0000 is equivalent to Hex 0.
12. Binary 0001 is equivalent to Hex 1.
13. The final result shows decimal 192.168.10.1 with Hex value of C0A80A01.
IP address classes
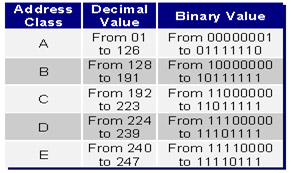
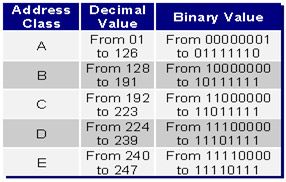
The IP address consists of two parts: the address of the network layer and the host address. By definition, there are 5 classes of IP addresses: A, B, C, D and E with the following differences:
- Class A uses the first 8 bits for the network address and the remaining 24 bits for the host part. This means that in a Class A network there are more than 16 million hosts (2 caps 24 minus 2). All Class A addresses start with 0xxxxxxx.
- Class B uses 16 bits for the network address and the remaining 16 bits for the host. Class B addresses with the first otect are 10xxxxxx
- Class C uses 24 bits for the network part and the remaining 8 bits for the host part. The first class C addresses with octec are 110xxxxx.
- Class D is not used for hosts but used for multicast communications. With the first octec is 1110xxxx
- Class E is used for research purposes, not for hosts. The first octect is 11110xxx
The following table describes some key characteristics of network classes:
Private IP Address
In addition, there are some reserved addresses called private IP addresses that are used to type intranet addresses. Applying private addresses makes managing the network more scientific and preventing sppofing IP address because most routers will not forward packets on the Internet that originate from this address. Private address addresses corresponding to each network layer are:
- Class A: 10.0.0.0 to 10.255.255.255
- Class B: 172.16.0.0 to 172.31.255.255
- Class C: 192.168.0.0 to 192.168.255.255
In addition, addresses of the range 127.0.0.0 to 127.255.255.255 as loopback address (127.0.0.1) used for checking the system or APIPA addresses (169.254.0.0 to 169.254.255.255) are also reserved. You can refer to RFC 1918 for private IP address.
SubNet Mask
Along with the IP address, the subnet mask is an indispensable component of a host. Based on the subnet mask and through AND (ANDing process) will determine the network class of a host. For example, a computer with an IP address of 192.168.1.33/24 will use 24 bits as a subnet mask (11111111. 11111111. 11111111.00000000) and when using AND operation, the subnet address 192.168.1.0 is given. (due to x AND 1 = x). By default, Class A uses 8 bits as subnet mask while Class B and C use 16 and 24 bits as subnet masks.
In addition, some documents using the format 255.255.255.0 to indicate subnet mask is / 24 or 255.0.0.0 is / 8
Exercises about dividing Subbnet
For example, the company has multiple network layers located in different locations in a building, and we want to divide the 12 network layers based on the IP structure originally defined as 10.0.0.0 / 8.
First, we determine the number of bits that will be added by the host part to be used for the network layer. In this case we need to borrow 4 more bits (because 12 is 1100 in binary). Then the subnet mask will be / 12 or 255.240.0.0 and the subnet layer will be permutation of the xxxx bits in the serial number after 00001010.xxxx yyyy.yyyyyyyy.yyyyyyyy, and we will identify the following network classes:
Subnetwork Binary Address Decimal Address
First 00001010.0000 0000.00000000.00000000 10.0.0.0
Second 00001010.0001 0000.00000000.00000000 10.16.0.0
Third 00001010.0010 0000.00000000.00000000 10.32.0.0
Fourth 00001010.0011 0000.00000000.00000000 10.48.0.0
Fifth 00001010.0100 0000.00 billion 00000000 10.64.0.0
Sixth 00001010.0101 0000.00000000.00000000 10.80.0.0
Seventh 00001010.0110 0000.00000000.00000000 10.96.0.0
Eighth 00001010.0111 0000.00 billion.00000000 10.112.0.0
Ninth 00001010.1000 0000.00 billion 00000000 10.128.0.0
Tenth 00001010.1001 0000.00 billion.00000000 10.144.0.0
Eleventh 00001010.1010 0000.00 billion.00000000 10.160.0.0
Twelfth 00001010.1011 0000.00 billion.00000000 10.176.0.0
Thirteenth 00001010.1100 0000.00000000.00000000 10.192.0.0
Fourteenth 00001010.1101 0000.00000000.00000000 10.208.0.0
Fifteenth 00001010.1110 0000.00 billion.00000000 10.224.0.0
Sixteenth 00001010.1111 0000.00 billion.00000000 10.240.0.0
There are a lot of tools that help us calculate subnet classes easily such as the IP Subnet Calculator.
X- Casting
Unicast
Broadcast
Multicast
Topic 1B: Analysis of the Three-Way Handshake process
In Topic 1B we will consider the handshaking processes of two computers before communication is also called the Tree-way Handshake. Before starting, take a look at a comparison of some of the differences between the two transport layer protocols, TCP and UDP
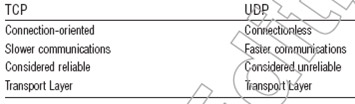
Through the above analysis, we see that the TCP protocol is a more reliable protocol and before communicating source and destination machines that need to initiate links, however UDP has a speed advantage. So, for time-priority applications, UDP is the best option, whereas if the security and the data guarantee reach the destination, TCP is the optimal choice. This is also the main difference that you need to keep in mind when handling questions of the SCNP international certification exam.
TCP Flag : In its communication process, TCP protocol uses flags called Flag TCP's SYN, ACK, FIN, RESET, PUSH and URGENT. These flags are usually identified by their first characters such as S, A, F, R, P and urg.
- SYN is used at the beginning of the link initiation process to synchronize two computers before the data is transmitted.
- ACK is used to send confirmation message after receiving data from the sender. Usually used in phase 2 of the link initialization process.
- FIN sent by the transmitter requires termination of the link.
- RESET: used to reset the session.
- PUSH is applied when the transmitting party requests data to be sent directly to the application without going through the buffer.
- URGENT is used for emergency data transfer with the highest priority.
Sequence and Acknowledgment Number
In addition to the TCP Flag, the Sequence and Acknowledgment Number are applied to enhance the reliability of data when transmitting as well as to consolidate data divided into small packets during the sending process, these are the 32 values The bit is specified in the header of the packet.
Connection (Links)
The data is only transmitted when the connection is established, there are two types of connections that are passive open (when the application listens to the connection: for example, the netcat application listens to a connection on a certain port) and active open (the application requires TCP communication with a remote host is in passove open mode.
Set up links
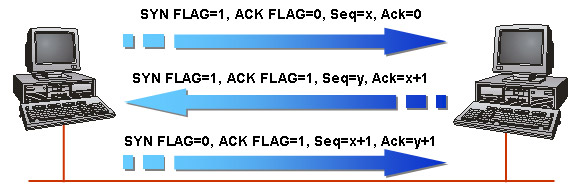
Before the data is transmitted as well as the active events and ack numbers, the link must be initialized, this process is called a three-way handshake, this process consists of the following three steps:
1. Host A sends a segment to Host C with information :
SYN = 1 (Session is synchronized)
ACK = 0 (There is no value in the ACK field, so this flag has a value of 0.)
Sequence Number = x, with x being a value. (x is the ISN of Host A)
Acknowledgement Number = 0
2. The Host C receives this segment and responds to Host A the following messages :
SYN = 1 (Session is still synchronized)
ACK = 1 (Verification flag has been set)
Sequence Number = y, with y being a value. (y is Host C's ISN)
Acknowledgement Number = x + 1 (The Sequence Number from Host A is added 1.)
3. Host A receives the segment from Host C and responds to Host C information :
SYN = 0 (Session has been synced; more requests are not needed.)
ACK = 1 (Ack set response to SYN from previous segment)
Sequence Number = x + 1 (This is the next order in sequence.)
Acknowledgement Number = y + 1 (Number of sequence numbers from Host C is added 1.)
End the link
Similar to the initialization of the link, the link termination process also includes many steps. There are two types of TCP endings that are graceful (using FIN flags) and include four steps because TCP communication is full-duplex communication and non-graceful (using the RESET flag). And like the initialization process we have 2 types of Passive Close and Active Close. Here are the steps in the graceful connection termination:
1. Host A sends a termination session to Host C with information :
FIN = 1 (The Session will be limited.)
ACK = 1 (Here are some numbers, based on current information)
Sequence Number (FIN number) = s (s is a value based on current information)
Acknowledgement Number = p (p is a value based on current information)
2. Host C receives Host A segment and responds to information :
FIN = 0 (This segment does not require a termination of the session.)
ACK = 1 (Segment includes some ack)
Sequence Number = Not Present (Since there is no FIN, there is no required sequence number)
Acknowledgement Number = s + 1 (This is the response to the FIN of Host A FIN)
3. Host C sends a session termination in the opposite direction to the information :
FIN = 1 (Session will be limited)
ACK = 1 (Here are some ack)
Sequence Number = p (p is a value based on current information)
Acknowledgement Number = s + 1 (Same as in the previous segment)
4. Host A receives the segments from Host C and responds to the information :
FIN = 0 (Segment does not require a termination, no SYN)
ACK = 1 (Segment includes some ack)
Sequence Number = Not Present
Acknowledgement Number = p + 1 (This is the number of Host C sequence numbers added 1)
Now the communication link between the two hosts has ended.

Port (Port)
The port number is defined in TCP and UDP header, is a 16 bit value from 1 to 65535. There are three main types of ports: well know, register and dynamic:
Well Know Port is the port in the range of 1 -1023, only users with administrator rights can open or close the ports well know. You can refer to these ports at www.iana.org/assignments/port-numbers
Register Ports are ports from 1024 to 49151. These are the ports that users can define and apply to their applications, which are not defined and controlled by any organization.
Dynamic Port is also called private port from 49152 to 65535. Any internet user can use these ports.
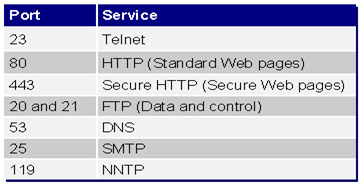
Some well know port and service:
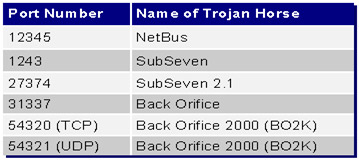
Some ports are used by famous trojans:
In the next article we will introduce network monitoring methods with common programs like Ethereal, WireShark and Network Monitor. Network monitoring is essential for system administrators because it not only helps network administrators not only diagnose problems to make corrective measures but also detect dangerous packets. Danger comes from Trojans, viruses or attackers.
-------------------------------------------------- -----------------------
Author: Nguyen Tran Dai Hung - Nguyen Tran Tuong Vinh
Comments may be sent to Administrator@Security365.Biz
Website: http://www.security365.biz
According to the official SCNP (Hardening Network Infrastructure) documentation