PKI Tutorial - Part 4: Troubleshooting
 Part 1: Planning
Part 1: Planning
 Part 2: Design
Part 2: Design
 Part 3: Installation
Part 3: Installation
Martin Kiaer
In the previous installments of this series, we gave you an overview of how to prepare, plan and design Microsoft PKI. We also gave you a bit of a technique to show you how to install PKI based on Microsoft Certificate Services in Windows Server 2003. In this final section, we will give an overview of how to maintain and engrave. Restore your PKI with some basic but very valuable tools.
Hop dung Cu
One of the components is very valuable to you and the PKI is a toolbox, which includes many tools. These tools will help you maintain PKI stability and solve problems quickly, without much trouble. However, this toolbox is not easy to perform task tasks immediately because it doesn't have many tools available, so use them best with what we have. Below we list your options for Microsoft PKI toolbox (not in order):
- Certificate Services (certsrv.msc) - This management interface includes the main functions you will need when configuring and maintaining PKI
- Certificate Templates (certtmpl.msc) - This interface is used to maintain and protect certificate templates
- Certificate Manager (certmgr.msc) - This interface is used to control certificates installed on the current computer or user.
- Certutil.exe - The command-line certificate utility is implemented as the Certificate Services MMC plus
- Event Viewer (Eventvwr.msc) - This tool is very important when troubleshooting PKI
- Enterprise PKI tools (PKIview.msc) - MMC-based PKI health tool.
- Capimon.exe - Allows administrators to check CryptoAPI calls of security applications and its results.
All of these tools are very useful for PKI, but they also have some important information to help you troubleshoot PKI. The best way to troubleshoot this PKI is to use a pre-structured process. This method is introduced below:
1. Always start troubleshooting by checking the event logs. This may seem obvious but almost all PKI related errors will be written to the event logs. Therefore, you can display error messages from different programs such as the Certificate Services MMC, and the event log is still the best way to read and troubleshoot PKI-related errors.
2. Use PKIview.msc tools to get an overview of your PKI status. PKIview.msc will show some of the most common errors, including an expired or missing CRL or an invalid CA certificate. If everything seems to be good for this tool, you can move on and focus on specific certificate-related issues such as security settings on the certificate template, etc.
3. If the error is not obvious or is difficult to fix, then seek help from our resource list at the end of the article, or find solutions through support.microsoft.com , groups or forums.
Another thing that may help you is to have a checklist after installation and during maintenance. Here is an example that you should consider for reference:
- What is the availability of your PKI and root certificates?
- Is CRL available?
- Will the issued certificates work properly?
- Do components or infrastructure applications based on certificates from PKI work properly?
- How does performance on systems use PKI certificates?
- Are there many error messages related to the installed certificates on the computer?
Go ahead and look at some of the utilities from our toolbox, how they can make it easier to implement your PKI aspect.
Certificate Services and Certificates Templates MMC Snap-in
The Certificate Services MMC snap-in (certsrv.msc) is the main PKI administration interface. You should invest some time with this MMC Snap-in and get familiar with the tool as it can help you gain a deep understanding of Microsoft's PKI world. With this snap-in, you will understand the AIA, CDP, V2 certificate templates, etc. and how they relate to some of the areas introduced in the previous sections. Its help is also very valuable, it includes many small parts that allow for the best operation (like many other help files in Windows Server 2003). Most problems with PKI are often related to permissions issues, where the certificate is being used or the availability of the CRL. So let's look at some examples where this tool can be of great help when troubleshooting your PKI.
One of the most frequent errors you will see in the PKI is an expired or inaccessible CRL. The quick way to solve this problem is to publish the CRL from the Certificate Services MMC, but this can also be edited from the command line.

Figure 1: Announcing the CRL
You should make a habit of checking whether a certificate has been issued by checking the 'Failed Requests' submenu on the left pane of the MMC interface. From this menu, you will be able to investigate why there is an error related to failure when issuing a certificate. Usually this error will be difficult to read from the 'Failed Request' section. A better way is that this error will be added to the application log. Since we can easily copy an event log input from the Event Viewer over the Certificate Services MMC, we should choose this method to check for PKI-related errors unless you use it. delegate admin type and custom MMC.
Another error is false security settings on certificate templates. You can change the security of certificate templates from the Certificate Services MMC by right-clicking Certificate Templates and selecting Manage or starting a new MMC, where you add Certificate Templates (certtmpl.msc) snap-in. With the Certificate Templates MMC, select the properties of the certificate template you want to use. Then click on the Security tab and make sure that the correct security group is allowed to receive a certificate by activating 'Read' and 'Enroll' terms (loaded) for that group.
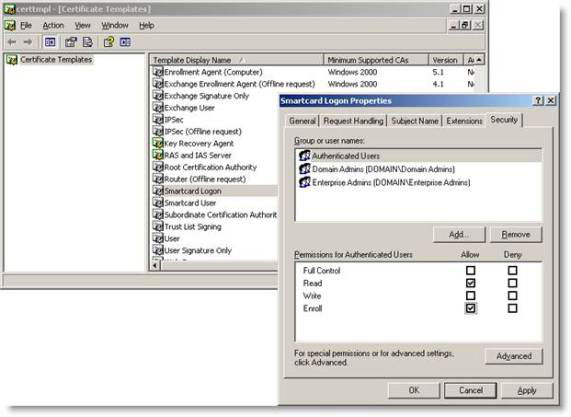
Figure 2: Check if the certificate template has the correct security settings
PKIview.msc
One of the most valuable tools for your PKI is PKIview.msc, which is available in the Windows Server 2003 Resource Kit. With this tool, you can check the status of PKI. When you start the graphics tool, you'll see different directives that tell you everything is fine with your PKI. Although the yellow indicator will tell you that the certificate or Certificate Revocation List (CRL) is about to expire. If you see red errors, red indicates that CRL or Authority Information Access (AIA) locations are out of control. Red errors may also indicate that a CA is not trusted. If you are in this situation, right-click on the error and click 'Copy URL' and paste the URL into the web browser, if it is an out-of-control HTTP location or use a tool like Windows adsiedit.msc Support Tools to check whether the published CDP location is canceled or trusted.
This tool has a lot of possibilities, you should at least run this tool once a week to ensure the status of the PKI. The details in this error will quickly indicate exactly where the error is, although it will not give a correct solution. So you need to do some detection work with some of the tools mentioned in the toolbox at the top of this article or search on Google for the event that appears in PKIview.msc.
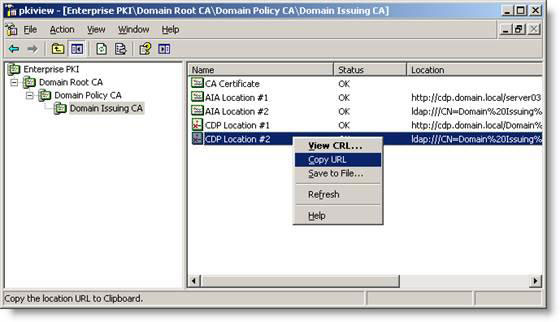
Figure 3: PKIview.msc, a great tool for troubleshooting
Certutil.exe
This is a command line utility that replaces the resource toolkit from Windows 2000 called Dsstore.exe. There are several advantages to using Certutil.exe. First, you can completely script and easily manipulate it when compared to all the tools in the PKI toolbox for configuration and documentation. and troubleshooting. Another advantage not often mentioned is that it can run many data collection features as a regular user. This is indeed a great advantage for troubleshooting certificate issues; does not compromise the security of PKI. The reason why PKI troubleshooting with Certutil.exe will not compromise PKI security is because many configuration options are not available unless you have the necessary permissions (sufficient permissions).
Another advantage of Certutil.exe is the change management feature (classification). Many Certificates Services settings are stored in the Windows registry:
' My ComputerHKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesCertSvc '
Whenever you make a change to the PKI with the certutil –setreg parameter, the utility will display the old setting first and followed by the new setting later.
We will not learn all the different features and options of Certutil.exe, because they really have too much. However, enter 'Certutil -?' You will get a complete overview. A little suggestion here for you is that Windows Server 2003 Certutil.exe version can be included in Windows Vista, Windows XP and Windows 2000. All you need to do is copy the Certutil files. .exe, Certcli.dll and Certadm.dll are located on your Windows Vista, XP or Windows 2000 computer. There are no requirements for registering DDL files. Run the command line utility from that location.
Conclude
Implementing this problem can be many ways, but by using the previously structured troubleshooting process, you can quickly locate and determine exactly where your PKI is suffering from. lost. We have tried to introduce an overview and all the tools and utilities needed for your service, and we have also documented some examples of how to use these tools. However there are so many options available, this depends on how you mix and match the tools. The examples shown in this article are suggestions for your inspiration. In the list of extended resources listed below, you will see links pointing to valuable articles that will introduce a lot of troubleshooting options. With all the resources mentioned in this article, you will have a good knowledge to protect your status and run PKI well.
Additional information source
All PKI articles http://www.microsoft.com/pki
If you want to see how Microsoft does PKI, go to http://www.microsoft.com/technet/itsolutions/msit/security/deppkiin.mspx
And finally, the book - Microsoft Windows Server 2003 PKI and Certificate Security at http://www.microsoft.com/mspress/books/6745.asp
You should read it
- ★ What is a Certificate Authority? What is CA?
- ★ From today, owning Linux LPI certificate will be easier!
- ★ Apache 2 supports SSL / TLS: Step-by-step instructions (continued Part II)
- ★ Configure Windows Server 2008 to remotely access SSL VPN Server (Part 4)
- ★ What is Root Certificate? How is it used for online monitoring?