how to use Zoom, guide 4 ways to use Zoom safely
With the complicated situation of the Covid-19 epidemic, instead of operating in offices, offices, companies are tending to encourage employees to work remotely. Therefore, online communication platforms have become an essential tool for individuals and businesses to interact and exchange jobs. With a global market share of nearly 20% and over 12.92 million monthly active users, Zoom has become one of the most popular communication platforms used to organize conferences, meetings, meetings. learn etc . online. However, the explosive Zoom comes with the risk that it becomes an attractive target for hackers.

According to a report by Check Point Research, an organization providing information on cyber threats, recent attacks from outside to eavesdrop on meetings, private conversations, . done via the Zoom app, which could potentially result in personal data breach or business espionage.
So how can you enjoy the benefits of Zoom without making yourself the prey of cyber attacks? Here are some tips from experts from Vietnam Internet Security Corporation VSEC.
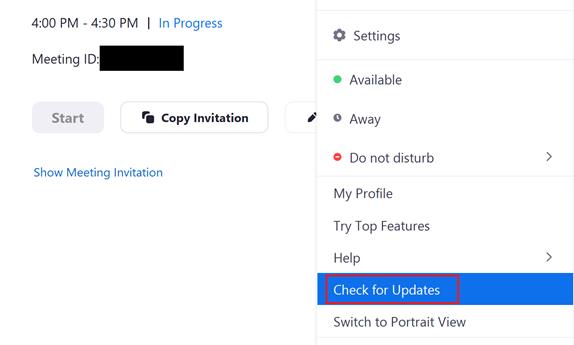
1. Always update to the latest version
To maintain effective security, the Zoom software must be updated regularly. The updates not only add new options and features, but also fix bugs and fix security holes found from previous versions - such as the ability to eavesdrop on the meetings. counter above.
It should be noted that the opportunity for hackers to attack does not end when the vulnerabilities have been patched, because users who have not updated the new version still exist. Only when users update the software and receive a Zoom patch, threats in the old version can be resolved.
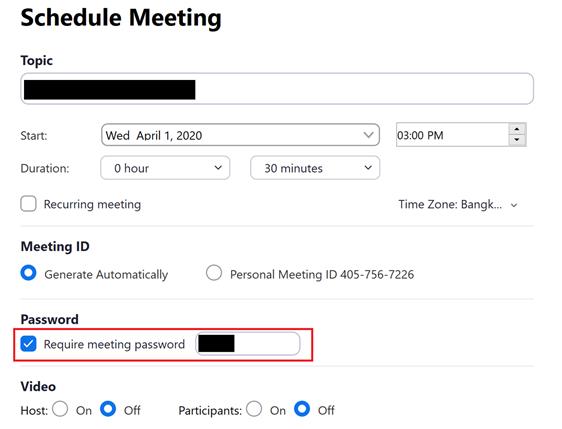
2. Use passwords in meetings
VSEC experts said that for each conference, Zoom will generate an ID of 9-11 characters that are random numbers. With brute force attacks - a technique for testing possible results to detect meeting IDs, hackers can steal IDs easily and infiltrate a conference without the host's knowledge. This attack occurs in the event that the conference does not set a password.
To avoid the above problems, Zoom offers the option to create a password for the meeting. So when strangers know the ID of the meeting, it is still necessary to have a password before joining the meeting.
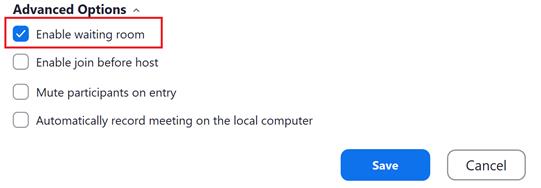
3. Using the "Waiting room" feature
To ensure that user meetings include only the participants that the host wishes. Zoom adds control of meeting participants - waiting room. After enabling this feature, each new participant will be on standby to allow the host to approve the right to attend the meeting.
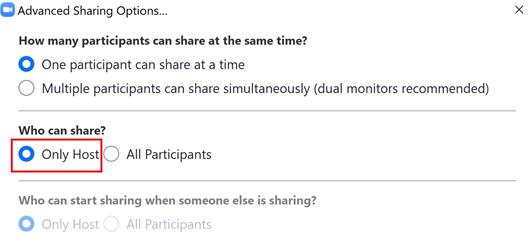
4. Manage screen sharing
To give the host more control as well as prevent participants from sharing screens with unwanted content. Zoom has provided the "Only Host" feature in the "Advanced Sharing Options" tab, which means that only the host can share content during the meeting.
In addition to some of the safety tips mentioned above, VSEC experts also recommend that users should be aware of Phishing attacks - disguising reputable individuals and organizations to steal information. your personal.
If you are using Zoom for the first time, make sure you are downloading directly from the zoom.us site, not any other domain (z00m.us, etc.). In addition, users do not download the Zoom software installer through any third party software provider.