How to Use Telnet on Mac OS X
Method 1 of 2:
Connect via SSH
-
 To ensure a secure connection, use SSH (Secure Shell)
To ensure a secure connection, use SSH (Secure Shell) -
 From the Shell menu, select New Remote Connection...
From the Shell menu, select New Remote Connection... -
 Enter a host name or IP address. In the field at the bottom of the New Connection window shown below type in the address of the server you wish to connect to.
Enter a host name or IP address. In the field at the bottom of the New Connection window shown below type in the address of the server you wish to connect to.- Note that you must have an account to log in.
-
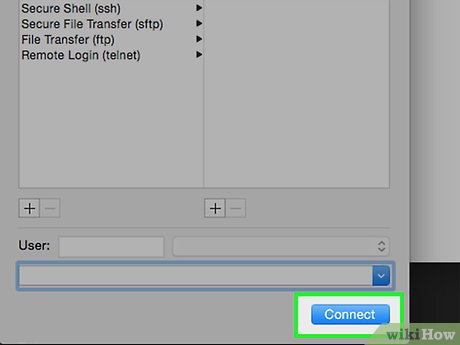
 Click Connect
Click Connect -
 You will be prompted for your password. Your keystrokes will not be displayed, for security purposes.
You will be prompted for your password. Your keystrokes will not be displayed, for security purposes. -
 Save your settings. Click the + sign under the Server column.
Save your settings. Click the + sign under the Server column. -
 Enter the host name or IP address of the server in the entry screen pictured.
Enter the host name or IP address of the server in the entry screen pictured. -
 Click OK.
Click OK. -
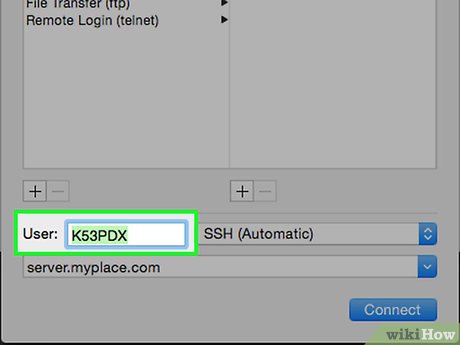
 Enter the user ID in the User field, click Connect, and your information will be saved.
Enter the user ID in the User field, click Connect, and your information will be saved.
Method 2 of 2:
Unsecure Connection
-
 Type Command-N. This opens a new Terminal session.
Type Command-N. This opens a new Terminal session. -
 Enter host name or IP address. Next to the blinking cursor, enter the appropriate login information as shown:
Enter host name or IP address. Next to the blinking cursor, enter the appropriate login information as shown:telnet server.myplace.net 23- Note that the port number may vary. Check with your server admin if the connection fails.
Share by
Kareem Winters
Update 04 March 2020