How to check the authenticity of Linux software with digital signatures
When you download software from the Internet, you must believe that the developer (s) program is not malicious. However, you also have to worry about hackers. There are many attackers who can hack a website and replace the software with a malicious version.
Think of a website hosting Bitcoin wallet utility. If an attacker seizes control and replaces the legal version with a malicious version, they can steal money from tens of thousands of users. Another valuable goal to attack is the operating system. This has happened with Linux Mint in the past.
So what can you do to remedy these situations?
Hash and signature
Developers with a sense of security will often pack files set up with checksums (software used to ensure the integrity of a file, after being transferred from another device) that you can Verification. Refer to the article: Check MD5 and SHA1 to check the integrity of the file for more details. However, the problem with these hash is that if a hacker replaces the files on a web page, he can easily replace the hash. This makes hash almost useless, especially if they are stored on the same server where the programs are located.
To make these checksum useful, many developers have added digital signatures to them with the help of public and private key pairs. Only the owner of this private key can create a signature and they can only be verified by the corresponding public key, published on the Internet. If the verification process is passed, you can be sure that the private key owner has 'signed' his software.
In order to bypass this security mechanism, hackers must steal private keys in some way, which is much harder to implement if the owner takes appropriate measures for security. And even if this key is stolen, the owner can disable it by revoking and notifying it. If this happens, when you download the public key and try to use it to verify the signature, you will be notified that the signature has been revoked.
How to verify the signature with GnuPG (GPG)
Gpg utilities are usually installed by default on all releases. If, for some reason, it is missing, you can install gpg with the commands below. On some distributions, if you get an error ' gpg: failed to start / usr / bin / dirmngr' dirmngr ': No such file or directory ', you need to install dirmngr too.
On distributions based on Debian, Ubuntu or Debian, run:
sudo apt install gnupg dirmngr For RedHat / CentOS:
sudo yum install gnupg dirmngr And on Fedora:
sudo dnf install gnupg dirmngr You can follow the example below to check how you verify the ISO installer Debian 9.8.0.
Download SHA256SUMS, SHA256SUMS.sign, and debian-9.8.0-amd64-netinst.iso. You may have to right-click on the first two files and select 'Save link as' or the equivalent option, in the web browser. If not, clicking on these files may only display content instead of automatically downloading.
Open the terminal emulator and change the directory containing the downloads.
cd Downloads/ Check the checksum
Wait for the ISO download process to finish. Next, verify the SHA256 checksum.
sha256sum -c SHA256SUMS 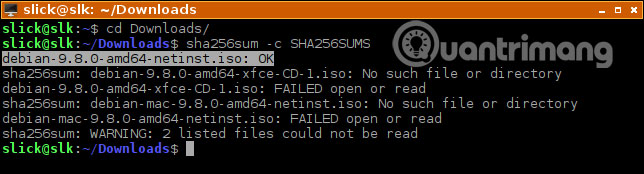
You will see the name of the file followed by the message 'OK' if the checksum is fine. To verify other checksum types, you have the following commands: sha1sum, sha512sum, md5sum. But you should use at least one SHA256SUMS or more, if available.
Some websites do not provide files like SHA256SUMS, where file names and checksum are grouped together for easier verification. If the page only displays sum, verify the file's hash with a command like this:
sha256sum debian-9.8.0-amd64-netinst.iso Use GPG to verify the signed checksum
In this example, the Debian team signed the SHA256SUMS file, with their private key and saved it in the SHA256SUMS.sign file. Confirm the signature with the command:
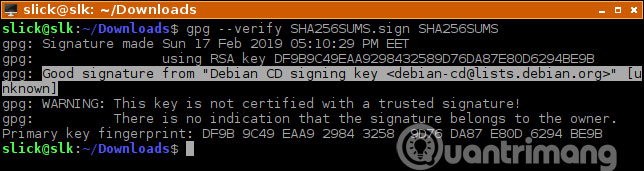
gpg --verify SHA256SUMS.sign SHA256SUMS You will receive a message like this:
gpg: Signature made Sun 17 Feb 2019 05:10:29 PM EET gpg: using RSA key DF9B9C49EAA9298432589D76DA87E80D6294BE9B gpg: Can't check signature: No public key This means you do not have a public key on your computer. This is very normal. You must import it from a keyserver.
gpg --keyserver keyring.debian.org --recv-keys DF9B9C49EAA9298432589D76DA87E80D6294BE9B If keyserver has a problem, you can use another keyerver instead. For example, you can replace keyring.debian.org with keyerver.ubfox.com.
But how do you know this key is legitimate? Unfortunately, to be absolutely certain, you'll need to build something called Web of Trust (WOT). Obviously, you don't have it at this point. But there are a few things you can do.
Search on the key's Google fingerprint (DF9B9C49EAA9298432589D76DA87E80D6294BE9B). If you don't find anything, try Google only the last eight characters (6294BE9B). A legitimate key will be mentioned on many websites related to similar software. Moreover, posts will usually last for many years because the safety-protected key will be used for a long time.
If you are not really sure, download the BitTorrent image and then verify the checksum and signature. With the way torrent works, it cannot replace files uploaded by hundreds of different users. Moreover, BitTorrent also has its own mechanisms for verifying the integrity of each data block it downloads.
Now you have a public key. Finally, you can also verify the signature:
gpg --verify SHA256SUMS.sign SHA256SUMS If you see the 'Good signature' message, it means everything has been checked. Don't worry about alerts. That's normal because, as mentioned, you don't have any Web of Trust set for public key.
As you probably already know, nothing is certain on the Internet. But it is certainly safer to take preventive measures and verify the electronic signature of the files you download. These measures can help you avoid malware. Many times users have downloaded Bitcoin wallet or operating systems that are infected with malware, but they can avoid trouble if they check the signature.
Hope you are succesful.