Practice applying electronic signatures to practice
Concept of digital signature (electronic signature):
Digital signatures or digital signatures can be visualized similarly to handwritten signatures. Electronic signatures are used in electronic transactions. From reality, digital signatures also need to ensure the functions: identify the owner of a certain data: text, photo, video, . and that data during the transfer process. changed or not.
In short, the main purpose of digital signatures is to prevent changes in documents and also to perform whether or not a document is actually sent by the subject to be traded.
Digital signatures use public key / private key cryptography (public key / private key cryptography).
You can provide your public key (public key) to anyone who needs it. But private key, only you are the holder.
Basic example: Mike has two keys, a public key and a private key. Mike gave his public key to Amanda, but kept his private key. When he wants to transfer documents to Amanda, Mike can confirm (sign) these documents using his own key and send them to Amanda. Amanda will then use Mike's public key, to be able to check the documents she received, actually sent by Mike.
First application: use electronic signature for Email
Let's embark on the following specific application to better understand how to use electronic signatures in a regular transaction.
In this example, we need two POP3 e-mail accounts.
The first POP3 e-mail account is set up for Mike (in this example Mike will send email and a second account to Amanda (Amanda will use to receive e-mails and check the digital signature to determine if these mails are from Mike)
Check that the Internet connection is ready for sending and receiving e-mails. Again, Mike is the sender (sender) and Amanda will be the mails receiver (receiver). In this example, the Storks Corporation website and their email accounts are maintained by a web hosting service on the Internet. The Web service provider provides the Storks company with email account information for Mike and Amanda, which will be used in this example. All employees who use e-mail at Storks use Outlook Express or Microsoft Outlook as their default Mail client program.
Install a POP3 email account
1. Mike uses Outlook Express as his default mail client. Log in to your Windows XP Computer (Pro-1).
Open Outlook Express from the Tools menu, select Accounts .
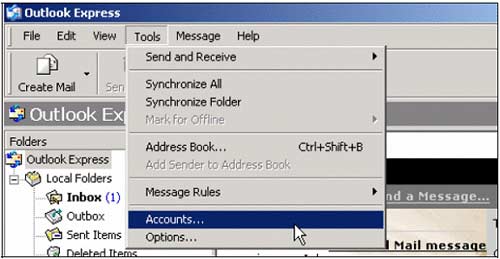
2. Click Mail tab then select Add , select Mail . The wizard will then guide Mike step by step to enter the name , email address and POP3 account information. information about mail accounts provided by ISAP or web hosting provider (web hosting).

Note: You need to install a second POP3 account for Amanda in the same way to check the electronic signature of Mike's email documents.
Rent a personal digital certificate (personal certificate) from a public digital certificate provider (public CA)
3. In the next step, in order to be able to send e-mail with electronic signatures, Mike needs to contact and hire personal digital certificates from a trusted digital certificate provider (such as Verisign or Thawte). . Renting a digital certificate from a 3rd party that is trusted is essential if you want to send secure email to an unrecognized recipient in your organization. Because normally, in an organization, to ensure the safety of internal transactions using digital signatures, that organization often uses its own secure digital certificate service (eg installation and deploy the Certificate Authority –CA certificate service, on Windows Server 2003). However, this local digital certificate provider is not usually used for electronic transactions with your non-organization transactions.
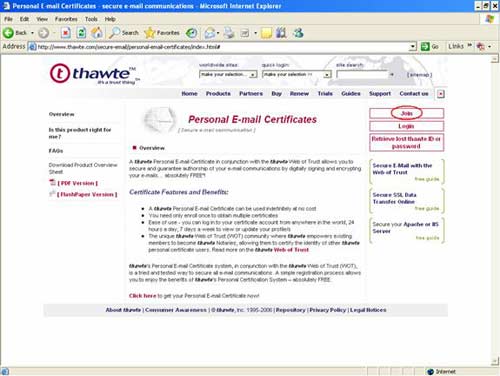
Because of these reasons, Storks decided to use the digital certificate of Thawte provider (www.thawte.com), to equip Mike in email transactions using personal digital certificates.
And Mike can sign up for a free Personal Email Certificate account here. Visit the following weblink and proceed to register to receive a personal digital certificate
http://www.thawte.com/secure-email/personal-email-certificates/index.html
Important note:
You must give Thawte personal information to identify you. This information is necessary and will be handled by Thawte's CA systems in the process of issuing digital certificates to you. Be sure to read all the information about providing digital certificates on Thawte's Website and know what needs to be done during the registration process.
You need to provide personal information and answer 5 questions for yourself. After you have registered, you will receive an email from Thawte with specific instructions on how to complete the application. number.
After this process, you will receive another email confirming that Thawte's personal digital certificate has been issued to you. Just click on the links on this Email and proceed to install the digital certificate. Click Yes and OK when the Certificate Installation Complete message appears.
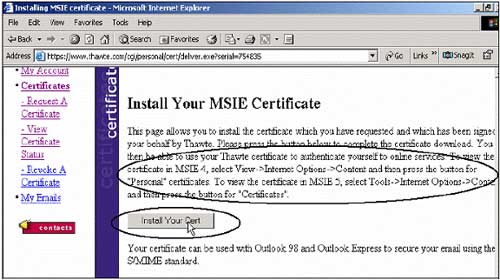
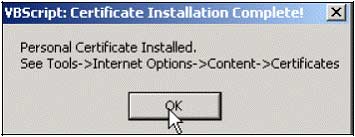
Confirm the email for emails
Once the personal digital certificate for the email has been installed, you can use it as a digital signature and encrypt the outgoing emails.
1. Open Outlook Express using the first POP3 email account created above. Select Tools , select Options and select Security tab . On this tab, we will have an option to encrypt and digitally sign your outgoing messages . Click Apply and OK .
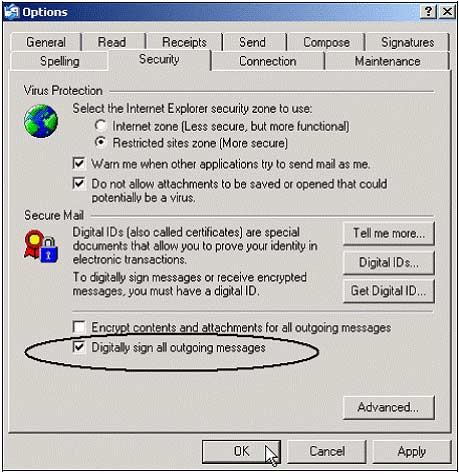
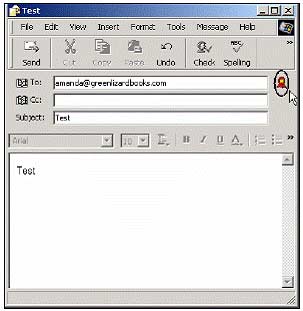
2. Click Create Mail and you will see the red ribbon icon in the upper right corner. This means that the email you send will be confirmed with a digital signature. fill in To: the recipient of the email address is Amanda (the second POP3 email you created)
Then click Send .
3. Go to Amanda's POP3 email account and open the email received from Mike. You will see the message that Amanda will receive similar to the screen below. Click Continue to see the actual message.
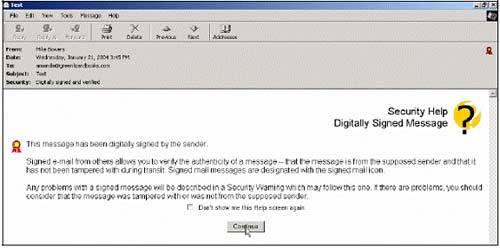
Notice the red ribbon in the upper-right corner of the mail. This tells Amanda that Mike has sent this mail using digital signatures. Click on the Red ribbon icon to see the digital signature from the sender (sender). Check and see that the mail content has not been changed and this digital signature is reliable. You can view information about the sender's personal digital certificate by clicking View Certificate .
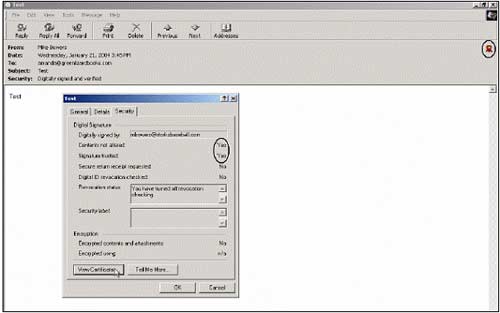
Emails encryption
Encryption is a security method that converts plain text data into an unreadable text format to ensure confidentiality and integrity ( integrity) and the authenticity (authenticity) of the data. When you encrypt email, the entire email will be encrypted, including messages and attachments. A digital signature will ensure the authenticity (true sender) and integration (data has not been changed) but does not guarantee confidentiality because the mail content has not been encrypted. chemical.
1. Open Outlook Express using Amanda's POP3 mail account. Select Tools , select Options. Click on the Security tab . Check Encrypt contents and attachments box for all outgoing messages . Click Apply and OK .
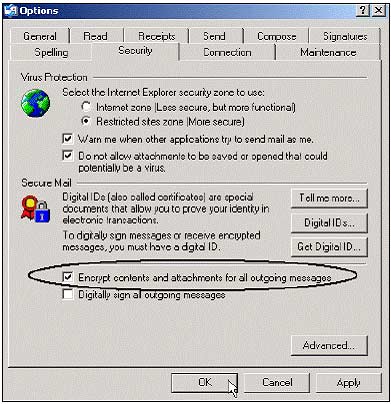
2. Click Create Mail and the lock lock icon will appear in the upper right corner. This means your email will be encrypted when sent. Enter the recipient's email address as Mike's POP3 account and click Send .
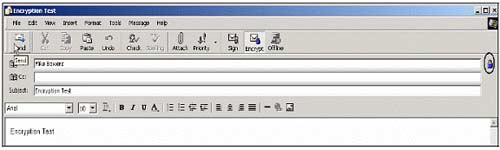
3. Go back to Mike's POP3 mail account and open the email that Amanda just sent. When you open the email, you will receive a message An application is requesting access to a protected item .
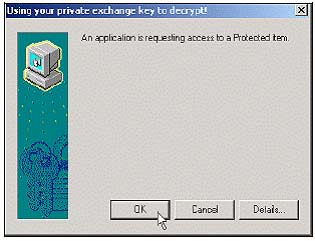
4. Click OK and then select Continue to read the encrypted email contents.
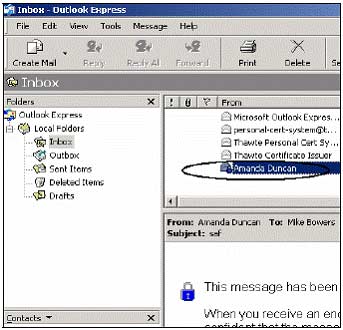
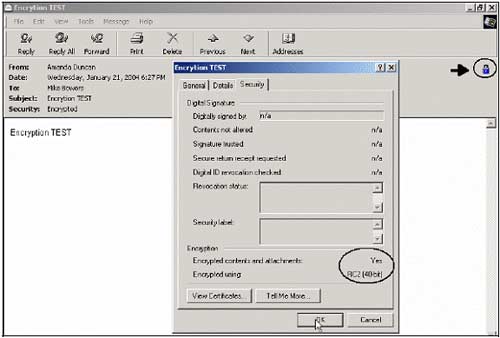
5. You can click the green lock icon to see more detailed information about encrypted email. Amanda did not confirm the digital signature for this message, so at Digital Signature all lines confirmed no use of n / a (not available).
Second application: Use PGP to encrypt files
Pretty Good Privacy (PGP) is a free software that provides PGP encryption capabilities in today's leading email and file transfer. However, if used for commercial purposes, you need to buy a commercial version of PGP that includes more features than the free version. The main purpose of PGP is to encrypt files to ensure safety when transmitted over the Internet.
With PGP Freeware, only the following limits can be used:
- Used for personal use at home, not related to profit-generating activities (as in the company's environment)
- Students at non-profit schools and students
- Charities, institutes, non-profit organizations
You can download the free version of PGP at the following weblink:
http://www.pgp.com/products/freeware.html
PGP installation
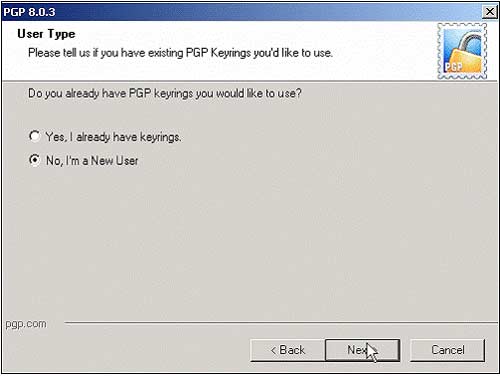
1, Log in to your Windows XP Pro-1 with Administrator and start the PGP installation process by double-clicking on the downloaded Installation File . Click Next , read the License agreement, click Yes . Read Me screen appears, click Next after reading this section. Select No, I'm a New User , because you're a new user, never created and used pre-existing keys (pre-existing keys).
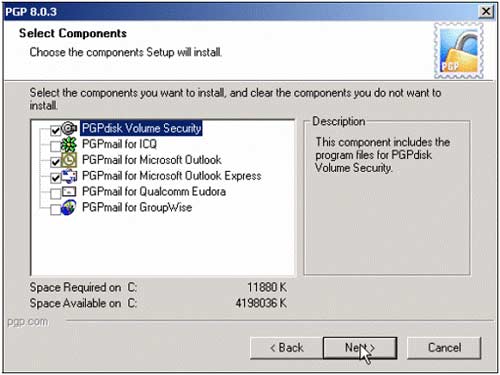
2, Leave the default values for Destination Folder and click Next . Select the components as shown, click Next . Click Next again and Finish to restart the computer.
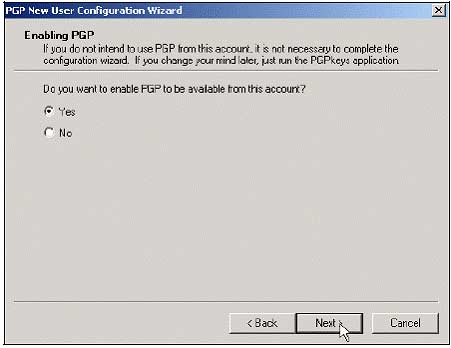
3, Log back into the machine with Mike's account (or if Mike is Administrator, log in normally as before).The PGP New User Configuration Wizard appears instructing Mike on operations. Click Next to continue. Select Yes then click Next .
4, Next select I am a New User . Create new keyring files for me . Click Next , then Click Finish to complete.
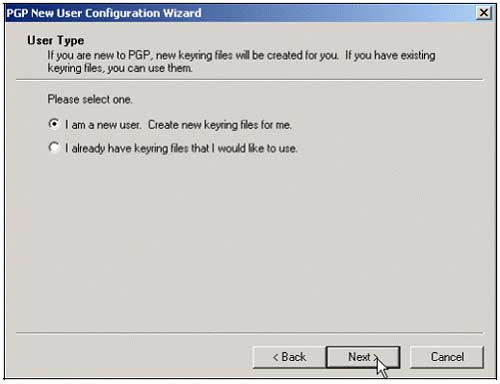
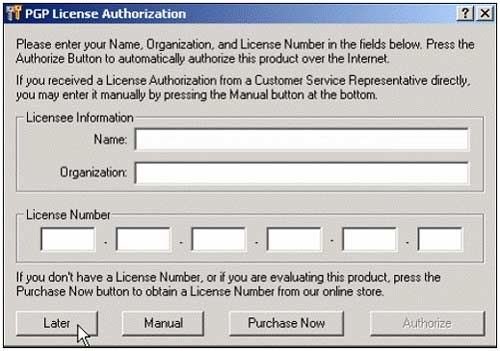
5, You will see the PGP License dialog box appear. If you are using a free, click Later version , if you want to purchase a license, click Authorize .
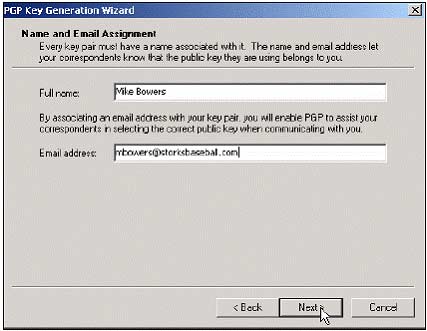
6, PGP Key Generation Wizard will appear. Click Next to continue. Fill in your full name, and email address, then click Next .
In this example is Mike's name and email address
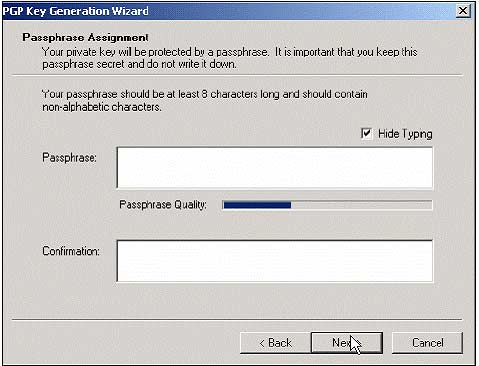
7, The next screen prompts you to enter the passphrase , the purpose of the passphrase is to protect access to the private key. A passphrase should be used safely (not easily guessed or detected).
Enter a passphrase and confirm (confirm), then click Next . And notice that you are Mike, the private key is created for you, and never forget your passphrase.
8, Click Next then, click Finish to complete the activation process.
Export public key (Public PGP Key)
Why need to export (PGP) public key. The simple answer is as follows. The goal of this example is how Amanda can encrypt a text file and then send it to Mike as an attachment via email. To do this, Amanda needs to have Mike's public key.
Mike has installed and activated the PGP key, and then he will export his public key, and then transfer this key to Amanda so she can encrypt the text file and then send it back to Mike as an attachment. In contrast, in case Mike sends the encrypted files to Amanda, Amanda herself has to export the public keys and pass it to Mike, so that the secure transaction happens.
1. Right-click PGP lock located in the system tray and click PGPkeys again .
2. Click Keys and then Export . Fill in the file name and save it in any easy-to-remember place like the C: drive or the FDD 1.44 floppy disk. Mike saved the file to a floppy disk and transferred it to Amanda.
And Amanda will do the same.
And note in this practice example, the operation to install and configure PGP on Amanda's machine, will be similar to the operations you are performing on Mike's machine if Mike wants to send the data. safe by email to Amanda, and so Amanda will use PGP to activate her lock, then export the public key, save it to a floppy disk and pass this key to Mike, Mike will use this key to encrypt the data, then send data to Amanda
Enter the PGP key public key
Once Amanda has received the public key from the floppy disk, she needs to enter this key into PGP software .
1. Right-click the PGP lock from the system tray and click PGPkeys . Click Keys and select Import .
2. Select the key under the file name, Mike Bowers saved it to a floppy disk and click Open .
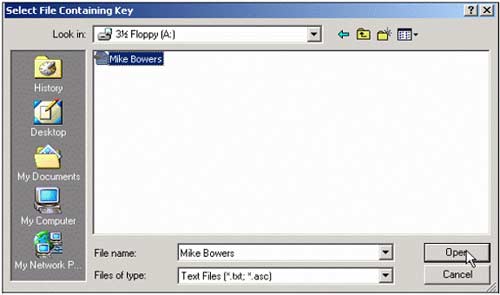
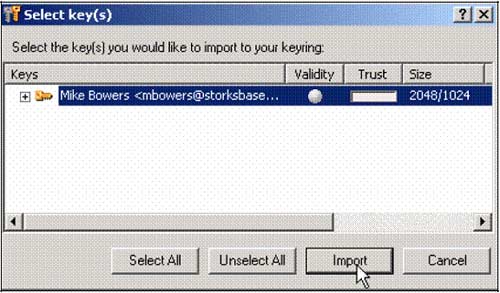
3. Select Mike Bowers and click Import . Exit PGPkeys window . And note: in the opposite direction, Mike also needs to enter Amanda's public key for me.
Check that file encryption will be sent using PGP encryption
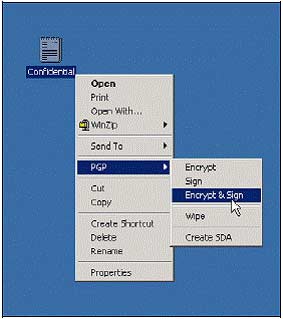
1. Create a text file on the desktop called Confidential . Right-click the file and select PGP , select Encrypt & Sign .
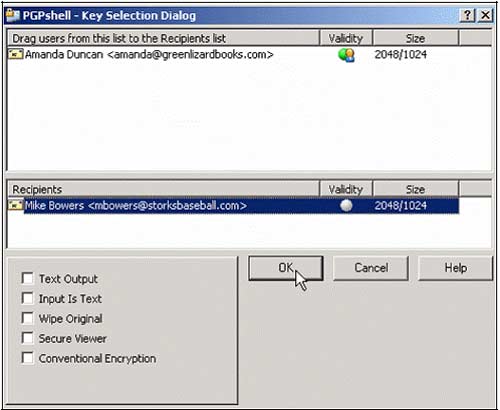
2. Select the recipient as Mike Bowers (recipient) and click OK .
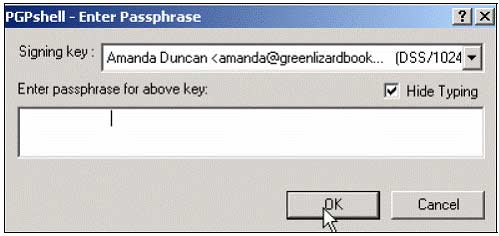
3. Fill in Amanda's passphrase and click OK . The purpose of this is to confirm that the file is encrypted so that Mike can be sure Amanda is actually the sender.
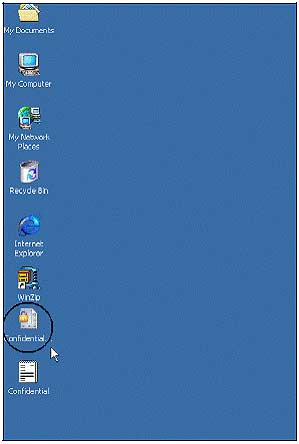
4. When the File is encrypted using PGP, the file icon will change as shown. And only the following people can open this file: Amanda (with his passphrase), Mike (with his passphrase) and someone steals Amanda or Mike's passphrase.
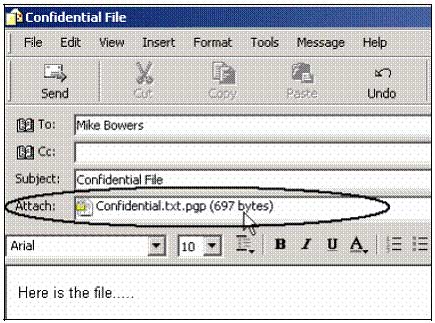
5. Amanda will then send this encrypted file as Attachment attached to an email to Mike.
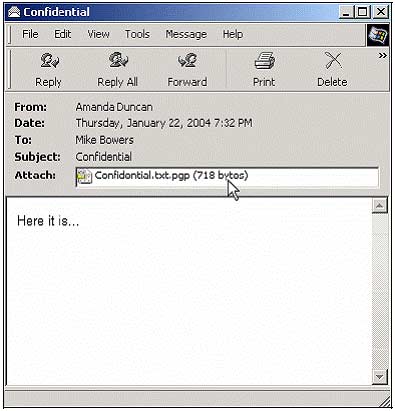
6. Then when Mike proceeded to receive the mail and save the attachment on the Desktop.
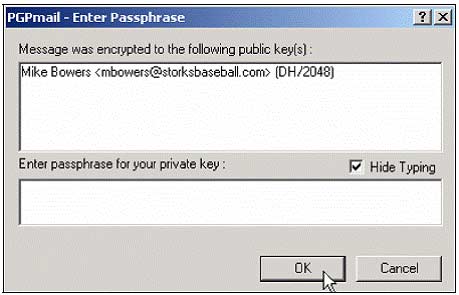
7. When Mike double-clicked on the encrypted file, he needed to input his exact passphrase and click OK . If the passphrase is correct, the file will be decrypted.
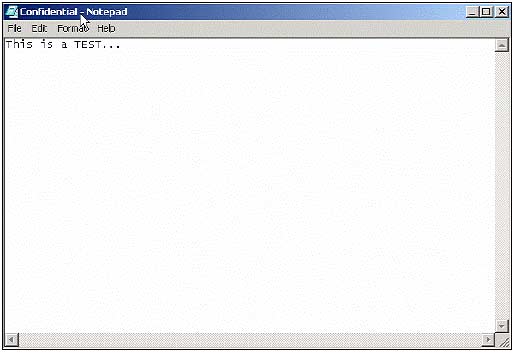
8. Mike opened the file and saw the contents
PGP - Wipe (PGP's permanent File deletion feature)
When a File has been deleted the system usually still exists on your hard disk and can easily be recovered with just a little data recovery software and skills. This is quite dangerous, because these data can be exploited. Deleted information is still present on the hard disk and is often lost only if overwritten with new information, even in this case, with some data recovery tools still recoverable. feedback And PGP has provided us with a feature, permanently deleting data, PGP's Wipe, the specified information deleted with PGP wipe, forever without a chance to recover. Using the method write dd9e2 on the information deleted some random information at specified times.
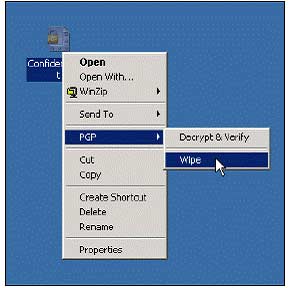
1. Mike will check this feature on his computer. Right click on Confidential file and select PGP , choose Wipe .
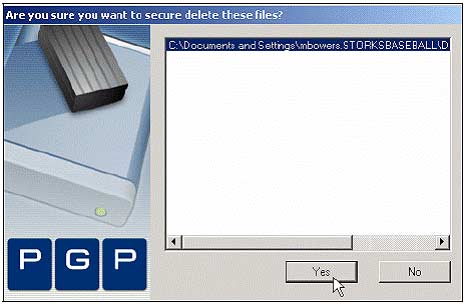
2. Select the file listed and click Yes . The file will be permanently deleted.
Ho Viet Ha
Network Information Security Vietnam.
www.Nis.com.vn
Email:NetworkSecurity@Nis.com.vn