Microsoft Forefront TMG - Publish RD Web Access using RD Gateway (Part 2)
In the second part of this article series, I will show you how to publish Remote Desktop Web Access with the Remote Desktop Gateway via Microsoft Forefront TMG.
[#RelatedNews (7) #]
In part one, I showed you the configuration of the RD Web Access and RD Desktop Gateway services and in this section we will introduce how to publish RD Web Access with Forefront TMG and how to access RD Web Access via a Windows 7 client.
The article assumes that the Remote desktop Session Host feature is properly installed and configured, so we only need to install and configure the Remote Desktop Web Access and Remote Desktop Gateway components.
First, we need to issue a certificate named webmail.trainer.de. This name will be used by clients in the Internet to access the RD Web Access or RD Gateway service.
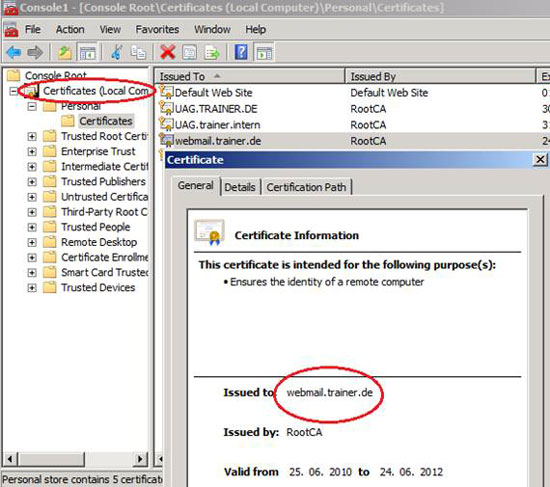
Figure 1: Import the Webserver certificate for TMG publishing
The next step is to create a Webserver or Exchange Web client publishing rule. You can use both publishing rules.

Figure 2: Create a new Web publishing rule
Select Allow as the rule's action.
Select Publish a single Website or Load Balancer
Use SSL to connect to the Published Web server and enter the internal Hostname of the server you want to publish.

Figure 3: Enter the site name inside
You can restrict access from clients to certain paths, with RD Gateway access you need to allow path / RPC / *, the path used by RPC via HTTPS proxy service. After the wizard has finished, we must change the publishing rule to also allow access to the / RDWEB / * path, which will be used by the RD Web Access feature.

Figure 4: Select the / RPC path to publish
Now we have to enter the public Hostname used to access the published server from the Internet.

Figure 5: Enter the public Hostname
Next we need to create a new Web listener for RD access. Since we want to use SSL Bridging, select Require SSL Secured Connections With Clients . If there is only one IP address bound for the external interface on Forefront TMG, you do not need to change the Listener IP address. If there are multiple IP addresses for Forefront TMG's NIC interface, it is possible to select the IP address you want to use to publish the RD server.

Figure 6: Select Web listener
Now it's time to select the certificate that will be tied to the Web listener. Select webmail.trainer.de certificate
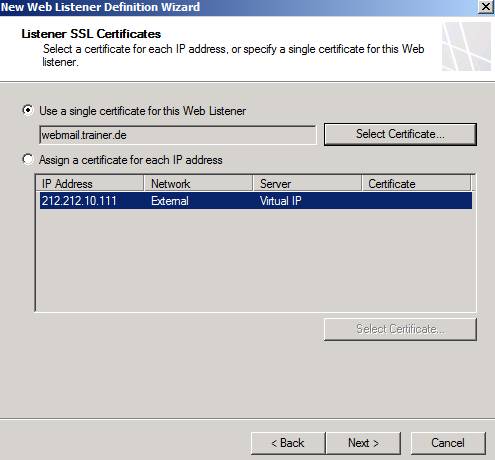
Figure 7: Use the Webmail.trainer.de certificate
The authentication method is HTTP Integrated Authentication with Active Directory.

Figure 8: Select HTTP as the authentication method
Authentication authorization method is Kerberos constrained delegation (KCD). We must also enter the correct Service Principal Name (SPN). The SPN for this lab environment is HOST / trainer-dc.trainer.intern.

Figure 9: Select KCD and enter SPN
The rule applies to all authenticated users.
Click Finish . You will see an additional message stating that you must configure the TMG Server to allow authorization for RD server.

Figure 10: Notice for additional KCD configuration
Click Apply.
After the configuration changes take effect, we must change the publishing rule to allow access to the sub-path / RDWEB / *, the path used by the RD Web Access feature.

Figure 11: Add the path / RDWEB as an additional path
As a final step, we must configure the Trust for Delegation settings. Open Active Directory Computer and Users Snap In on a Domain Controller and navigate to the Computer account of Forefront TMG Server, select the delegation tab, select Advanced and select Server with RD services and choose Host as the service type.

Figure 12: Trust RD Gateway for Kerberos Delegation
Configuring Forefront TMG is finished, we can now configure the Windows 7 client in the Internet to receive RD Gateway and RD Web Access.
Launch the Remote Desktop connection utility (MSTSC.EXE) and enter the public domain name as the name of the computer you want to connect to.

Figure 13: Connection to public hostname
Click Advanced and settings in the Connect from anywhere section

Figure 14: Connect from anywhere
Specify the RD Gateway settings and similar to the RD Gateway Server, enter the name of the internal Server with the RD Gateway role installed. Make sure that the Bypass RD Gateway Server for local access dialog box is checked.

Figure 15: Enter the RD Gateway INTERNAL Server name
Now create a connection to the RD Gateway Server. If the connection is successful, you will see another icon in the Remote Desktop console, indicating that you connect via the RD Gateway service.

Figure 16: Connecting via HTTPS to the RD Gateway service
If you are the administrator of the RD Gateway server, you can also check connections from the client to the RD Gateway using the RD Gateway Manager console below the Monitoring button as you see in the figure below.

Figure 17: Check the connection with the RD Gateway manager
Now open this website from the Windows 7 client and you will have access to RD Web Access after successful authentication. Depending on the RD Web Access and RD RemoteApp settings that you can access the application via the web interface, access will be tunneled through the RD Gateway service.

Figure 18: RD Web Access via Internet
Conclude
In this article, I have shown you how to publish the RD Gateway service and the RD Web Access feature with the help of Microsoft Forefront TMG, and also showed you how to access the RD service. Gateway with Remote Desktop client and how to access RD Web Access with the web browser on the client.
You should read it
- ★ Use the Security Configuration Wizard with TMG 2010
- ★ Microsoft rushed to release security updates for Windows XP, Server 2003
- ★ Microsoft stopped supporting SQL Server 2008 and Windows Server 2008
- ★ Configure Windows Server 2008 to remotely access SSL VPN Server (Part 3)
- ★ Learn the new Network Policy Server feature in Windows Server 2008