Network analysis with Colasoft Capsa
2 years ago, a computer worm appeared and raged around the world under the name Conficker . They are primarily aimed at system vulnerabilities based on operating systems, user accounts . and this process will generate countless authentication and identity requests to Active domain controllers. The directory, so the official account will not be able to log in because of the previous false signals.
To overcome this problem, Microsoft released MS08-067 patch to apply to computers that were patched by KB958644. But for large-scale businesses or companies, it is difficult to apply this method without a reasonable solution. The administration department must assign staff to perform this operation on each computer in the network, and with this manual method, the occurrence of errors or errors is unavoidable.
One of the most popular support applications today is Capsa of Colsasoft. The program has a simple interface, easy to use - this feature is quite important for administrators. In the main control panel, you can easily determine the diagnostic levels according to the instructions. Then, configure it in detail when applying within your system with available forms and metrics. And the fact that not all administrators are proficient in configuring hardware devices, so they desperately need good support tools in this. With Capsa, users will not have to spend too much time and formulas to configure:
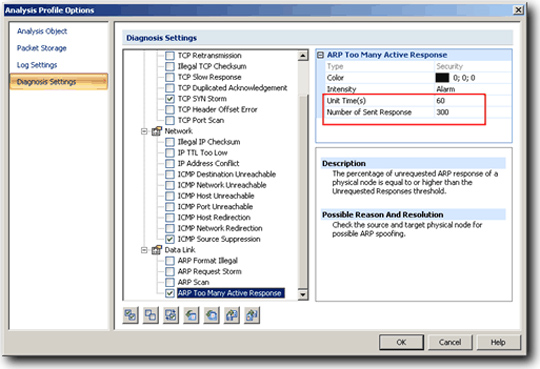
Setting up the applications needed to analyze the entire network operation requires cost not cheap. When using Capsa, you will save a lot of time, cost and effort compared to before. The analytical results are very detailed and scientific, the accompanying Matrix feature helps managers keep track of the entire data flow situation in the network, they just need to hover over the displayed display lines. corresponds to the thickness - thin on the screen, you will know exactly which connection is causing network congestion in the system:
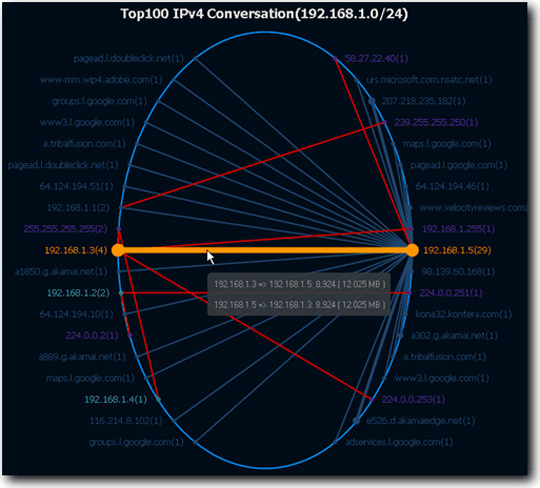
Currently Capsa has many versions, but the Free version does not have the function to create reports.