How to protect bank accounts, Facebook, ... from appropriation
Recently the incident of appropriating bank accounts, Facebook, Gmail, . again rang a warning bell about the status of stealing personal information. And the reason for this hijacking is that malware fake the extension (extension) on Chrome browser, stealing account information from personal computers.
You can see that the method of stealing information this time of the hacker is much more sophisticated, surpassing Google, taking advantage of fake extensions to easily steal personal information. So how to be vigilant and avoid installing right types of malware containing malware that steal information?
1. Check the software before installing:
The fastest way to attack and infect malware is through pirated software forms. Be wary of cracked software or files appearing online. Finding software from mainstream sources, the software's home website is essential. In addition, before installing software, users should scan the virus to decide whether to use it or not.
We can use the Virustotal website to scan files, so we can determine the safety of installation files through popular software scanners such as McAfee, Symantec, Kaspersky, AVG, BitDefender, .

2. Be wary of strange plug-ins on Chrome Web Store:
As mentioned above, the current personal account hijacking and hijacking incident started with a fake extension installed on Chrome. Users will receive a link to install the plug-in on the Chrome Web Store to continue their work, and of course no one will suspect that the extension is fake.

However, in fact today, the number of fake extension exist is very much. The more dangerous these types of extensions use the same name as the real version, making the user "trapped" if not tested thoroughly. Therefore, before deciding to install an extension, please check the name, author name, and number of stars to avoid counterfeiting.
- How to distinguish real and fake gadgets in the browser
3. Do not install the extension from the source other than Chrome Web Store:
As well as dozens of dangers when installing software in places where the source is unknown, the extension at the source outside the Chrome Web Store is also at risk. Whether you have knowledge of technology or not, it's best not to install extensions in any other "floating" source, other than the Chrome Web Store.
4. Do not display many personal information at email:
The way email services are now part of the signature so that users can enter any of their personal information, such as name, company, phone number, even account number, .
However, the potential risk of account attacks may stem from the information displayed in the email that you consider to be extremely normal, so that others can easily contact when something is needed. Hackers have enough technical, professional, sophisticated to penetrate these personal accounts, and everything disappears after only a few seconds.
So limit putting too much personal information in the notes below the message as shown below as an example.
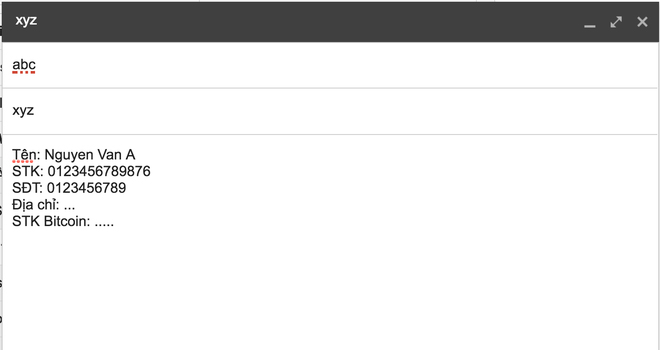
In addition to the personal accounts that are the most appropriated account, emails and administrative accounts of the company's internal system are no exception in this attack. In this case, companies should use two types of system security, including protected OTP code and VPN login to be able to secure the access IP address, access VPN password as a password matching OTP code.

With hackers' increasingly sophisticated attack capabilities, there is no other way but to improve our awareness of any software or extension. You should thoroughly check the software before installing, and do not disclose too much personal information if you do not want to become a victim of account hijacking.
Hope this article is useful to you!
You should read it
- ★ 5 best free security tools you may not know yet
- ★ Download the malware removal tool and clean up Malware Hunter PRO computer for $ 49.95 for free
- ★ Top 5 best Malware removal software 2020
- ★ Offers anti-malware software, protects IObit Malware Fighter 6 PRO computer, for $ 9.95, free of charge
- ★ 3 things that antivirus software can't do