Security experts discovered that the line appropriated bank accounts, Facebook, Gmail ... very large in Vietnam, you can also be a victim
Follow the crime track
Recently, in the process of strengthening the security of the company's system, a group of security experts from the Information Security department under VCCorp happened to find and trace the trail of an information-hijacking line. large scale in Vietnam. By taking advantage of the web browser, this group of hackers has a lot of account information in the system of many large organizations.

Specifically, on June 21, when an unusual sign was found in an admin account on a familiar website, the security team immediately went to the cause. After performing many business measures, they determined: account information was stolen from this employee's personal computer, by a malware in the form of extension (extension) on Chrome browser.
 Malicious extension pretending to be Internet Download Manager has been around for a long time on the Chrome Web Store.
Malicious extension pretending to be Internet Download Manager has been around for a long time on the Chrome Web Store.
Note: the author's name for this extension has been confirmed as fake, the goal is currently being clarified.
The amount of stolen information is unprecedented
Notably, this is an extension to replicate IDM extension - Internet Download Manager is very popular in Vietnam, can be used on the top 2 browsers Google Chrome and Coc Coc. Although not strange with this form of fraud, but the sophistication and professionalism in the way of action as well as the victim is Vietnamese, the experts have continued to trace very small traces. The results really surprised the group of experts - even though they were used to the world of cyber security many events.
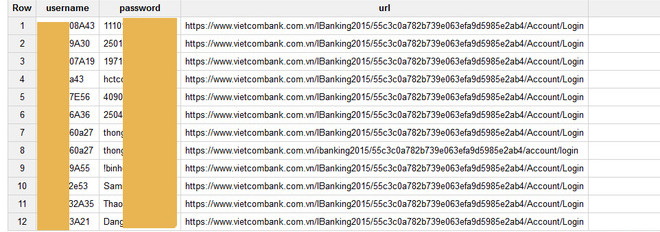
Hackers have captured a large amount of electronic accounts, including Vietcombank accounts
According to preliminary statistics, this hacker group has stolen login information (Username / Password) of about 55,000 Facebook accounts, 6,000 Google accounts, 5,000 Yahoo accounts and the most frightening is over 5 million cookies of universal pages. variables like Facebook, Google Mail, Yahoo Mail, Hotmail or even PayPal. With the hacker group owning cookies, if you are careful to use the 2-layer security feature, please give condolences, they can still completely take over your rights.
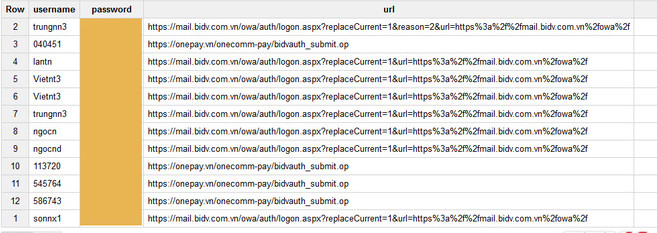
Many banking customers are also victims of hackers
Experts also note that this type of malware has existed for a long time but has not been captured by antivirus software and prevented because of mischief in the mode of infection. Users can "accidentally" infect this malware via two main routes:
1. Infection through the release of pirated software (crack):
When users download pirated software from any website (uploaded by hackers), in the crack file will attach a task execution file in the following order: turn off the browser (Chrome / Coc Coc) if running , create a connection to the extension page and finally download the extension and install it in the victim's computer.
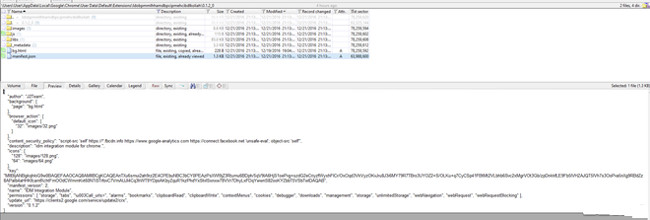
The log logs that the executable file automatically downloads and installs the extension.
2. Using curious links (links):
Previously, by circumventing the law, hackers have posted 11 different versions of this fake extension on the Chrome Web Store. Hackers will spread many curious links, the victim after clicking will get invited to install a "plugin" (to see the content, to use the web faster, etc.). Because the extension exists on Chrome Web Store properly, most users will accept the installation.
This extension has many rights that can be abused on bad and unnecessary.
Here the hacker continues to take another name in the author section.
How hackers can upload up to 11 different versions of this malicious extension and overcome many security tools, due to the framework of a limited article, we will provide details for you. read on the next lesson. Going back to the incident, this extension after being installed will steal the victim's login information when accessing all websites, as well as recover all user cookies sent to the hacker server.
So when you read this article, readers should immediately take the following steps, especially when you find yourself having the same behavior as what is mentioned in the 2 ways of infection above:
- Check the extensions in your computer browser, you can use the same tools as in this article.
- If there are suspicious signs such as using unnecessary permissions at any extension, erase it.You can refer to the meaning of extension permissions at this address .
- Change all passwords in all your electronic accounts.
At the same time as checking your computer, readers should actively share this information to those around you, especially those with little knowledge of technology. Don't let bad guys take over people's information, or use them to serve more dangerous purposes.
We will give detailed information on how security experts find out the culprit group in the next articles. Looking forward to your attention.
Follow genk