Compare U2F and UAF security standards
U2F (Universal Second Factor) is a 2-layer security authentication standard that uses external hardware (USB, bracelets .) so the level of security will be higher than sending codes via email or phone number. Today, TipsMake.com will help you learn the basics of this new form of security and compare it with UAF standard (almost fingerprint sensor on devices of Apple and Samsung).
About U2F
2-layer security is a basic way to protect important online accounts. This could be an email account, a cloud storage account, an online bank account or an account to log in to the company's internal web site. Normally, applications or services that support 2-layer security will require you to log in with the following steps:
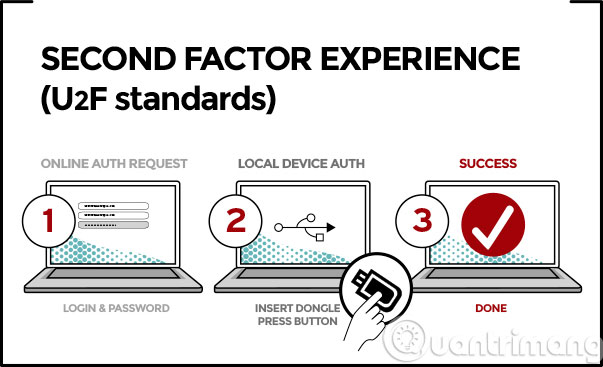
- Open the website / service to log in, type in the username and password as usual
- After that, an authentication code will be sent to you in different ways: be it via SMS, via email, read the code by phone or use a special app number.
- Once you have the authentication code in hand, you continue to enter the code on the website / service to login successfully.
Basically, the second security layer works to prevent unauthorized access to your account even if you have exposed all login details. For example, the person in your hand with your username and password to access the web banking cannot get the authentication code because it is only sent to your phone or only sent to your email. As a result, he will still be stuck outside the site and can do nothing, at least see some details about the balance but cannot make a money transfer.
Of course, if he also stole a phone or knew how to log in to an email account, it was a different story. Many people now share the email password for many websites and online services so bad guys can still access the mailbox and then get the 2-layer security code. At this point, the benefits of a two-layer security mechanism completely disappear.
Similarly, the phone is also very easy to steal and open SMS to see the 2-layer security code. Even without stealing, the bad guys can still see the authentication code sent to your phone when the message appears on the lock screen. It's that simple, it's extremely dangerous, isn't it?
U2F was born to address these restrictions. U2F uses HARDWARE to do the authentication code so you no longer have to worry if someone hacked the mailbox or took your phone anymore. The login must be done in the presence of the hardware, can not hack or hack in remotely, reducing many risks. Currently the most popular U2F hardware is a USB memory stick, which is very compact in size so it is easy to take with you wherever you go. In the future there will be more companies making U2F devices in the shape of rings, necklaces, bracelets, keys and dozens of other things.
U2F is developed by an alliance called FIDO ( Fast IDentity Online ), which has the participation of Google, Microsoft, PayPal, American Express, MasterCard, VISA, Intel, ARM, Samsung, Qualcomm, Bank of America and many other big companies. As of June this year, FIDO has 200 members from many different countries. FIDO is currently very active in promoting U2F, from hardware to software and in the future it will appear everywhere.
Principle of operation
When you need to log into an online service, for example Gmail, you still have to enter your username and password as usual. In the next step, you will be asked to pin the U2F-compatible USB drive to your computer. Chrome browser instantly detects the device's presence and uses encryption technologies to retrieve data from it ( you'll have to press a button on the USB drive ). Chrome continues to confirm whether the data is correct, is valid and if everything is fine, you will be logged into Gmail.
The reason you still have to enter your username and password in the first step is to prevent someone from breaking into your account just by stealing the key. It's also true, because it's like "2 classes", it's like a class.
In the process of authenticating Chrome, there are a lot of things going on to ensure your safety. First, the browser will check to see if it is communicating with the real website via https protocol. This helps prevent you from using double-layer security with a fake website. Next, the browser sends a code from your USB drive straight to the website, so in theory, an attacker will not be able to get this code while the data is being transmitted.
According to the U2F configuration, in addition to entering the full password as usual, the website can also give you the option to enter a short PIN then press a button on the USB device to continue logging. This way you can simplify remembering passwords as well as saving more time during the use of the service (because you have to type fewer characters).
Which websites support U2F?
Up to the time of writing this article, not many websites, services and software have officially supported U2F. Chrome is currently the only browser that integrates U2F and it is available on both Windows, Mac, Linux and Chrome OS. Firefox and Edge are being integrated but don't know when to complete it. Some websites have used U2F including Google, Dropbox, Github websites. Hopefully in the future, there will be more large web sites supporting U2F.

And as mentioned above, in order to use U2F, you have to use a special USB drive, but you can't get the USB drive you have right away. These drives can be found on Google, Amazon and you can use the keyword FIDO U2F Security Key to search, prices range from a few dollars to a dozen dollars. Currently on the market Vietnam has not sold this type of USB.
Assuming you have already purchased a USB U2F drive, you can go to Google's 2-layer security configuration page and follow the instructions of the web to start using.
What about UAF?
UAF ( Universal Authentication Framework ) is another login standard developed by FIDO itself, but it does not need any password. That's why UAF is also called passwordless experience. UAF requires some kind of authentication method that is on the user's device itself and does not propagate outside (local). Some examples of local authentication measures are fingerprint sensors, iris sensors, face detection, and even microphone use for voice recognition. After registering with the online service, every time you need to log in, the user simply sweeps your finger through the sensor or brings your face close to the camera.
You can imagine the UAF the way Apple uses the Touch ID sensor to help us log into the App Store, or how Samsung uses the fingerprint sensor of Note 4, Note 5, S6, and S6 Edge to help you login to websites or buy PayPal without typing a password. Whenever authentication is needed, just put your finger on the sensor and everything else will be done automatically.
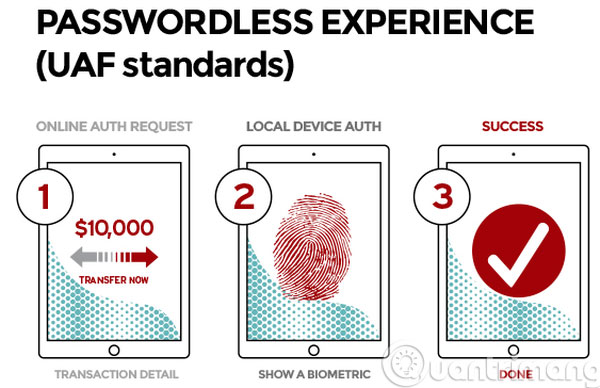
UAF is different from Apple and Samsung solutions in that it is standardized, so any website or application will be able to deploy this type of security quickly and easily, not from scratch, and not even depends on any platform or operating system. That will help UAF become more attractive and get more used services, as well as reach more users on a large scale.
UAF also allows to use a combination of PIN or password with local security, but then the experience will no longer be really passwordless but turn into two-layer security.
Data used to authenticate UAF standards, such as your fingerprint or your voice pattern, will always be on your own device and of course they are carefully encrypted. These sensitive data are not allowed to be exposed to the outside because then there is a risk of being stolen by hackers.
- Enhance USB security with USB Flash Security application
- Learn about DNS Hijacking and how to prevent it!
- Theory - What is Ransomware?
Good luck!
You should read it
- ★ Reveal the real photos of Galaxy Note 10: no 3.5mm jack and Bixby button, a selfie punched camera
- ★ The most noticeable 'leaks' about Galaxy Note 9
- ★ Samsung portrays four legends of the Galaxy Note series
- ★ The bender iPhone 6 Plus switched to testing Galaxy Note 4
- ★ 3 ways to take screenshots on Samsung Galaxy Note 4