Virus prevention experience
Concept
In this article, we only introduce some "familiar" viruses to home users. Some types are almost "extinct" because they cannot keep up with the development of computers, the Internet is only spread among infected people, the risk of harm is not high, easily detected. However, this is not good news because we must continue to "confront" with their next generation: more mischievous, more malicious, faster infection, the ability to destroy horribly .
Virus: A piece of code, a small program is written to perform something on the infected computer without permission or the user does not know. They have the ability to self-replicate, spread to other files, programs in the computer and to other computers. Computer viruses are often divided into several types: Virus files (Jerusalem, Cascade .) are viruses that infect files of some commonly used software in Windows operating system such as .com files. exe, .bat, .pif, .sys .; Boot virus (Disk Killer, Michelangelo, Stoned .) is a virus that infects the code in the boot sector of the hard disk; Virus macro (W97M.Melissa, WM.NiceDay, W97M.Groov .) infects the file in MS. Office. In addition, there are some other viruses such as bisexual virus (combining virus boot and virus file), virus master boot record .
Trojan horse: Programs that are disguised as harmless but hidden inside dangerous code to steal personal information, open ports for hackers to enter, turn infected computers into sources of spread spam or become a tool to attack a website, such as W32.Mimic. Unlike viruses and worms, Trojan horses do not have the ability to replicate themselves to spread, so they often combine with viruses and worms to infiltrate user computers.
Spyware: A software that monitors your activities on the computer. They collect all the user's personal information, personal habits, and surfing habits and send it to the author. Spyware is the biggest threat to the safety of a computer, a computer system.
Adware: Simply a form of adware stealthily installed on a user's computer or installed via a free software, approved by the user (but not aware of their purpose). However, they do not stop by simply advertising when combined with other viruses to increase the "effectiveness" of destruction.
Worm: Computer worm is one of the most widespread, widespread and popular software. Unlike "primitive" viruses, worms do not need "bait" files to infect. They self-replicate and spread through Internet, peer-to-peer networks, sharing services .
 Identify that the computer is infected with a virus
Identify that the computer is infected with a virus
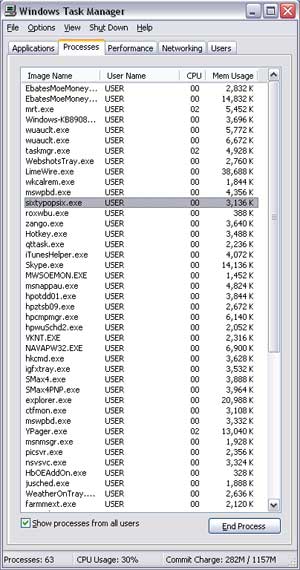
After entering the system, some virus machines immediately perform vandalism. Others lurked, silently spreading to other computers, waiting for G time to simultaneously "attack" to prevent users from being able to keep up; typically CIH virus, Melissa. Some common phenomena when a computer is infected with viruses: There are abnormal symptoms such as continuous access to hard disks; sluggish operation system; Some strange websites, advertising popup automatically jump out when you work. If you use Windows NT / 2000 / XP, you can refer to the information in Windows Task Manager as CPU Usage is always at 100%, there are some strange executable files in the Processes tab of Windows Task Manager .
Scan virus
When you suspect the system is infected, you need to find software to test and destroy them. Note: Virus protection before they enter the system is always simpler than destroying them. The article "New Anti-Virus" introduces 10 best antivirus products that can support both known and unknown threats. Each product has its strengths and weaknesses ranging from free to paid, so you can choose the right software yourself.
After selecting the appropriate software, you need to install them into the system. Some viruses are so "devilish" that after infecting the system, they prevent users from installing or controlling these software in order to not detect them, preventing access to the manufacturer's website. . If you cannot install in Normal mode in Windows, try setting it to Safe mode. To start the computer in Safe mode, do the following:
1. Use the System Configuration Utility or press F8 during Windows startup to enter Safe mode.
- Close all applications in use.
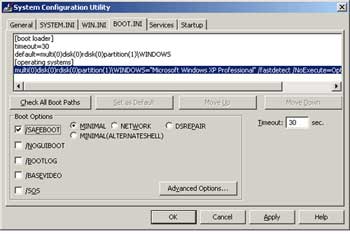
- Select Start. Run. Type msconfig command line and click OK to open the System Configuration Utility window
- On the BOOT.INI tab, check the / SAFEBOOT option in the Boot Options section
- Click Ok and select Restart to confirm restarting the computer to enter Safe mode.
 Note :
Note :
Restart the computer in Normal mode: Perform the above steps and remove the / SAFEBOOT option in the Boot Options section.
Update virus list. As mentioned above, if you cannot access the manufacturer's websites, it is not possible to update the virus definition online; Please download them from another computer to update.
Turn off System Restore. If you use Windows ME or XP, you should turn off the System Restore feature when your computer is infected with a virus. By default in Windows ME and XP, this feature is enabled to help you restore the system when something goes wrong. Anti-virus software cannot scan the System Volume Information folder, where System Restore stores files and folders that help restore the system. So there will be a "re-infection" of the virus when System Restore recovers the system of infected archives.
To turn off System Restore in Windows XP, do the following:
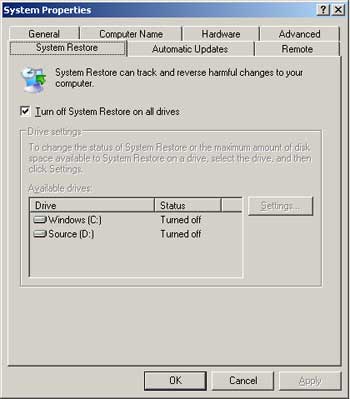
- Right-click on My Computer, select Properties
- In the System Properties window, System Restore tab, check Turn off System Restore on all drivers option and click OK
- Select Yes when asked to confirm this.
If using Windows ME, do the following:
- On the Desktop, right-click the My Computer icon and select Properties.
- In the System Properties window, select Performance. File System. Troubleshooting
- Check the option to Disable System Restore and click OK
- Select Close and Yes to restart Windows
 Note : turning off the System Restore feature means deleting all restore points. Manually create a restore point when System Restore is turned back on.
Note : turning off the System Restore feature means deleting all restore points. Manually create a restore point when System Restore is turned back on.
Full scan (full system scan). The default setting of some antivirus programs only scans some of the specified file types. To be sure, you should set up "full system scan" for the computer to be fully tested. Some notes during the scanning process:
- If you get an error message the software cannot delete a virus or a virus file. Please restart the computer in Safe mode and continue the test
- At the end of the scanning process, the program will report a summary of the detected viruses and how to handle them. If the program cannot kill certain viruses, try to kill them manually. Using the search engine with the keyword is the name of the virus, you will find information on how to destroy it at some websites of antivirus software manufacturers.
- After restarting Windows in Normal mode, if you get an error message similar to "Windows cannot find [FILE NAME]. Make sure you typed the correctly name, and then try again. To search for a file, click the Start button, and then click Search ". For example, with the W32.Lecna.A virus, you will see an error message that the iexplore.exe file cannot be found. These are the remnants of the W32.Lecna.A virus even though they have been destroyed. To delete them, you need to find and delete the keys added by this virus in the Registry. We still note that readers should back up the Registry before you "touch" them. Refer to how to back up the Registry in the article "Care and maintenance of the Windows Registry", ID: A0502_90.
Select Start. Run to open DOS Prompt window; type "regedit" to open the Registry Editor window. If you see an error message "Registry editing has been disabled by your administrator", refer to the information related to this error in the article "Internet Explorer always visiting strange websites," ID: A0604_154.
Find and delete spyware related keys in the following branches:
- KEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun. Delete the "iexplore.exe" = "iexplore.exe" key in the right pane.
- HKEY_LOCAL_MACHINESoftwareMicrosoftCurrentNetInf. Delete "hostid" = "[RANDOM NUMBER]" and "pid" = "[ENCRYPTED DATA]" keys
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa. Delete key "forceguest" = "0"
Exit Registry Editor and restart the computer.
Update fixes for OS, software. Some viruses like W32.Blaster.Worm often exploit vulnerabilities in the Remote Procedure Call service of Windows NT / 2000 / XP operating system to destroy. If you use Microsoft software, you can update the fix from http://www.microsoft.com/downloads/Search.aspx?displaylang=en, avoiding re-infection after scanning.
" Fire prevention is better than fire! " In the next article we will give you some experience and tips to protect your computer in the era of Internet boom and boom . virus.
Dong Quan
References
* http://service1.symantec.com/SUPPORT/nav.nsf/docid/1999041209131106
* http://www.symantec.com/avcenter/cybercrime/trojans_spyware.html?src=symsug_us#
See next part 2
You should read it
- Instructions to restore Windows 10 to the newly installed state
- How to Restore Your Windows XP Computer
- How to use System Restore in Windows: Turn off, turn on, create, restore System Restore
- How to Do a System Restore
- How to Remove the FBI Moneypak Virus in Windows 7
- How to Use System Restore on Windows 7
 Top 10 most dangerous viruses in June 2006
Top 10 most dangerous viruses in June 2006 Security has also become the target of viruses
Security has also become the target of viruses In June, 27 new viruses appeared in Vietnam
In June, 27 new viruses appeared in Vietnam Asia: 26 types of viruses are spreading strongly!
Asia: 26 types of viruses are spreading strongly! Security experts 'humiliated' because of new worms?
Security experts 'humiliated' because of new worms? 'Internal virus' YMHeart infected 4,600 Vietnamese computers via chat
'Internal virus' YMHeart infected 4,600 Vietnamese computers via chat