Some popular fake security software - Part 1
TipsMake.com - The fake security software term - Rogue security software, is a malicious program of malware, after infecting the victim's system, the application will display the wrong information. deviate from the current security situation , and entice users to spend money to buy the copyrights of these fake software. In the last few years, the number of users who have caught this trap is increasing, especially for desktop users. The following is an alphabetical list of some of today's popular fake programs:

1. A-Fast Antivirus
As a fake security program that is quite dangerous and easily spread, when successfully installed on the victim computer, the program will proceed to scan the entire registry key, continuously display false information about the virus. , Trojans and worms are detected on the system. And these messages only disappear when users buy the copyright.
Before removing A-Fast Antivirus using standard Windows tools, register the software's license with one of the following activation codes:
B0B302F772
C197C46C46
B20C1467B7
041E4B235A
25CCCC7329
9926220EED
A58EC19D33
C15F2FF276
F61E370D62
DDAD6A7A2C
9F8122FE00
3754DD9DA6
3DC52EA100
EE73BBFFA6
7E61C9C7DF
EE34D2E8A7
AA61971AA1
9D2510E3E8
When installing, A-Fast Antivirus will copy the following files to the hard drive:
% UserProfile% Local SettingsApplication Data [random characters]
% UserProfile% Local SettingsApplication Data [random characters] [random characters] tssd.exe
And initialize the following keys in the registry:
HKEY_CURRENT_USERSoftwareA-fast
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem "DosableTaskMgr" = "1"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun "fast"
HKEY_LOCAL_MACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewall
PolicyStandardProfileAuthorizedApplicationsList "C: Program FilesA-fastA-fast.exe"
The main screen of the program:
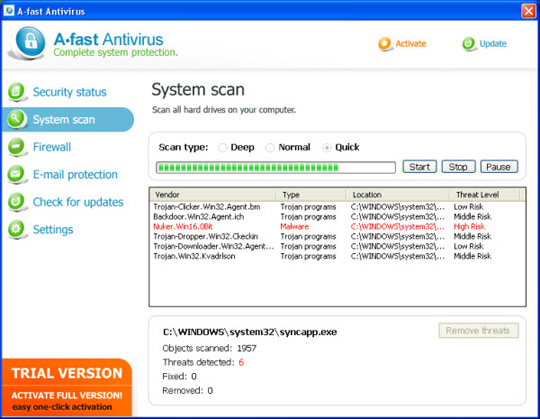
2. AKM Antivirus 2010 Pro
Similar to A-Fast Antivirus, AKM Antivirus 2010 Pro has extremely fast performance and infection modes. The program is also known as Your PC Protector.
When installing on a victim's computer system, AKM Antivirus 2010 Pro will copy the following files to the hard drive:
% UserProfile% DesktopAKM Antivirus 2010 Pro.lnk
% UserProfile% Start MenuProgramsAKM Antivirus 2010 Pro
% UserProfile% Start MenuProgramsAKM Antivirus 2010 ProAKM Antivirus 2010 Pro.lnk
C: Program Filesadc32.dll
C: Program Filesalggui.exe
C: Program Filesnuar.old
C: Program Filesskynet.dat
C: Program Filessvchost.exe
C: Program Fileswp3.dat
C: Program Fileswp4.dat
C: Program Fileswpp.exe
C: Program FilesAKM Antivirus 2010 Pro
C: Program FilesAKM Antivirus 2010 ProAKM Antivirus 2010 Pro.exe
% Temp% win1.tmp
% Temp% win2.tmp
And continue to create the following registry key:
HKEY_CURRENT_USERSoftwareAKM Antivirus 2010 Pro
Application main screen:
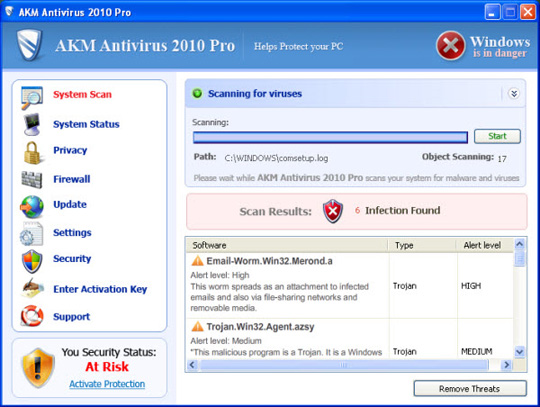
3. ApcSafe
APcSafe (also known as A Pc Safe) is also a form of Rogue Security Software, just like the two programs above. But there is a little difference here that ApcSafe supports users 'little' of system protection. In fact, APcSafe is a new variant of the Winisoft line, the main 'author' of APcSafe also produces the following variations:
APcSecure, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcsProtector, GreatDefender, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SiteVillain, LinkSafeness, SecureKeeper, AntiAID, System Warrior, System Veteran, System Fighter, Block Protector, Block Keeper, Block Scanner, Block Watcher, SoftBarrier, Shield Safeness, Soft Stronghold, Soft Veteran, SoftCop, Soft Soldier, Trust Fighter, Soldier Trust, Safe Fighter, Trust Cop, Secure Warrior, Secure Fighter, Secure Veteran, Security Soldier, Security Fighter, Save Armor, Save Defender, Trust Warrior, Soft Safeness, Safety Keeper, Save Keeper, Quick Heal Cleaner, System Cop, Block Defense, Save Defense, Trust Ninja, Save Soldier , Save Keep, Winishield, Wini Fighter, WiniBlueSoft.
After successfully installing the victim's computer, APcSafe will generate a certain number of empty files with different sizes and names. And when reviewing, APcSafe will automatically detect those files that are malicious, harmful to the system and require users to buy the full license of the program.
Exactly, APcSafe will copy the following files to the hard drive:
% ProgramFiles% APcSafe SoftwareApcSafeApcSafe.exe
% ProgramFiles% APcSafe SoftwareApcSafemain_config.xml
% ProgramFiles% APcSafe SoftwareApcSafeuninstall.exe
% AllUsersProfile% DesktopApcSafe.lnk
% AllUsersProfile% Start MenuProgramsApcSafe1 ApcSafe.lnk
% AllUsersProfile% Start MenuProgramsApcSafe2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsApcSafe3 Uninstall.lnk
and the following registry keys:
HKEY_LOCAL_MACHINEsoftwareApcSafe
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallApcSafe
HKEY_CURRENT_USERsoftwareApcSafe
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'ApcSafe'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'ApcSafe'
Main interface of ApcSafe:
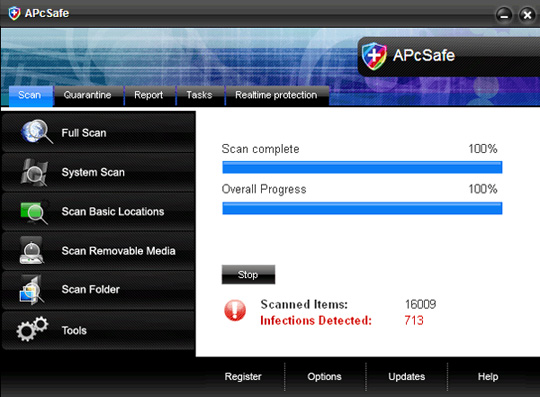
4. ApcSecure
With the same functionality and structure as ApcSafe, this program is spread through the website www.apcsecure.com (this address is no longer available). ApcSecure is a new variant of Winiguard / Winisoft series, besides, there are other types such as:
ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, Protected, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
Like ApcSafe, when successfully installed on the victim computer, APcSecure will automatically generate a certain number of empty files with different names. When conducting a review, APcSecure will automatically detect the correct files and ask the user to purchase the license to erase the above files.
APcSecure will copy the following files to the system drive:
% ProgramFiles% APcSecure SoftwareAPcSecureAPcSecure.exe
% ProgramFiles% APcSecure SoftwareAPcSecuremain_config.xml
% ProgramFiles% APcSecure SoftwareAPcSecureuninstall.exe
% AllUsersProfile% DesktopAPcSecure.lnk
% AllUsersProfile% Start MenuProgramsAPcSecure1 APcSecure.lnk
% AllUsersProfile% Start MenuProgramsAPcSecure2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsAPcSecure3 Uninstall.lnk
And the following registry keys:
HKEY_LOCAL_MACHINEsoftwareAPcSecure
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallAPcSecure
HKEY_CURRENT_USERsoftwareAPcSecure HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'APcSecure'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'APcSecure'
Some pictures of the program:

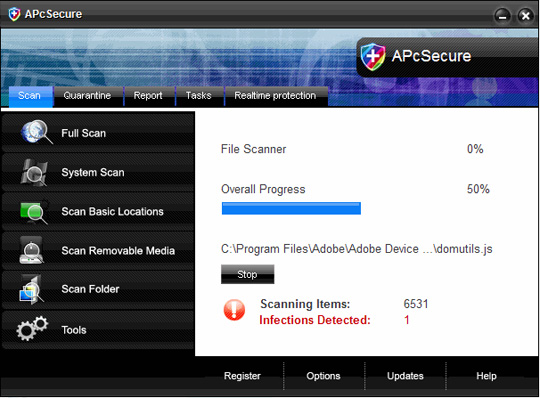
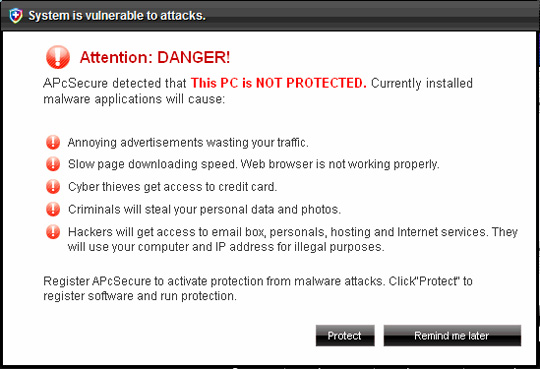
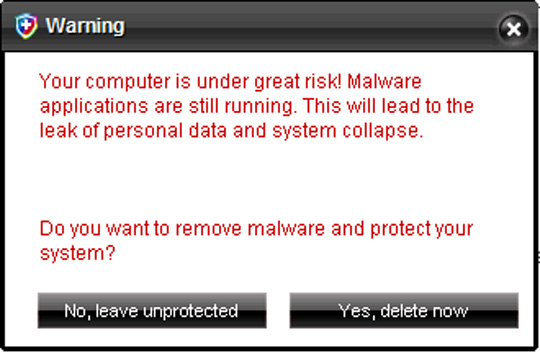
5. AntiSpyware Soft
When successfully infiltrated and installed on the victim computer, AntiSpyware Soft will continuously issue warning messages about viruses, Trojans and worms detected on the system, users will not be able to delete or disable the information. This information unless buying the license or activation key of the program.
During the installation process, AntiSpyware Soft will copy the following file to the hard drive:
% Documents and Settings% [UserName] Local SettingsApplication Data [random characters] [random characters] tssd.exe
Also create the following registry keys:
HKEY_CURRENT_USERSoftwareAvScan
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun '[random characters]'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun '[random characters]'
HKEY_CURRENT_USERSoftwareavsoft
HKEY_CURRENT_USERSoftwareavsuite
HKEY_LOCAL_MACHINESOFTWAREavsoft
HKEY_LOCAL_MACHINESOFTWAREavsuite
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerDownload "RunInvalidSignatures" = "1"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings "ProxyOverride" = ""
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings "ProxyServer" = "http = 127.0.0.1: 5555"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAssociations "LowRiskFileTypes" = ".exe"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAttachments "SaveZoneInformation" = "1"
Main interface of the program:
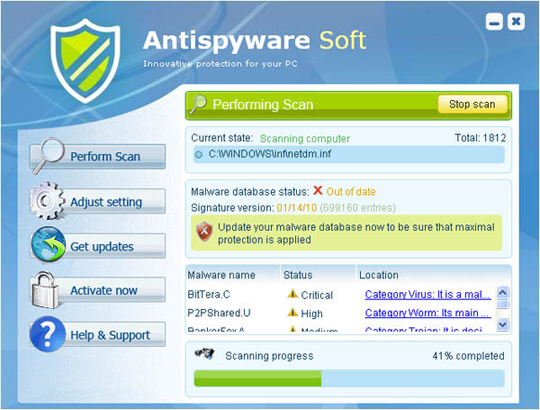
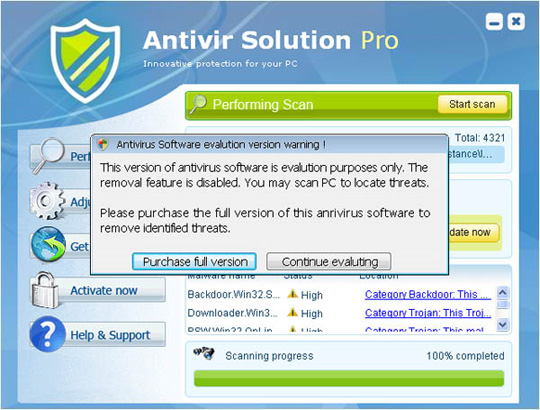
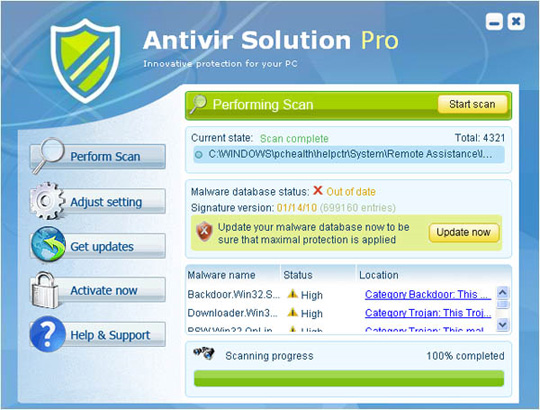
6. Antivir Solution Pro
Like all of these malicious programs, Antivir Solution Pro cleverly disguises it as legitimate security software, making it easy for users to trust and always use it. The program is widely available through http://antispybox.com/ and related links. This is also a self-replicating form of AVSecurity Suite, Antivirus Suite and Antivirus Soft. When the review process begins, users will continually receive warnings about viruses, Trojans and worms that are "raging" on the system, and rooted processing is only carried out when a user purchases a key. program activities.
When installing into the system, Antivir Solution Pro will copy the following executable file to the hard drive:
% UserProfile% Local SettingsApplication Data% random %% random% .exe
And create the following registry keys:
HKEY_LOCAL_MACHINEsoftwareAVSolution
HKEY_LOCAL_MACHINEsoftwareAVSuitE
HKEY_CURRENT_USERsoftwareAVSolution
HKEY_CURRENT_USERsoftwareAVSuitE
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, "% random%"
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, "% random%"
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionInternet Settings
ProxyServer = http = 127.0.0.1: 5643
ProxyOverride =
HKEY_CURRENT_USERsoftwareMicrosoftInternet ExplorerPhishingFilter
EnabledV8 = 0 × 00000000 (0)
Enabled = 0 × 00000000 (0)
Some pictures of the program:
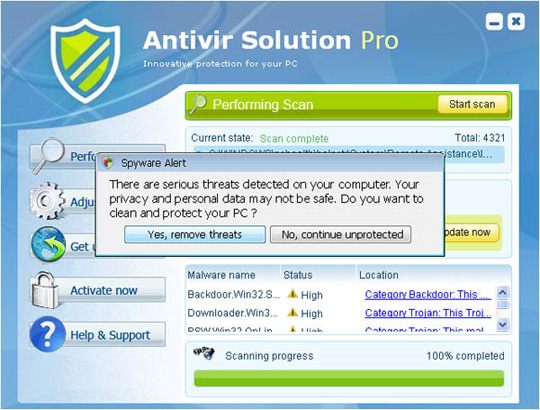
7. Antivirus
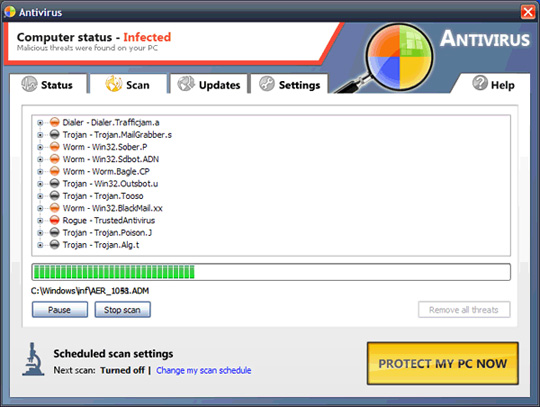
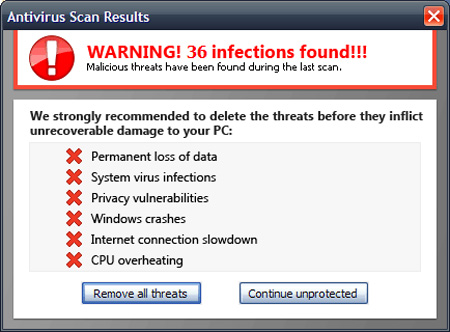
A very generic name - Antivirus, this program has something very similar to APcSafe and ApcSecure, the main source of infection of this malicious application is the website www.just-protect-pc.info (address This is no longer available. The way to infect and operate is not changed, the warnings about viruses, Trojans and worms discovered on the system are continuously sent to users.
During the installation process, Antivirus will copy this file to the system drive:
% ProgramFiles% AntivirusAvBho.dll
% ProgramFiles% AntivirusUninstall.exe
% ProgramFiles% Antiviruswscsvc32.exe
% ProgramFiles% AntivirusAntivirus.exe
% AllUsersProfile% DesktopAntivirus.lnk
% AllUsersProfile% Start MenuProgramsAntivirusAntivirus.lnk
% AllUsersProfile% Start MenuProgramsAntivirusUninstall.lnk
% UserProfile% Application DataMicrosoftInternet ExplorerQuick LaunchAntivirus.lnk
% UserProfile% Local SettingsTempwinupd64x.exe
And create the following registry keys:
HKEY_LOCAL_MACHINEsoftwareAntivirus
HKEY_LOCAL_MACHINEsoftwareClassesAvBho.AvBhoApp
HKEY_LOCAL_MACHINEsoftwareClassesAvBho.AvBhoAppCLSID
HKEY_LOCAL_MACHINEsoftwareClassesAvBho.AvBhoAppCurVer
HKEY_LOCAL_MACHINEsoftwareClassesAvBho.AvBhoApp.1
HKEY_LOCAL_MACHINEsoftwareClassesAvBho.AvBhoApp.1CLSID
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620}
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620} InprocServer32
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620} ProgID
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620} Programmable
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620} TypeLib
HKEY_LOCAL_MACHINEsoftwareClassesclsid {9d541c6a-573b-4888-b35e-6816e68c3620} VersionIndependentProgID
HKEY_LOCAL_MACHINEsoftwareClassesInterface {967A494A-6AEC-4555-9CAF-FA6EB00ACF91}
HKEY_LOCAL_MACHINEsoftwareClassesInterface {967A494A-6AEC-4555-9CAF-FA6EB00ACF91} ProxyStubClsid
HKEY_LOCAL_MACHINEsoftwareClassesInterface {967A494A-6AEC-4555-9CAF-FA6EB00ACF91} ProxyStubClsid32
HKEY_LOCAL_MACHINEsoftwareClassesInterface {967A494A-6AEC-4555-9CAF-FA6EB00ACF91} TypeLib
HKEY_LOCAL_MACHINEsoftwareClassesInterface {9692BE2F-EB8F-49D9-A11C-C24C1EF734D5}
HKEY_LOCAL_MACHINEsoftwareClassesInterface {9692BE2F-EB8F-49D9-A11C-C24C1EF734D5} ProxyStubClsid
HKEY_LOCAL_MACHINEsoftwareClassesInterface {9692BE2F-EB8F-49D9-A11C-C24C1EF734D5} ProxyStubClsid32
HKEY_LOCAL_MACHINEsoftwareClassesInterface {9692BE2F-EB8F-49D9-A11C-C24C1EF734D5} TypeLib
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26}
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26} 1.0
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26} 1.0
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26} 1.0win32
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26} 1.0FLAGS
HKEY_LOCAL_MACHINEsoftwareClassesTypelib {65DA0CE6-30D1-4144-A0B6-59BD01372E26} 1.0HELPDIR
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects {9d541c6a-573b-4888-b35e-6816e68c3620}
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallAntivirus
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'Antivirus.exe'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'wscsvc32.exe'
Some pictures of the program:
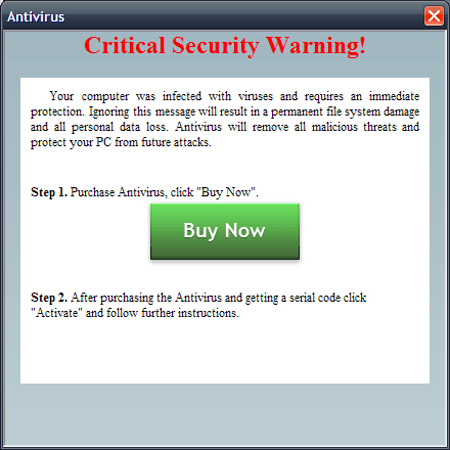
8. Antivirus 7
Unlike a fake program Antivirus, Antivirus 7 will automatically create its executable file during system startup, each time so, users will see the interface of Antivirus 7 appear quickly and then turn off. When scanning, Antivirus 7 always detects viruses and other malicious types in the system directory ( C: Windows and C : WindowsSystem32 ). When the user agrees to buy the license to delete the malicious files detected above, Antivirus 7 will continue to spread to other folders on the system (and other computers on the local network), while The accompanying Trojan constantly downloads other variants of Antivirus 7 from the Internet.
Antivirus 7 will automatically copy the following files to the hard drive:
% Documents and Settings% All UsersStart MenuAV7
% Documents and Settings% All UsersStart MenuAV7Antivirus7.lnk
% Documents and Settings% All UsersStart MenuAV7Uninstall.lnk
% Program Files% AV7
% Program Files% AV7antivirus7.exe
% WINDOWS% SoftwareDistributionDataStoreLogstmp.edb
% WINDOWS% system32UpdateExplorer.dll
% UserProfile% DesktopAntivirus7.lnk
and create the following registry keys:
HKEY_CURRENT_USERSoftwareEVA246
HKEY_CLASSES_ROOTCLSID {E2BFE352-A303-4EA8-88FE-CE35361D7E8B}
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects {E2BFE352-A303-4EA8-88FE-CE35361D7E8B}
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun "AV7"
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionInternet Settings5.0User AgentPost Platform "WinNT-EVI 12.03.2010"
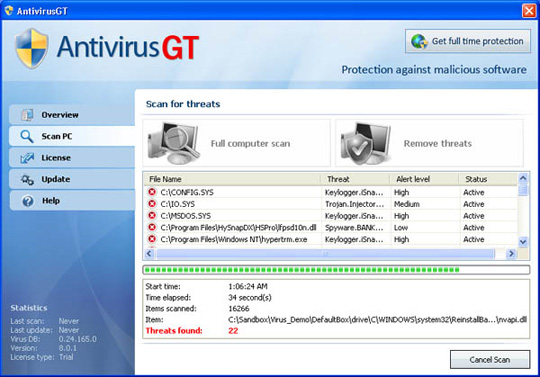
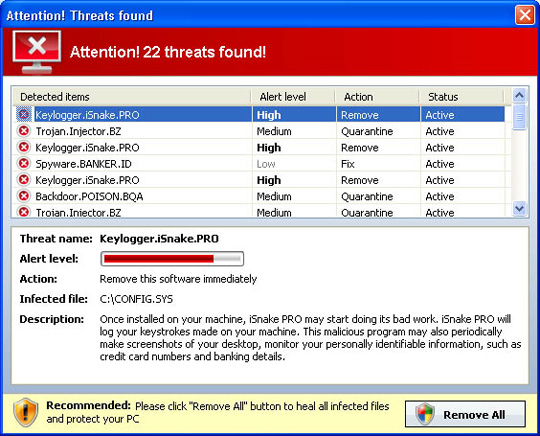
9. AntivirusGT
If compared with the above applications, AntivirusGT can be considered as a complete copy of Antivirus7. When the review process begins, AntivirusGT will create and detect false messages about the status and number of viruses, Trojans and worms.
After successfully installing the victim's computer, AntivirusGT will automatically copy the following files to the hard drive:
% ProgramFiles% AVGTAntivirusGT.exe
% AllUsersProfile% Start MenuAVGTAntivirusGT.lnk
% AllUsersProfile% Start MenuAVGTUninstall.lnk
% UserProfile% DesktopAntivirusGT.lnk
and create the following registry keys:
HKEY_CURRENT_USERsoftwareEVA50C
HKEY_CURRENT_USERsoftwareWinV2
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, "AVGT"
Some pictures of the program:
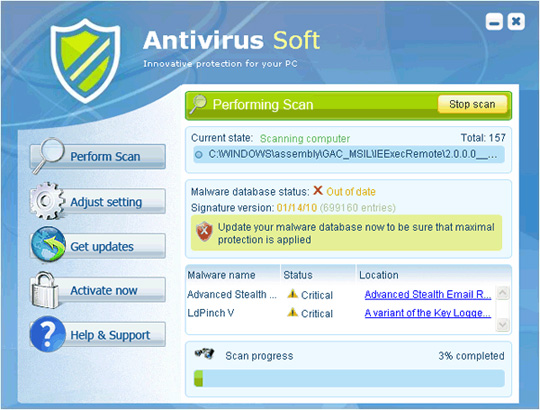
10. Antivirus Soft
Antivirus Soft is also listed as Rogue Security Software - fake security software, when cleverly disguised as one of the safest applications for inexperienced users, such as virus scanning or registry review. The origin of spreading this malicious application is the website www.newsoftspot.com (this address no longer exists). Just like all of the fake software listed above, Antivirus Soft when running will constantly display false messages about viruses, Trojans and worms. If the user does not purchase the activation key, it will not turn off those annoying notifications.
When installing into the system, Antivirus Soft will copy the following files to the hard drive:
% UserProfile% Local SettingsApplication Data% random %% random% sftav.exe
and the following registry keys:
HKEY_CURRENT_USERsoftwareavsoft
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun,% random%
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun,% random%
Some images of Antivirus Soft:
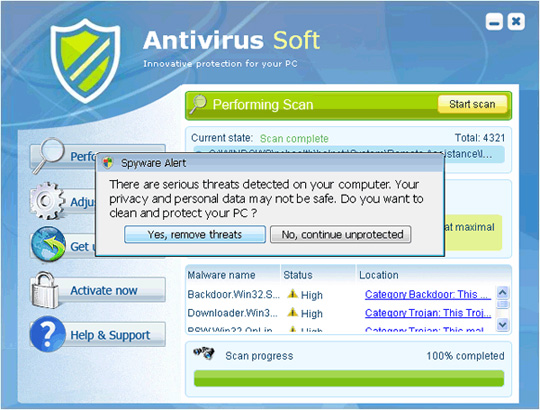
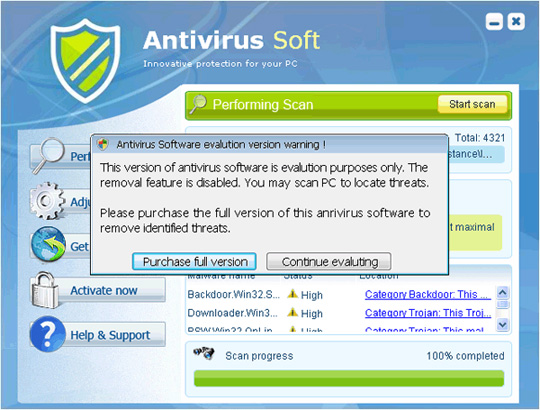
11. Antivirus Suite
Antivirus Suite - has been and is still one of the fastest, most powerful spreads today. For users who are not wary or have little experience. When the Antivirus Suite works, the program will only display false messages about viruses, Trojans and worms detected on the system. Only when the user purchases the license or the activation key will these messages disappear.
Antivirus Suite will copy the following files to the system drive after installation:
% UserProfile% Local SettingsApplication Data [random characters]
% UserProfile% Local SettingsApplication Data [random characters] [random characters] tssd.exe
Also create the following registry keys:
HKEY_CURRENT_USERSoftwareavsuite
HKEY_LOCAL_MACHINESOFTWAREavsuite
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerDownload "RunInvalidSignatures" = "1"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings "ProxyOverride" = "
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings "ProxyServer" = "http = 127.0.0.1: 5555"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAssociations "LowRiskFileTypes" = ".exe"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAttachments "SaveZoneInformation" = "1"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun ""
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun ""
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerDownload "CheckExeSignatures" = "no"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionInternet Settings "ProxyEnable" = "1"
Main interface of the program:
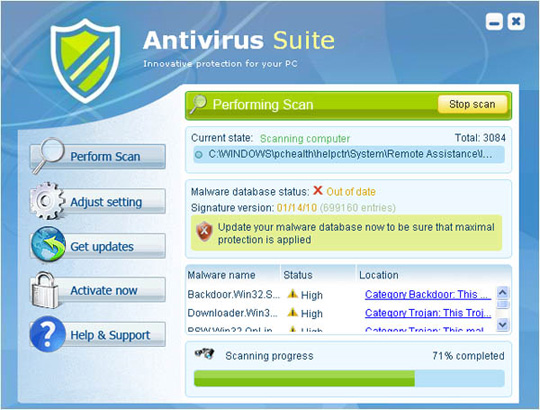
12. ByteDefender
In fact, this is a malicious malware program, when installed, it will continue to "call the Trojan" to the victim's computer in the form of audio or video codec packs - of course it is also fake. Once successfully installed, ByteDefender will continuously perform scans on the system, and display completely misleading information about the security status of the computer. The main purpose of this process is to 'entice' users to click on advertising links or purchase full licenses to use the full functionality of ByteDefender.
Byte Defender is essentially a new variant of Winiguard / Winisoft, disguised on a computer system as a safe and secure application, similar to a virus scanning or system registry application (or collectively called Rogue Security Software). At the same time, it also creates the following fake software variants:
PcsSecure, APcSafe, APcSecure, ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
After Byte Defender is installed on the system, this application will automatically generate redundant files with many different names. When users enable full system scanning, Byte Defender will continually create earlier virus, Trojan and worm warning messages before officially creating these malicious files. At the same time, these messages will never disappear unless the user buys the license of the program.
During the installation process, Byte Defender will copy the following files to the hard drive:
% ProgramFiles% ByteDefender SoftwareByteDefenderByteDefender.exe
% ProgramFiles% ByteDefender SoftwareByteDefenderUninstall.exe
% ProgramFiles% ByteDefender SoftwareByteDefenderalways_delete.xml
% ProgramFiles% ByteDefender SoftwareByteDefenderalways_skip.xml
% ProgramFiles% ByteDefender SoftwareByteDefenderquarantinequarantine.xml
% AllUsersProfile% Start MenuProgramsByteDefender.lnk
% UserProfile% DesktopByteDefender.lnk
And continue to create the following keys in the registry system:
HKEY_LOCAL_MACHINEsoftwareByteDefender
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallByteDefender
HKEY_CURRENT_USERsoftwareByteDefender
HKEY_CURRENT_USERsoftwareByteDefenderagents
HKEY_CURRENT_USERsoftwareByteDefendergeneral
HKEY_CURRENT_USERsoftwareByteDefenderrealtime
HKEY_CURRENT_USERsoftwareByteDefenderscanner
HKEY_CURRENT_USERsoftwareByteDefendertasks
HKEY_CURRENT_USERsoftwareByteDefendertasks
HKEY_CURRENT_USERsoftwareByteDefendertasks1
HKEY_CURRENT_USERsoftwareByteDefenderupdates
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, "ByteDefender"
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, "ByteDefender".
You should read it
- ★ Instructions to remove fake security program Cyber Security
- ★ What is Social Engineering? How to prevent Social Engineering?
- ★ Awareness and experience - the most important factor in every network security process
- ★ Find out about Ghidra - NSA's powerful cybersecurity tool
- ★ Learn about the Cross-Site Request Forgery attack method