What is Social Engineering? How to prevent Social Engineering?
Social engineering is a type of attack based on human interaction and often involves manipulating things by breaking common security processes, accessing systems and networks to gain financial benefits. main.
Criminals use social engineering techniques to hide their true identity and motivation by the appearance of a trusted source of information or individuals. The goal is to influence, manipulate or trick users into giving up privilege or access information within an organization. For example, an attacker may pretend to be an urgent problem colleague, requiring access to additional network resources.

Social engineering is a common tactic of hackers because it is easier to exploit a user's weakness than to find a network or software vulnerability. Hackers often use social engineering tactics as the first step in a larger campaign to infiltrate systems or networks and steal sensitive data or disperse malware.
- Risks from malware and how to prevent it
What is social engineering?
Social engineering is the art of controlling people to reveal confidential information. The types of information that criminals are looking for may vary, but often when an individual is targeted, criminals often try to trick the person into providing passwords, banking information or access to the device. charged to install malware.

As mentioned above, criminals use social engineering tactics because it is easier to attack users' weaknesses than to hack software. For example, it would be much easier to trick someone into giving you a password than try to hack their password (unless the password is really weak).
It is important to know when to and should not give important information to someone. The same is true when you interact online and use the site: Do you need to know if the site is legal or safe to provide your personal information?

If you ask any security expert, they will tell you the weakest link in the security chain is the person - the object can easily accept a familiar person or script. It's like when you protect your house. It doesn't matter how many locks and how many locks you have. It doesn't matter if you have a dog to look after or have an alarm system and the barbed wire fence is even protective. As long as you trust the person at the gate, when he says that he is a pizza deliverer and you let him into the house without checking, you become completely passive by any risks he brings.
Criminals take advantage of social engineering through human behavior. For example, if a stranger wants to enter a building, he just needs to step in and confidently ask someone to help him inside.
Popular hackers Kevin Mitnick helped popularize the term 'Social engineer' in the 1990s, although more and more sophisticated new ideas and techniques were introduced.
How does social engineering work?
Social engineering uses many different tactics to perform attacks.
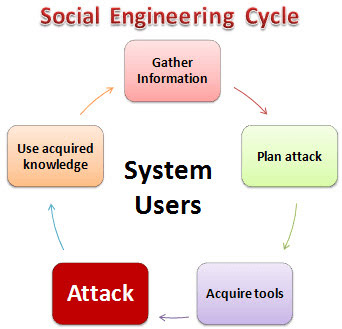
The first step in most social engineering attacks is that the attacker will conduct research and survey on the target. For example, if the goal is a business, hackers can gather intelligence about employee structure, internal operations, general terms used in the industry and business partners, etc. A popular tactic of social engineering is to focus on the behaviors and patterns of low-level employees, but with first-hand access, such as security guards or receptionists. Hackers can scan their social network profile for information and research their behavior.
From there, hackers can design an attack based on the information collected and exploit the weaknesses discovered during the survey period.
If the attack is successful, hackers have access to sensitive data - such as credit cards or bank information, to make money from goals or have access to networks or systems. protect.
Types of social engineering attacks
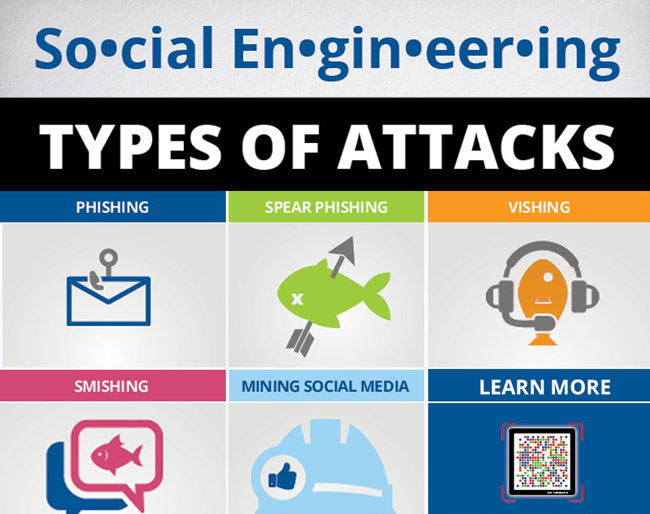
Common types of social engineering attacks include:
- Baiting : Baiting is when an attacker leaves behind a physical device infected with malware, such as a USB flash drive, in a place that will definitely be found. After that, the finder will use the device, then install the device on his computer and accidentally cause the device to be infected with malware as well.
- Phishing : Phishing is when an attacker sends a phishing email disguised as a legitimate email (often fake from a reliable source). This notice is intended to trick recipients into sharing personal or financial information or clicking on the malware installation link.
- Spear phishing : Spear phishing is like Phishing but designed specifically for a specific person or organization.
- Vishing : Vishing is also known as voice fraud and it is the use of social engineering over the phone to collect personal information and financial information from the target. (See also: Phishing "tricks" by phone)
- Pretexting : Pretexting is an attacker who wants access to privileged data. For example, a pretexting scam might involve an attacker pretending to need personal data or financial information to confirm the identity of the recipient.

- Scareware : Scareware involves tricking victims into thinking that his computer is infected with malware or accidentally downloading illegal content. The attacker then provides the victim with a solution to fix the bogus problem. In fact, the victim is simply tricked into downloading and installing the attacker's malware.
- Water-holing : A water-holing attack is when an attacker attempts to compromise with a specific group of people by infecting malware into sites they often visit or trust.
- Diversion theft : In this type of attack, social engineering will trick a delivery or courier company to receive or deliver the wrong location, thus preventing transactions from being made.
- Quid pro quo : Quid pro quo is an attack in which social engineering pretends to provide something in exchange for the target's information or support. For example, a hacker randomly selects phone numbers in an organization and pretends to call back for technical support. Finally, the hacker will find a person who is having technology related problems and pretending to help. Through this, hackers can force targets to add commands to launch malware or may collect password information.

- Honey trap : This is an attack in which social engineering pretends to be an 'attractive' person to interact with an online person or forge an online relationship and gather sensitive information through termites. that relationship.
- Tailgating : Tailgating, sometimes called piggybacking, is when a hacker enters a protected building by tracking someone who has access to the building. This attack assumes that the person who has the right to enter the building will keep the door open for the person behind them (assuming they are allowed to do this there).
- Rogue : The rogue software is a type of malware, tricking payment targets to eliminate fake malware. (See also: 5 signs of computer malware infection)
Examples of social engineering attacks
Perhaps the most famous social engineering attack comes from the legendary Trojan War, in which Greeks can enter the city of Troy and win by hiding in a giant wooden horse donated to the army. Trojan as a peace gift.
Frank Abagnale is considered one of the leading experts in social engineering techniques. In the 1960s, he used various tactics to impersonate at least eight people, including an airline pilot, a doctor and a lawyer. After being detained, he became a security consultant for the FBI and began his own financial fraud advisory career. His own experiences helped him become famous for the best-selling book Catch Me If You Can and then this book was adapted into a film by an Oscar-winning director, Steven Spielberg.
A recent example of a successful social engineering attack is a breach of 2011 data from RSA security company. An attacker sent two different phishing emails within two days to the small group of employees of RSA. The email has the subject line "Recruitment Plan 2011" and contains the attached Excel document file. The spreadsheet containing malicious code has been silently installed through the Adobe Flash vulnerability. Although it is unclear what information was stolen, RSA's two-factor authentication system SecurID (2FA) was compromised and the company spent about $ 66 million to remedy the aftermath. public.
In 2013, Syrian Electronic Army was able to access Associated Press's Twitter account by including a malicious link in a phishing email. Email is sent to AP staff under the guise of a colleague. The hackers then tweeted a fake news story from the AP account saying two explosions happened at the White House and then President Barack Obama was injured. This has attracted so many people interested, that the stock market has lost 150 points in less than 5 minutes.
Also in 2013, a phishing scam led to a serious violation of Target's data. A phishing email was sent to an HVAC subcontractor (involving heating, ventilation and air conditioning) - a Target's business partner. Emails containing Citadel Trojans, allow attackers to break into Target's point of sale system and steal information from 40 million customers' credit and debit cards. That same year, the US Department of Labor became targeted by a watering hole attack, and the ministry's websites were infected with malware through a flaw in Internet Explorer - a remote access Trojan. called Poison Ivy.

In 2015, hackers gained access to John Brennan's personal AOL email account, then the CIA director. One of the hackers who explained in the media how he uses social engineering is to forge a Verizon technician and ask for information about Brennan's account from the telecom tycoon. Once the hackers collect Brennan's Verizon account details, they will contact AOL and use the information to accurately answer the security questions for Brennan's email account.
Measures to prevent social engineering attacks
Security experts recommend that IT departments routinely conduct checks to avoid intrusions using social engineering techniques. This will help administrators find out which types of users are most at risk for specific types of attacks, and identify additional training requirements for their employees.
Training in security awareness can also be helpful in preventing social engineering attacks. If people know what forms of social engineering attacks and what they are capable of doing, they will be less likely to become victims.
On a smaller scale, organizations must have secure web and email access ports to scan emails containing malicious links and filter them out, to reduce the likelihood that employees will click on one of the links. not safe there. It is also important to keep up to date with software fixes on devices, as well as monitor employees who handle sensitive information and enable advanced authentication measures for them.
Do not become a victim
In the context of widespread phishing attacks, very quickly and just a few users prey as the attack was successful, you need methods to protect yourself. The simplest thing is to pay attention to everything. Keep in mind the following to avoid fraud.
Tips to remember:
- Slow down : Spammers want you to take action first and think later. If the transmission message creates a sense of urgency or uses high pressure tactics, be wary. Never let the emergency they create affect your judgment.
- Careful research : Suspect any messages you receive. If the email seems to be from a company you are using, find out your own way. Use the search engine to access the company's website or phone directory to find their phone number and then verify the information.
- Don't let a link control where you are : Keep control by searching the site yourself by using a search engine to make sure you get to the right website. Hovering over the links in the email will show the actual URL below, but note that sophisticated spoofing can still fool you.
- Email hacking is rampant : Hackers, spammers and social engineering users taking control of everyone's email accounts (and other contact accounts) have become more and more dangerous. When they control their email accounts, they will steal their contacts. Even if the sender seems to be the person you know, if you don't expect an email with a link or attachment, check with your friends before opening the link or downloading.
- Be careful with any download : If you don't know who the sender is and why they send the attachment to you, downloading anything is a serious mistake.
- Foreign email address is fake : If you suddenly receive an email from a lottery company or sweepstakes abroad, money from an unidentified relative or request for money transfer from abroad is certain It is a scam.
How to protect yourself:

- Delete all requests for financial information or passwords : If you are asked to reply to a message with personal information, it is a scam.
- Refuse to ask for help or offer help : Legal companies and organizations do not contact you to help. If you do not request specific support from the sender, consider any suggestions to 'assist' credit score recovery, assistance with buying a home, answering questions, etc. Similarly, if you receive a request for assistance from a charity or organization with which you have no relationship, remove those requests. Instead, search for reputable charities yourself to avoid becoming a victim of a scam.
- Set your spam filter to the highest level : Each email program has a spam filter. Look at your installation options and set these options to the highest level - just be sure to check your spam folder periodically to see if any important emails were mistakenly sent here. You can also look for step-by-step instructions for installing your spam filter by searching your email provider name plus the phrase 'spam filters'. (See also: How do you prevent spam messages?)
- Secure your computer devices : Install antivirus software, firewalls, email filters and update these software. Set your operating system to update automatically and if your smartphone does not update automatically, update it manually whenever you receive a notification asking for updates. Use an anti-phishing tool provided by your web browser or a third party to warn you about risks. (See also: 7 ways to protect web browsers from network attacks)
See more:
- 10 scam tricks via email
- 10 common scams on Facebook
- Check the safety of websites
You should read it
- ★ 9 misunderstand about social networks
- ★ The importance of correlating cybersecurity events
- ★ Find out about Ghidra - NSA's powerful cybersecurity tool
- ★ Think before posting anything on social networks, hackers can exploit them to launch attacks
- ★ Social networks do not create a diversity of views

