Some popular fake security software - Part 2
TipsMake.com - The fake security software term - Rogue security software, is a malicious program of malware, after infecting the victim's system, the application will display the wrong information. deviate from the current security situation , and entice users to spend money to buy the copyrights of these fake software. In the last few years, the number of users who have caught this trap is increasing, especially for desktop users. The following is an alphabetical list of some of today's popular fake programs:
>> Some popular fake security software - Part 1
13. CleanUP Antivirus
In addition to the harms like the malicious programs described above, CleanUP Antivirus actually provides users with a minimal amount of protection. When the installation is successful, CleanUP Antivirus will create the boot path with the system. And every time the computer starts up, CleanUP Antivirus automatically scans the entire computer, and continuously copies the junk files all over the hard drive. On the other hand, when the review process is activated, CleanUP Antivirus detects itself as viruses, Trojans or worms, and requires users to purchase the activation license of the program.
After successfully installing the victim's computer, CleanUP Antivirus will copy the following files to the hard drive:
% AllUsersProfile% Application Data58969CUf4c.exe
% AllUsersProfile% Application Data58969CUA.ico
% AllUsersProfile% Application DataCUQKWACUZNJUENEA.cfg
% UserProfile% Application DataCleanUp AntivirusInstructions.ini
% UserProfile% Application DataCleanUp Antiviruscookies.sqlite
% UserProfile% Application DataMicrosoftInternet ExplorerQuick LaunchCleanUp Antivirus.lnk
% UserProfile% DesktopCleanUp Antivirus.lnk
% UserProfile% Start MenuCleanUp Antivirus.lnk
% UserProfile% Start MenuProgramsCleanUp Antivirus.lnk
Also create the following deviation records into the Hosts system file:
74.125.45.100 4-open-davinci.com
74.125.45.100 securitysoftwarepayments.com
74,125.45,100 privatesecuredpayments.com
74.125.45.100 secure.privatesecuredpayments.com
74,125.45.100 getantivirusplusnow.com
74.125.45.100 secure-plus-payments.com
74.125.45.100 www.getantivirusplusnow.com
74.125.45.100 www.secure-plus-payments.com
74.125.45.100 www.getavplusnow.com
74.125.45.100 safebrowsing-cache.google.com
74,125.45,100 urs.microsoft.com
74.125.45.100 www.securesoftwarebill.com
74.125.45.100 secure.paysecuresystem.com
74,125.45,100 paysoftbillsolution.com
74,125,45,100 protected.maxisoftwaremart.com
Besides, you can create and record many of the following registry keys:
Table of registry keys
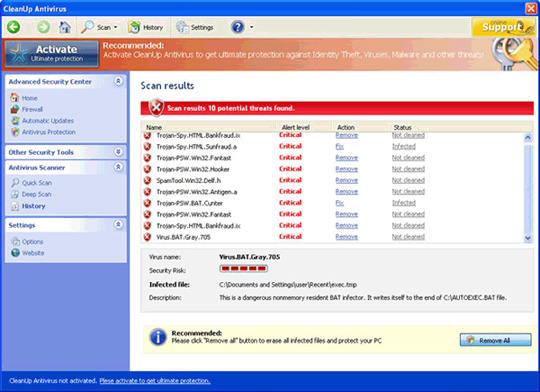
Main interface of CleanUp Antivirus:
14. Control Components
Control Components are also listed as fake security software, with the mode of operation and spread no different from the above models.
After installing on the victim computer, Control Components will copy all the following files to the system partition:
% UserProfile% Application DataControl Componentssettings.ini
% UserProfile% Application DataControl Componentsuninstall.exe
% UserProfile% Application DataControl Componentsccagent.exe
% UserProfile% Application DataControl Componentsccmain.exe
% UserProfile% Application DataControl Componentsfaqguide.html
% UserProfile% Application DataControl Componentsfaqimages6.png
% UserProfile% Application DataControl Componentsfaqimages7.png
% UserProfile% Application DataControl Componentsfaqimages8.png
% UserProfile% Application DataControl Componentsfaqimages9.png
% UserProfile% Application DataControl Componentsfaqimages10.png
% UserProfile% Application DataControl Componentsfaqimages5.png
% UserProfile% DesktopControl Components.lnk
Also create the following registry keys:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstallControl Components
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun "ccagent.exe"
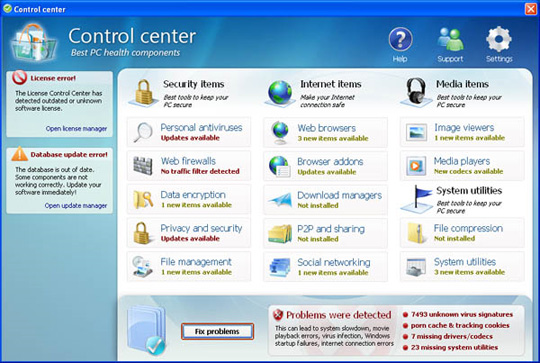
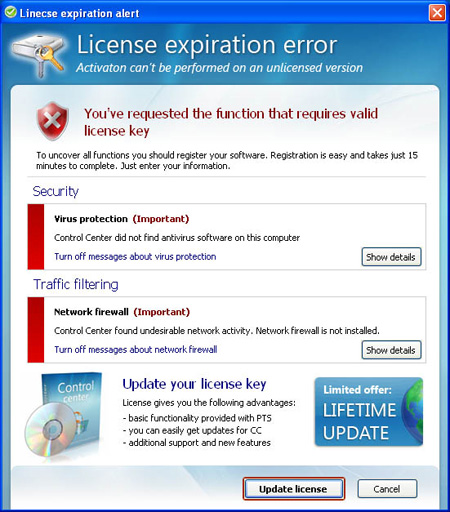
Some pictures of the program:
15. Digital Protection
Like the malware listed above, Digital Protection is a new variant of the CoreGuard series, and there are also variations of the same type: Your Protection, User Protection, and Dr. Guard, Paladin Antivirus.
When installing on a victim's computer system, Digital Protection will continuously copy the following junk files:
% Documents and Settings% [UserName] DesktopDigital Protection Support.lnk
% Documents and Settings% [UserName] DesktopDigital Protection.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital Protection
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionAbout.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionActivate.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionBuy.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionDigital Protection Support.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionDigital Protection.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionScan.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionSettings.lnk
% Documents and Settings% [UserName] Start MenuProgramsDigital ProtectionUpdate.lnk
% Documents and Settings% [UserName] Application DataMicrosoftInternet ExplorerQuick LaunchDigital Protection.lnk
% Program Files% Digital Protection
% Program Files% Digital Protectionabout.ico
% Program Files% Digital Protectionactivate.ico
% Program Files% Digital Protectionbuy.ico
% Program Files% Digital Protectiondigprot.exe
% Program Files% Digital Protectionhelp.ico
% Program Files% Digital Protectionscan.ico
% Program Files% Digital Protectionsettings.ico
% Program Files% Digital Protectionsplash.mp3
% Program Files% Digital Protectionuninstall.exe
% Program Files% Digital Protectionupdate.ico
% Program Files% Digital Protectionvirus.mp3
% WINDOWS% System32zq5e7t.dll
% WINDOWS% System32vurrozj.dll
% WINDOWS% Tempavp.exe
% WINDOWS% Temp [random name] .exe
And continue to create the following registry keys:
HKEY_LOCAL_MACHINEsoftwareDigital Protection
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallDigital Protection
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, "Digital Protection"
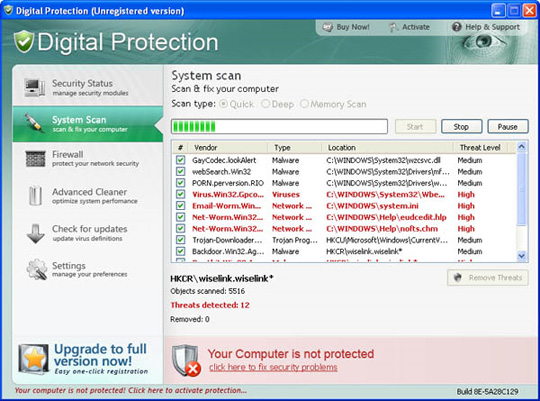
Some main images of Digital Protection:
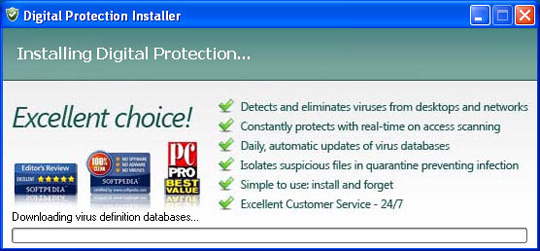
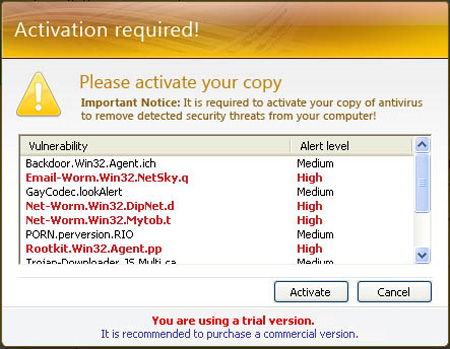
16. ErrorFix
Spread and spread widely through the website www.errorfix.org (this address is no longer available), the author of ErrorFix also created RegTool tool, both of which were discovered by Kaspersky Lab and identify not virus: FraudTool.Win32.ErrorFix.b .
When successfully installed on the computer, ErrorFix will continuously display information about the registry errors extremely seriously of Windows, and only when the user agrees to purchase the license key, the program will automatically fix Those serious errors.
ErrorFix will copy the following files to the hard drive after installing:
ErrorFix.exe
Icon.exe
definitions.db
privacy.db
ErrorFix.url
ErrorFix.lnk
ErrorFix Help.lnk
ErrorFix on the Web.lnk
ErrorFix Scan.job
Also create the following registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun "ErrorFix" = "C: Program FilesErrorFixErrorFix.exe -boot"
HKEY_CURRENT_USERSoftwareErrorFix
HKEY_LOCAL_MACHINESOFTWAREErrorFix
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstall {83A867EF-8D2E-4CAF-A1DD-B3996724CF78}
HKEY_CLASSES_ROOTInstallerUpgradeCodes2B6D4FBB6D32BEA409CCCEDDDBC9E08E
HKEY_CLASSES_ROOTInstallerFeaturesFE768A38E2D8FAC41ADD3B997642FC87
HKEY_CLASSES_ROOTInstallerProductsFE768A38E2D8FAC41ADD3B997642FC87
Main interface of the program:
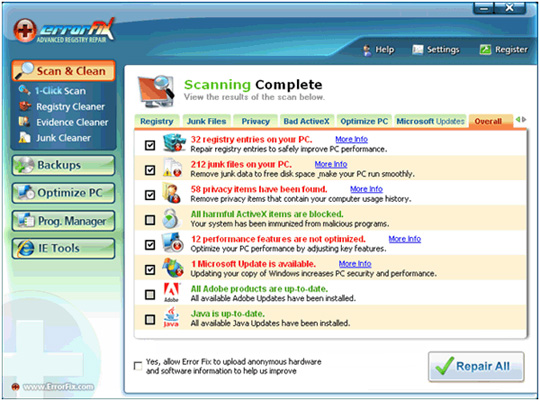
17. GuardWWW
GuardWWW, with its clever disguise, the program spreads very quickly and easily to many users' computer systems around the world. Widely distributed through the website www.guardwww.com (this address no longer exists), is a new variant of Winiguard / Winisoft series, besides the associated malicious applications such as:
PcsSecure, APcSafe, APcSecure, ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
When installed into the system, GuardWWW will automatically generate a certain number of empty files with different names, and when conducting a review, GuardWWW will detect these files themselves as read and virus codes, copper At the time of asking users to buy copyright, the key activates to 'root' treatment.
GuardWWW will automatically copy the following files to the hard drive:
% ProgramFiles% GuardWWW SoftwareGuardWWWalways_delete.xml
% ProgramFiles% GuardWWW SoftwareGuardWWWalways_skip.xml
% ProgramFiles% GuardWWW SoftwareGuardWWWGuardWWW.exe
% ProgramFiles% GuardWWW SoftwareGuardWWWmain_config.xml
% ProgramFiles% GuardWWW SoftwareGuardWWWuninstall.exe
% ProgramFiles% GuardWWW SoftwareGuardWWWquarantinequarantine.xml
% AllUsersProfile% DesktopGuardWWW.lnk
% AllUsersProfile% Start MenuProgramsGuardWWW2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsGuardWWW3 Uninstall.lnk
% AllUsersProfile% Start MenuProgramsGuardWWW1 GuardWWW.lnk
% UserProfile% Cookiesuserdemo @ guardwww [1] .txt
Also create the following keys in the registry:
HKEY_LOCAL_MACHINEsoftwareGuardWWW
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallGuardWWW
HKEY_CURRENT_USERsoftwareGuardWWW
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'GuardWWW'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'GuardWWW'
Some images of GuardWWW:

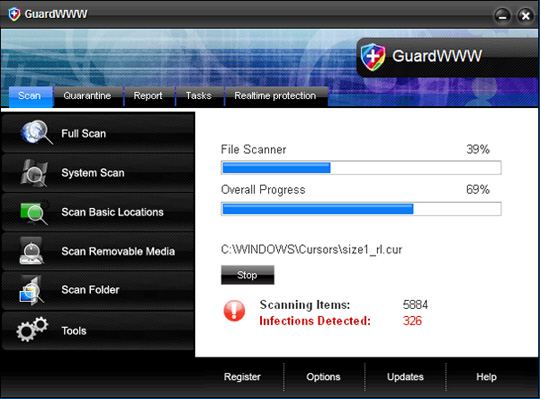
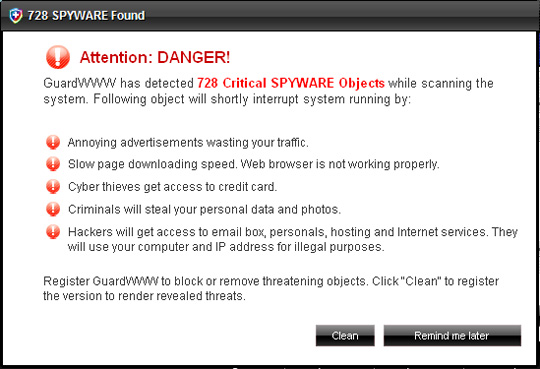
18. MyPcSecure
MyPcSecure - one of the fake security applications, is widely distributed via the address www.mypcsecure.com (this address no longer exists). In fact, this is a new variant of the Winiguard / Winisoft series, besides the following popular forms:
PcsSecure, APcSafe, APcSecure, ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
After completing the installation process, MyPcSecure will create a certain number of empty files with different names, and when conducting a full scan, MyPcSecure will detect and report those files as malicious code, also requires users to purchase activation keys to remove those malicious files.
Files generated during MyPcSecure installation:
% ProgramFiles% MyPcSecure SoftwareMyPcSecurealways_delete.xml
% ProgramFiles% MyPcSecure SoftwareMyPcSecurealways_skip.xml
% ProgramFiles% MyPcSecure SoftwareMyPcSecuremain_config.xml
% ProgramFiles% MyPcSecure SoftwareMyPcSecureMyPcSecure.exe
% ProgramFiles% MyPcSecure SoftwareMyPcSecureuninstall.exe
% ProgramFiles% MyPcSecure SoftwareMyPcSecurequarantinequarantine.xml
% AllUsersProfile% DesktopMyPcSecure.lnk
% AllUsersProfile% Start MenuProgramsMyPcSecure2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsMyPcSecure3 Uninstall.lnk
% AllUsersProfile% Start MenuProgramsMyPcSecure1 MyPcSecure.lnk
% UserProfile% Cookiesuserdemo @ mypcsecure [1] .txt
Also create the registry keys:
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallMyPcSecure
HKEY_LOCAL_MACHINEsoftwareMyPcSecure
HKEY_CURRENT_USERsoftwareMyPcSecure
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'MyPcSecure'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'MyPcSecure'
Some pictures of the program:

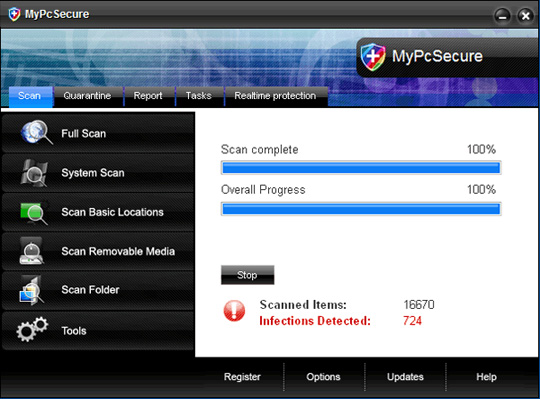
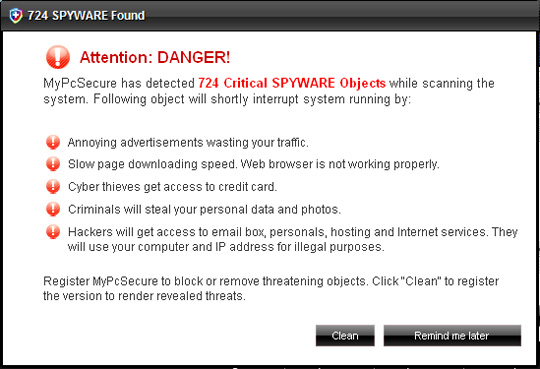
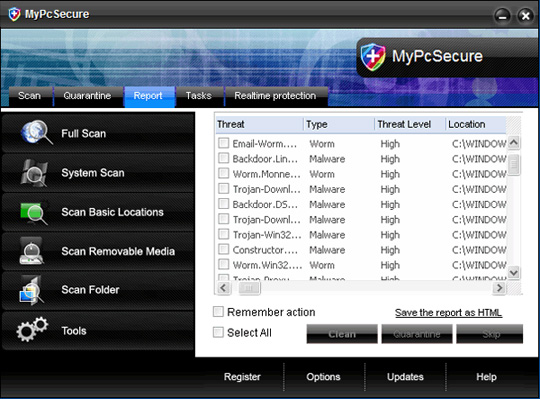
19. My Security Engine
My Security Engine with the mechanism to create the boot path with the system, and each time so, the program will create and copy a lot of junk data into many different folders on all partitions. And each time it starts and scans, the number of junk files will increase faster and more. To remove these files, the program requires users to purchase copyright or application activation code.
Files created and copied to the hard drive:
% AllUsersProfile% Application Data% random% MSE.ico
% AllUsersProfile% Application Data% random% MSf4c.exe
% UserProfile% Application DataMicrosoftInternet ExplorerQuick LaunchMy Security Engine.lnk
% UserProfile% Application DataMy Security Enginecookies.sqlite
% UserProfile% Application DataMy Security EngineInstructions.ini
% UserProfile% DesktopMy Security Engine.lnk
% UserProfile% Recentsnl2w.dll
% UserProfile% Recentsnl2w.drv
% UserProfile% Recentstd.exe
% UserProfile% Recentstd.tmp
% UserProfile% Recentcid.tmp
% UserProfile% RecentDBOLE.tmp
% UserProfile% Recenteb.dll
% UserProfile% Recenteb.tmp
% UserProfile% Recentenergy.exe
% UserProfile% Recentexec.sys
% UserProfile% Recentfix.dll
% UserProfile% Recentfix.drv
% UserProfile% RecentFW.exe
% UserProfile% Recentpal.drv
% UserProfile% RecentPE.dll
% UserProfile% Recentrunddlkey.sys
% UserProfile% Start MenuMy Security Engine.lnk
% UserProfile% Start MenuProgramsMy Security Engine.lnk
Also the following registry keys are created:
Table of registry keys
On the other hand, My Security Engine also prevents access to some websites by changing the HOSTS file system. The following information has been changed in the HOSTS file:
127.0.0.1 localhost
74.125.45.100 4-open-davinci.com
74.125.45.100 securitysoftwarepayments.com
74,125.45,100 privatesecuredpayments.com
74.125.45.100 secure.privatesecuredpayments.com
74,125.45.100 getantivirusplusnow.com
74.125.45.100 secure-plus-payments.com
74.125.45.100 www.getantivirusplusnow.com
74.125.45.100 www.secure-plus-payments.com
74.125.45.100 www.getavplusnow.com
74.125.45.100 safebrowsing-cache.google.com
74,125.45,100 urs.microsoft.com
74.125.45.100 www.securesoftwarebill.com
74.125.45.100 secure.paysecuresystem.com
74,125.45,100 paysoftbillsolution.com
74,125,45,100 protected.maxisoftwaremart.com
209.212.147.138 www.google.com
209,212,147,138 google.com
209,212,147,138 google.com.au
209.212.147.138 www.google.com.au
209,212,147,138 google.be
209.212.147.138 www.google.be
209,212,147,138 google.com.br
209.212.147.138 www.google.com.br
209,212,147,138 google.ca
209.212.147.138 www.google.ca
209,212,147,138 google.ch
209.212.147.138 www.google.ch
209,212,147,138 google.de
209.212.147.138 www.google.de
209,212,147,138 google.dk
209.212.147.138 www.google.dk
209,212,147,138 google.fr
209.212.147.138 www.google.fr
209,212,147,138 google.ie
209.212.147.138 www.google.ie
209,212,147,138 google.it
209.212.147.138 www.google.it
209,212,147,138 google.co.jp
209.212.147.138 www.google.co.jp
209,212,147,138 google.nl
209.212.147.138 www.google.nl
209,212,147,138 google.no
209.212.147.138 www.google.no
209,212,147,138 google.co.nz
209.212.147.138 www.google.co.nz
209,212,147,138 google.pl
209.212.147.138 www.google.pl
209,212,147,138 google.se
209.212.147.138 www.google.se
209,212,147,138 google.co.uk
209.212.147.138 www.google.co.uk
209,212,147,138 google.co.za
209.212.147.138 www.google.co.za
209.212.147.138 www.google-analytics.com
209.212.147.138 www.bing.com
209.212.147.138 search.yahoo.com
209.212.147.138 www.search.yahoo.com
Uk.search.yahoo.com 209,212,147,138
209,212,147,138 ca.search.yahoo.com
209,212,147,138 de.search.yahoo.com
209,212,147,138 fr.search.yahoo.com
209,212,147,138 au.search.yahoo.com
The most obvious symptom of this phenomenon is that the user cannot connect to the homepage www.kaspersky.com, and is related to the following products:
- Kaspersky Anti-Virus 6.07.02009 (all versions)
- Kaspersky Internet Security 6.07.02009 (all versions)
- Kaspersky Anti-Virus 5.0 Personal (all versions)
- Kaspersky Anti-Virus 5.0 Personal Pro (all versions)
- Kaspersky Anti-Hacker 1.8
- Kaspersky Anti-Virus 5.06.0 for Windows Workstations (all versions)
- Kaspersky Anti-Virus 5.06.0 SOS
To temporarily fix this phenomenon, you can apply the following manually: find the location of the HOSTS file system (with Windows-95/98 / ME at the root of the system installation, with Windows NT / 2000 / XP / Vista / 7 in the System32 / drivers / etc folder, open the file with any editing program (eg NotePad, WordPad) under Administrator, delete all the addresses except 127.0 .0.1 localhost. Or replace with HOSTS file provided by Kaspersky here.
Main interface of the program:
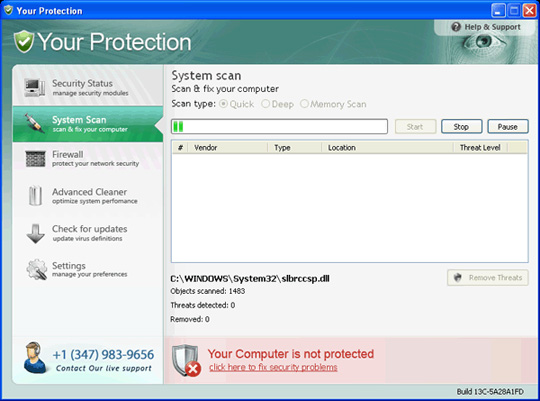
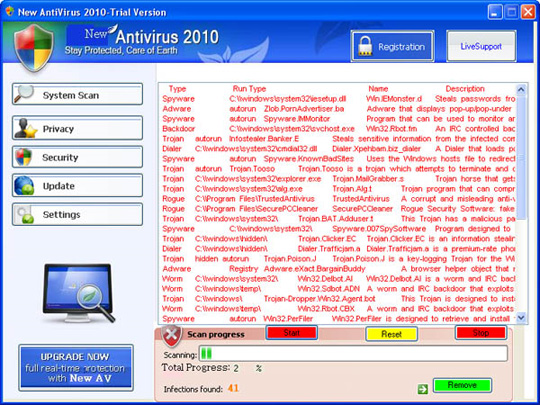
20. New Antivirus 2010
When successfully penetrating and installing on victim computers, New Antivirus 2010 will continuously give false warnings about viruses, Trojans and worms detected on the system, and require users to buy copyright. or activation key to use all functions and kill all viruses that are alerted on the system.
The following files are copied to the system drive by New Antivirus 2010:
% Documents and Settings% All UsersStart MenuProgramsNew Antivirus 2010
% Documents and Settings% All UsersDesktopNew Antivirus 2010.lnk
% Documents and Settings% All UsersApplication DataMicrosoftMachineWStech.dll
And continue to create the following registry keys:
HKEY_LOCAL_MACHINESOFTWARENew Antivirus 2010
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun "New Antivirus 2010"
Main interface of the program:
21. PcSecureNet
PcSecureNet is a new variant of Winiguard / Winisoft series, spread and spread widely through the address www.pcsecurenet.com (which no longer exists), besides the following notable variations:
PcsSecure, APcSafe, APcSecure, ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
With the popular spread method, PcSecureNet will continuously create a certain number of empty files with many different names after successfully installing the victim's computer. And when the user scans the entire system, PcSecureNet will detect and warn those files that are malicious, and 'entice' users to buy the license or activation key.
The following files were created and copied during installation:
% ProgramFiles% PcSecureNet SoftwareApcSafePcSecureNet.exe
% ProgramFiles% PcSecureNet SoftwareApcSafemain_config.xml
% ProgramFiles% PcSecureNet SoftwareApcSafeuninstall.exe
% AllUsersProfile% DesktopPcSecureNet.lnk
% AllUsersProfile% Start MenuProgramsPcSecureNet1 PcSecureNet.lnk
% AllUsersProfile% Start MenuProgramsPcSecureNet2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsPcSecureNet3 Uninstall.lnk
and the following registry keys:
HKEY_LOCAL_MACHINEsoftwarePcSecureNet
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallPcSecureNet
HKEY_CURRENT_USERsoftwarePcSecureNet
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'PcSecureNet'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'PcSecureNet'
Some main images of PcSecureNet:
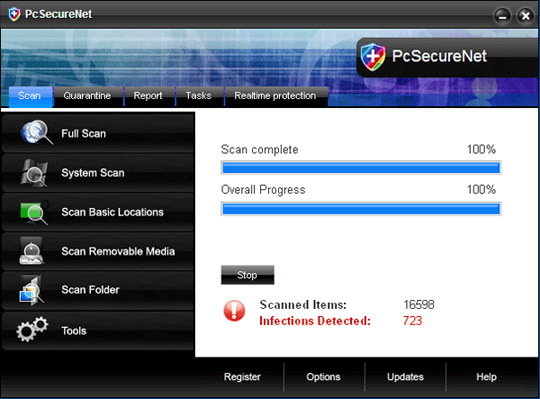
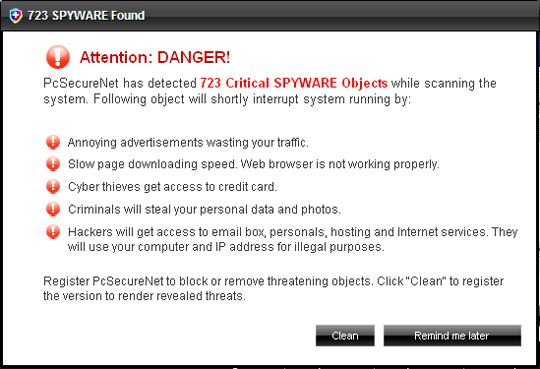
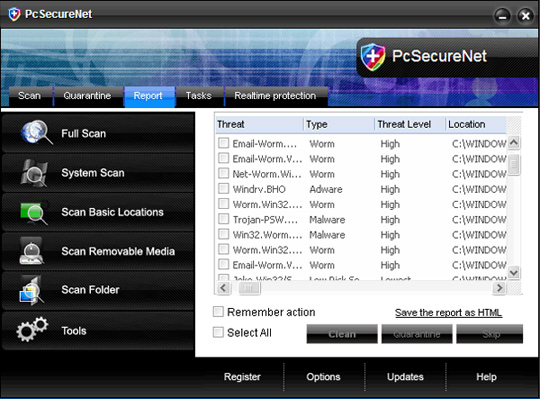
22. PcsSecure
PcsSecure - similar to PcSecureNet, is a variant of Winiguard / Winisoft, distributed and transmitted via www.pcssecure.com (no longer exists), besides there are many similar variants. as:
APcSafe, APcSecure, ProtectSoldier, ProtectDefender, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
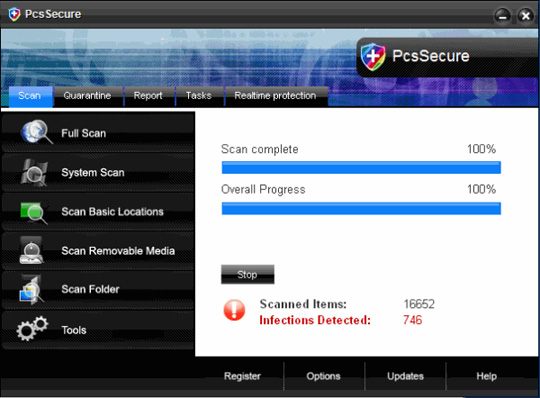
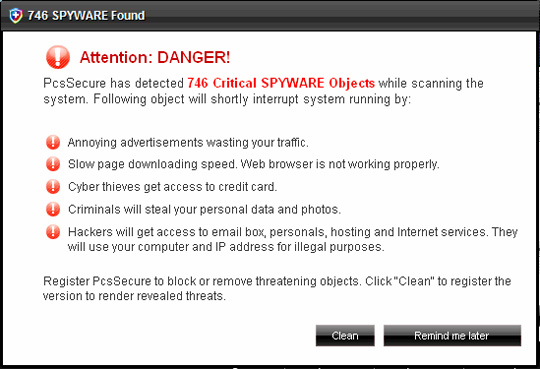
After penetrating and successfully installing the victim's computer, PcsSecure will create a certain number of empty files with different names, each time scanning, PcsSecure will warn users about these files. is a malicious code or virus, and only waits for the user to agree to purchase the license or activation code.
When installing, PcsSecure will create the following files:
% ProgramFiles% PcsSecure SoftwarePcsSecurealways_delete.xml
% ProgramFiles% PcsSecure SoftwarePcsSecurealways_skip.xml
% ProgramFiles% PcsSecure SoftwarePcsSecuremain_config.xml
% ProgramFiles% PcsSecure SoftwarePcsSecurePcsSecure.exe
% ProgramFiles% PcsSecure SoftwarePcsSecureuninstall.exe
% ProgramFiles% PcsSecure SoftwarePcsSecurequarantinequarantine.xml
% AllUsersProfile% DesktopPcsSecure.lnk
% AllUsersProfile% Start MenuProgramsPcsSecure1 PcsSecure.lnk
% AllUsersProfile% Start MenuProgramsPcsSecure2 Homepage.lnk
% AllUsersProfile% Start MenuProgramsPcsSecure3 Uninstall.lnk
% UserProfile% Cookiesuserdemo @ pcssecure [1] .txt
And the same keys in the registry:
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionUninstallPcsSecure
HKEY_LOCAL_MACHINEsoftwarePcsSecure
HKEY_CURRENT_USERsoftwarePcsSecure
HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionRun, 'PcsSecure'
HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionRun, 'PcsSecure'
Some pictures of the program:

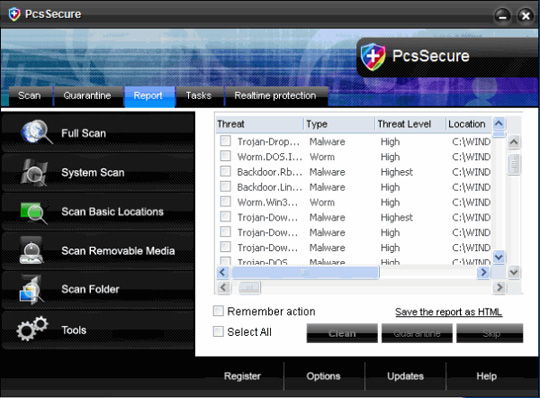
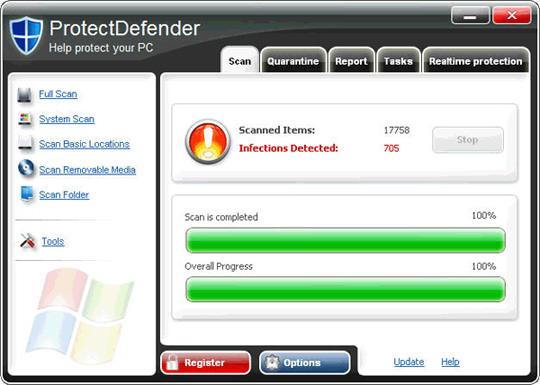
23. ProtectDefender
Widely distributed through www.protectdefender.com (this address is no longer available), ProtectDefender is also a popular variant of the 'family' Winiguard / Winisoft, besides the ' colleagues' later:
APcSafe, APcSecure, ProtectSoldier, ArmorDefender, DefendAPc, SysDefenders, InSysSecure, SysProtector, APcDefender, PcProtectar, PcsProtector, GreatDefender, APCProtect, ProtectPcs, SysDefence, TheDefend, GuardPcs, IGuardPc, SiteAdware, AntiTroy, AntiKeep, AntiAdd, RESpyWare, REAnti, KeepCop, SecureKeeper, LinkSafeness, AntiAid, SystemFighter, SystemVeteran, BlockProtector, BlockKeeper, BlockScanner, BlockWatcher, SoftStronghold, ShieldSafeness, SoftVeteran, SoftSoldier, SoftCop, TrustFighter, TrustSoldier, SafeFighter, SecureVeteran.
When successfully infiltrating the victim's computer, ProtectDefender will constantly generate a certain number of empty files in the system folder C: Windows and C: WindowsSystem32 , and of course, when booting or scanning the entire system The system, ProtectDefender will warn you to detect a lot of malicious code in the computer, and ask the user to buy the license or activation code.
The following files are created by ProtectDefender during installation:
% UserProfile% DesktopProtectDefender.lnk
% UserProfile% Start MenuProgramsProtectDefender.lnk
c: Program FilesProtectDefender Software
c: Program FilesProtectDefender SoftwareProtectDefender
c: Program FilesProtectDefender SoftwareProtectDefenderProtectDefender.exe
c: Program FilesProtectDefender SoftwareProtectDefenderUninstall.exe
c: WINDOWS59zwo5m236.ocx
c: WINDOWS980haczt9ol3e5.bin
c: WINDOWSsystem3228downlo5dez11979.bin
c: WINDOWSsystem329zbackdoor1975.bin
c: WINDOWSsystem3299zir5s6ef.ocx
And the following registry keys:
HKEY_CURRENT_USERSoftwareProtectDefender
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstallProtectDefender
HKEY_LOCAL_MACHINESOFTWAREProtectDefender
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun "ProtectDefender"
Main interface of the program:
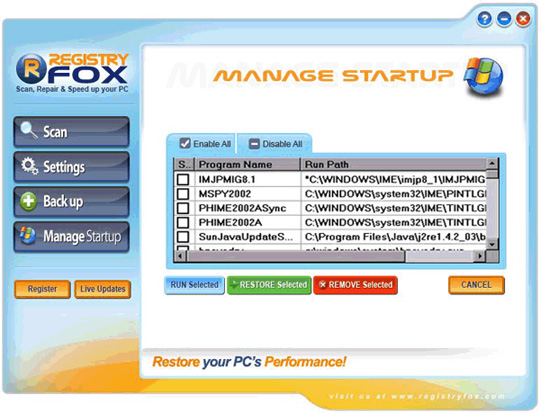
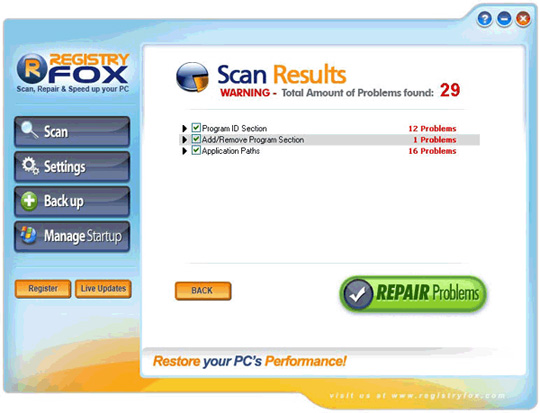
24. RegistryFox
It is a fake security software, cleverly disguised as a virus scanning application and scans the Windows registry system. RegistryFox is widely distributed through the website www.registryfox.com , but Kaspersky Lab found that it is not the FraudTool.Win32.RegistryFox.a virus.
When successfully installed on the victim's computer, RegistryFox will continuously generate false warning information about the critical error status in the operating system registry. Only when the user agrees to purchase the license key, RegistryFox will stop the notification and "fix" those errors.
RegistryFox will copy the following files to the victim's computer:
C: Config.Msi4f7ea.rbs
% ProgramFiles% RegistryFox
% ProgramFiles% RegistryFoxRegistryFox.url
% ProgramFiles% RegistryFoxRegistryFox.exe
% ProgramFiles% RegistryFoxTCL.dll
% ProgramFiles% RegistryFoxRegCleaner.dll
% ProgramFiles% RegistryFoxDataBase.ref
% ProgramFiles% RegistryFoxzlib.dll
% AllUsers% Start MenuProgramsRegistryFox
% AllUsers% Start MenuProgramsRegistryFoxRegistryFox.lnk
%% AllUsers DesktopRegistryFox.lnk
% AllUsers% Start MenuProgramsRegistryFoxRegistryFox on the Web.lnk
C: WINDOWSInstaller4f7eb.msi
and the following main registry key:
HKCUSoftwareMicrosoftWindowsCurrentVersionRunRegistry Fox
Some pictures of the program:

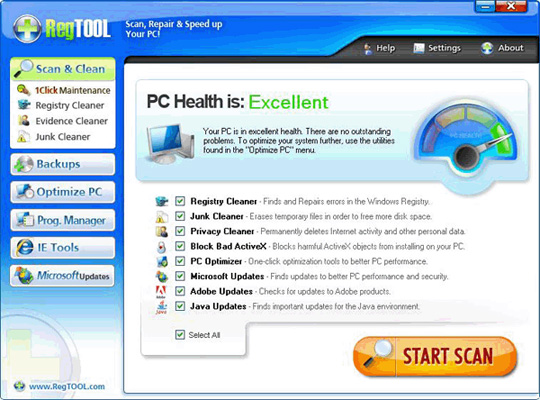
25. RegTool
With the same operation and spread as ErrorFix, RegTool is primarily distributed via www.regtool.com , but Kaspersky Lab does not list this fake program as FraudTool.Win32.RegTool.b .
When RegTool is successfully installed, when the user activates a feature in the registry, the program will warn the system with a serious registry error, and ask the user to purchase a license to activate the license.
RegTool will copy the following files to the system partition after installation:
regtool.exe
regtool5.dll
RegTool.lnk
and the following registry keys:
HKEY_CURRENT_USERSoftwareRegTool
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun "RegTool"
Main interface of the program:
26. RST Antivirus 2010
RST Antivirus 2010 was discovered by Kaspersky Lab and listed in Trojan.Win32.FakeAV.pz 's variant list, and distributed widely via the website http://rtsantivirus2010.com/ . When successfully entering the victim's computer, RST Antivirus 2010 will constantly generate error messages about viruses, Trojans and worms that exist on the system, and RST Antivirus 2010 will thoroughly overcome these errors when people Use to agree to buy a license to activate copyright.
After installing the computer, RST Antivirus 2010 will copy the following files to the hard drive:
% ProgramFiles% adc32.dll
% ProgramFiles% alggui.exe
% ProgramFiles% nuar.old
% ProgramFiles% skynet.dat
% ProgramFiles% svchost.exe
% ProgramFiles% wp3.dat
% ProgramFiles% wp4.dat
% ProgramFiles% rst antivirus 2010rst antivirus 2010.exe
% ProgramFiles% rst antivirus 2010comdlg32.dll
% ProgramFiles% rst antivirus 2010dwmapi.dll
% ProgramFiles% rst antivirus 2010libclamav.dll
% ProgramFiles% rst antivirus 2010oledlg.dll
% ProgramFiles% rst antivirus 2010pthreadvc2.dll
% ProgramFiles% rst antivirus 2010uninstall.bat
% ProgramFiles% rst antivirus 2010wininet.dll
% Programs% RTS Antivirus 2010.lnk
% Desktop% RTS Antivirus 2010.lnk
and the following registry keys:
HKCUSoftwareRTS Antivirus 2010
HKCRCLSID {77DC0Baa-3235-4ba9-8BE8-aa9EB678FA02}
HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects {77DC0Baa-3235-4ba9-8BE8-aa9EB678FA02}
HKLMSYSTEMCurrentControlSetServicesAdbUpd
Main interface of the program RST Antivirus 2010:

( Also )