Learn about the Cross-Site Request Forgery attack method
Cross-site request forgery (XSRF or CSRF) is a method of attacking a website in which a fraudulent intruder is a legitimate and reliable user.
What is Cross-Site Request Forgery?
A XSRF attack can be used to modify firewall settings, post unauthorized data on forums or perform fraudulent financial transactions. A attacked user may never know he has become a victim of XSRF. Even if the user has discovered this attack, it is only after the hacker has caused certain damage and has no means to remedy the problem.

How was the Cross-site request forgery carried out?
A XSRF attack can be done by stealing the identity of an existing user, then hacking into the web server with the identity stolen before. An attacker can also trick legitimate users into accidentally sending Hypertext Transfer Protocol (HTTP) requests and returning sensitive user data to intruders.
Is Cross-Site Request Forgery similar to Cross-site scripting or Cross-site tracing?
A XSRF attack in terms of functionality is contrary to Cross-site scripting (XSS) attacks, in which hackers insert malicious code into links on a website, apparently from a trusted source. When the end user clicks on the link, the embedded program is sent as part of the request and can be executed on the user's computer.

The XSRF attack is also different from Cross-site tracing (XST), a sophisticated XSS format that allows intruders to get cookies and other authentication data using a simple client-side script. In XSS and XST, end users are the main target of the attack. In XSRF, Web server is the main target, although the harm of this attack is borne by end users.
Cross-site danger level requests forgery
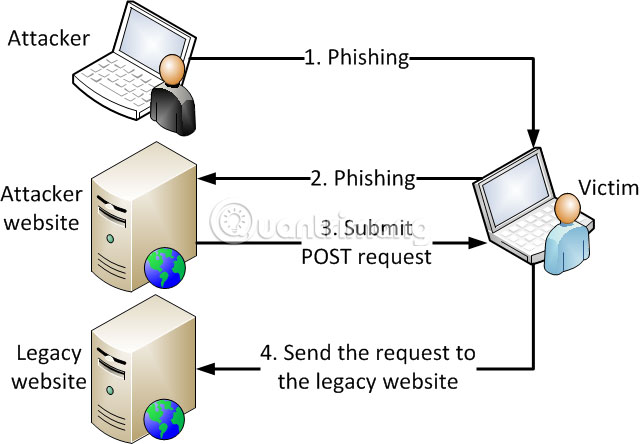
XSRF attacks are harder to prevent than XSS or XST attacks. Partly because the XSRF attacks are less common and do not get much attention. On the other hand, in fact, it is difficult to determine whether an HTTP request from a particular user is actually sent by the person himself. Although strict precautions can be used to verify the identity of the user trying to access the site, users are not "keen" with frequent authentication requests. The use of encrypted tokens can provide regular authentication in the background so that users are not constantly bothered by authentication requests.