Remedies of Windows XP / Vista Recovery
TipsMake.com - For current system cleanup programs, the general use is to 'clean' the entire temp folder before proceeding with other processes. The purpose of this process is often quite good, because this is also the place to stay for malicious programs, malware, viruses . so it will significantly shorten the processing time after this. But it is not only us who know how to do this, but the hackers also grasp this simple principle, so hackers have continued to create some fake security software with the purpose of trying to properties to move important users' files or data to this temp folder.
The most common common cases are fake Recovery Software and Windows Restore security in today's Windows XP or Vista operating system, many of the user's system files will be "secretly" transferred to the directory % temp% smtmp . After the system is infected, you absolutely cannot delete the data in this directory as you normally would, or use other support tools such as CCleaner . until the recovery process is completed. and everything is back to normal.
More specifically, these fake programs will temporarily hide and transfer all desktop shortcuts and Start Menu shortcuts to the % temp% smtmp folder , then continue to create 4 more subdirectories:
% Temp% smtmp1 => Allusers Start Menu
% Temp% smtmp2 => Allusers Quick Launch
% Temp% smtmp3 => Quick LaunchUser PinnedTaskBar
% Temp% smtmp4 => AllUsers Desktop
If you don't 'clean' the temp folder, you can restore these shortcuts, and in the other case, use the restoresm utility to retrieve commonly used shortcuts (download, extract and run restoresm.bat file).
Some steps to follow:
To continue, please follow the instructions as shown below. Specifically, we will learn more about the Windows Recovery spoofing program - cleverly disguised under the guise of a system analysis and optimization utility, after installing it into Windows they will work and provides a lot of false information and the current state of the operating system, and offers measures to improve by advanced functions - these functions are only activated when the user agrees to pay through a Number of common forms. And essentially, Windows Recovery is installed via the Trojan route infecting Windows, the next time the program will start automatically with the system, and for each such time, the messages are false about The status of the operating system, storage partition, or hard drive is displayed.
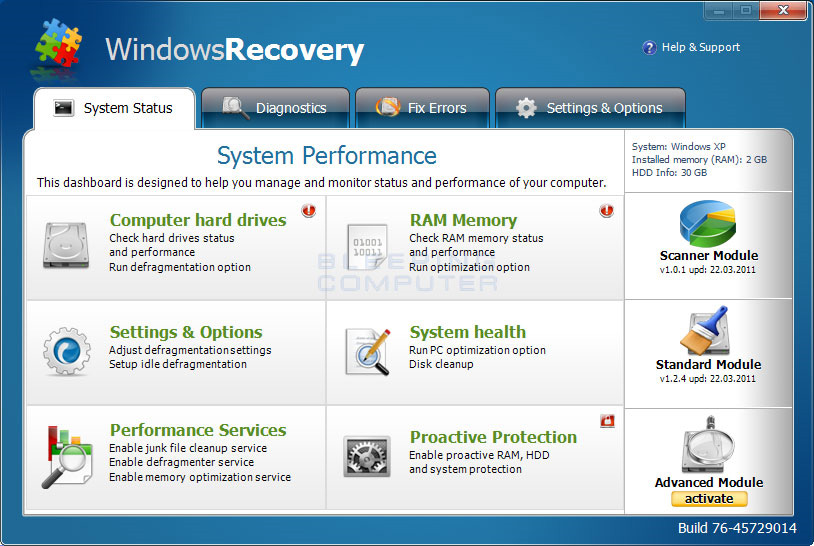
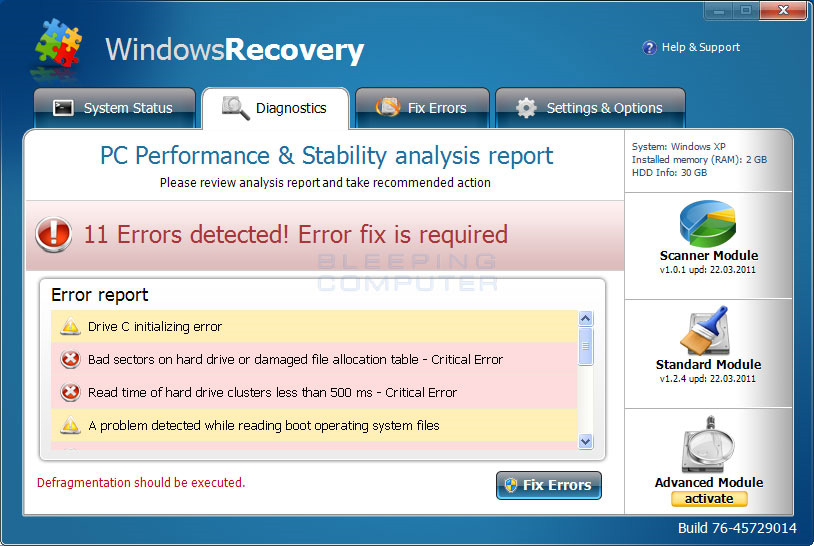
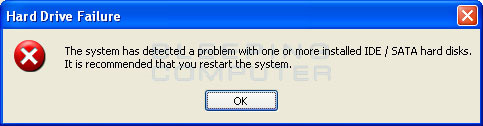
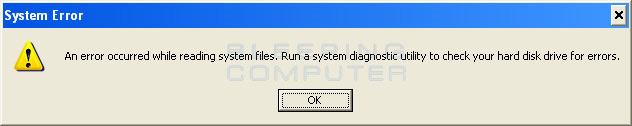
Some pictures of fake Windows Recovery program
On the other hand, in order for users to "trust" that the operating system is in an unstable state, Windows Recovery has made the internal data part of the folders 'disappear' completely, for example when users open some paths like C: WindowsSystem32 , instead of seeing the list of system folders and files as usual, they will only see a few different folders, which do not contain any data. They do this by secretly adding hidden - hidden properties and file and folder files, and changing Windows' display mechanism, so users cannot see hidden files and folders. .
Besides, Windows Recovery also makes it impossible for users to boot and use any programs on the computer. The manifestation of this is that when you start any program, the program will automatically disappear, and instead report an error that the application or storage hard drive is having problems. The purpose of hackers doing this is to protect the fake program from other security software. Common error messages look like this:
Hard Drive Failure
Đã tìm thấy hệ thống một vấn đề với một hay nhiều cài đặt IDE / SATA hard đĩa. Có nên thử lại bạn chạy lại hệ thống.
System Error
Lỗi lỗi khi đọc hệ thống tập tin. Đang chạy một thiết bị xác định hệ thống để kiểm tra các đĩa đĩa cứng cho lỗi.
Critical Error
Hard drive critical error. Đang chạy một thiết bị xác định hệ thống để kiểm tra các đĩa đĩa cứng cho lỗi. Windows không tìm thấy đĩa đĩa cứng. Hard drive error.
After closing these messages, the system continues to offer several options as follows:
Fix Disk
Windows Recovery Diagnostics will scan the system to identify problems.
Start or Cancel
If you select Start, the program will start to review, and display some results similar to the following:
Windows Recovery Diagnostics
Windows tìm thấy một lỗi tập tin cứng.
Một vấn đề với các rãnh ghi ổ cứng đã được tìm thấy. Nếu được thử lại để tải tập tin sertified theo đây để kiểm tra các lỗi không tìm thấy problems. Bạn có muốn tải hợp lệ software?
That's just a few warning messages trying to convince users that the operating system is experiencing serious problems related to the hard drive:
Không cho phép đăng nhập đăng nhập được phép Registry defragmentation required
Đọc thời gian của của của của của máy ảnh cứng nhỏ hơn 500 ms
32% of HDD space is unreadable
Bad các rãnh ghi trên bàn phím bị lỗi hoặc bị hỏng
RAM GPU temperature is critically high. Urgent bộ nhớ RAM (RAM) cần thiết cần thiết bị hỏng
Drive C initializing error
Ram Temp is 83 C. Optimization là cần thiết cho kích cỡ chính quy.
Hard drive không đáp ứng đến system lệnh
Data Safety Problem. System integrity is at risk.
Registry Error - Critical Error
Besides, while WindowsRecovery works, the program will continuously display false information from the Windows taskbar. Examples are as follows:
Critical Error!
Lỗi tìm thấy trình điều khiển clusters. Private data is at risk.
Critical Error
Không tìm thấy Hard Drive. Missing hard drive.
Critical Error
RAM memory usage is critically high. RAM memory failure.
Critical Error
Windows không tìm thấy đĩa đĩa cứng. Hard drive error
Critical Error!
Windows không thể lưu các dữ liệu cho tập tin System32496A8300. Tập tin đã bị mất. Có lẽ lỗi này bị lỗi với một lỗi máy tính của bạn.
Critical Error
Lỗi lỗi khi đã xác định khi chỉ mục được lưu trữ dữ liệu trên ổ cứng. Cần thiết bị khởi động
System Restore
Hệ thống đã được xác định sau khi lỗi lỗi. Chỉ xác thực dữ liệu và thiết bị cứng xác thực
Activation Reminder
Windows Recovery Activation
Advanced module activation required to fix errors and performance issues. Please purchase Advanced license module to activate this software and enable all features.
Low Disk Space
Bạn đang chạy một đĩa bên ngoài không trên địa chỉ đĩa (C :).
Windows - No Disk
Exception Processing Message 0x0000013
To fix it, you will need some support tools as follows:
- FixNCR.reg: use this file to be able to use executable files * .exe
- Rkill: run this file to remove active processes of malware
- RogueKiller: Another way to stop malware activity before using MalwareBytes
- Unhide: use this file to remove hidden properties of files and folders after being infected
- TDSSKiller: remove the type of rootkit TDSS exists on the system
Note that you should not reboot after using RKill or RogueKiller or the processes generated by malware will automatically reappear, users must use MalwareBytes immediately, fully updated and scanned. ( Full scan ) the entire system to eradicate threats.
In addition, if the order of the data files and programs used to open is disturbed or affected by the infection process, please refer here to fix:
- Dougknox XP is used on Windows XP
- With Windows Vista
- Windows 7
Continue, to restore the Accessories Program Files menu, we can use accrestore.zip, after downloading, you unzip and run the file AccRestore.exe, click the Restore button to proceed.
To restore the Admin Tools Program Files menu , use admintools.zip - unzip, activate the * .exe file and click the Restore Administrative Tools items button .
Good luck!