New FileFix Attack Can Bypass Windows MoTW: How to Protect Your Computer?
FileFix is a new attack method that takes advantage of the way Windows and browsers handle the HTML web page saving process to bypass Windows security checks. If done correctly, it can compromise Windows systems to launch ransomware attacks , harvest login credentials, and even install new malware. This guide lists all the measures you can take to protect your PC from the FileFix attack.
How the FileFix attack works
Revealed by security researcher mr.d0x, FileFix takes advantage of the way Windows handles local HTML application files and the Mark of the Web (MoTW) security feature. Whenever you save a web page using the "Save as" function, your browser will not tag the web page for MoTW, which is supposed to require security features (like Windows Security ) to scan the file.
Additionally, if the file is saved as an .hta (HTML application file), it can be executed directly as the current user without any security checks. If a malicious website convinces a user to save the page and also renames it to an .hta extension, malicious code will be downloaded and executed (when the user opens the file) without being detected by Windows security.
The main difficulty is convincing users to save the malicious page as an HTML application file. However, like EDDIESTEALER, this can be done using cleverly executed social engineering attacks , such as convincing users to save their MFA code with a specific name ending in .hta.
Fortunately, there are several blocking points to block this attack on PC. Here are the most reliable ones.
Avoid malicious websites
The attack starts by caching a malicious website, so if you don't visit the malicious site, you won't be targeted by this attack (and many others). Make sure you're using a modern browser like Chrome, Edge, Firefox, etc., as they have built-in anti- phishing and anti-malware protection. Also, on Chrome, turn on Enhanced Protection for AI-based protection that detects threats in real time.
Malicious websites are often distributed via phishing emails to pretend to be legitimate sites, so learn how to recognize phishing emails and avoid clicking on them as much as possible. If you accidentally land on a suspicious site without warning, there are ways to determine whether the site is legitimate or not.
Show file extensions in Windows
By default, Windows 11 hides file extensions and only shows the file name. FileFix indirectly takes advantage of this, as users may not notice the .html extension changing to .hta when the file extension is not visible. You can enable this feature to always see what the original file type was and whether it has been changed.
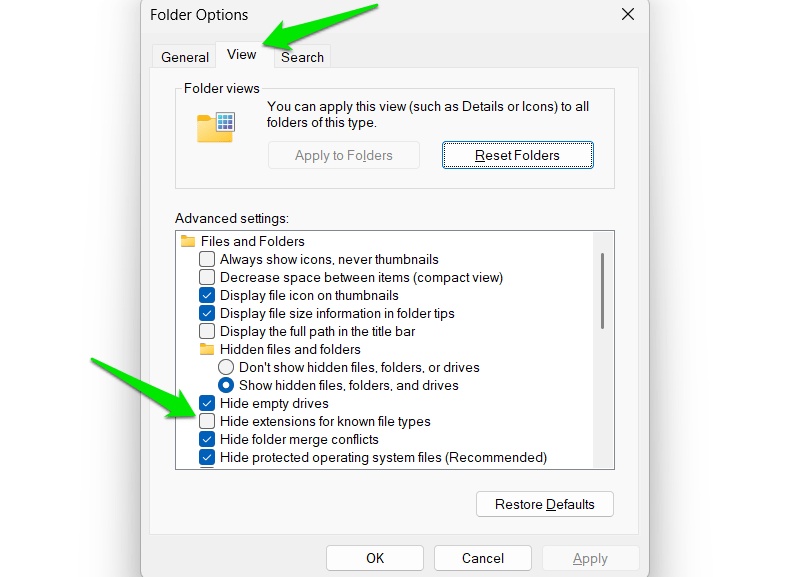
In File Explorer, click the See more button (three dots) and select Options .
Here, go to the View tab and uncheck the Hide extensions for known file types option .
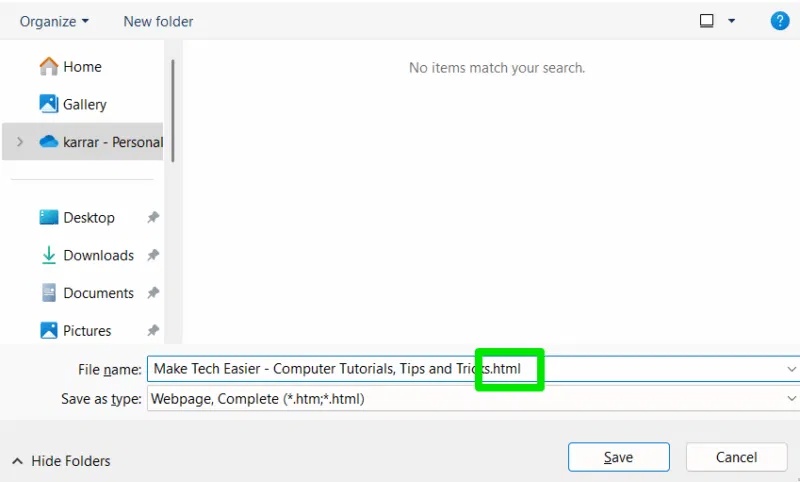
Now you will always see the file extension even in the download window when saving a web page.
Change .hta file association to Notepad
By default, Mshta is an application that runs .hta files to execute HTML application functions directly. However, if you change the .hta file association to Notepad, the application will open the file in a text editor when executed. So even if someone tricks you (or someone else on your PC) into downloading a malicious .hta file, it will not execute.
This won't affect most users as the use of .hta scripts is fairly limited and is typically only used by IT admins or for some legacy scripts in corporate environments. Unless you are heavily reliant on .hta scripts, this won't affect you.
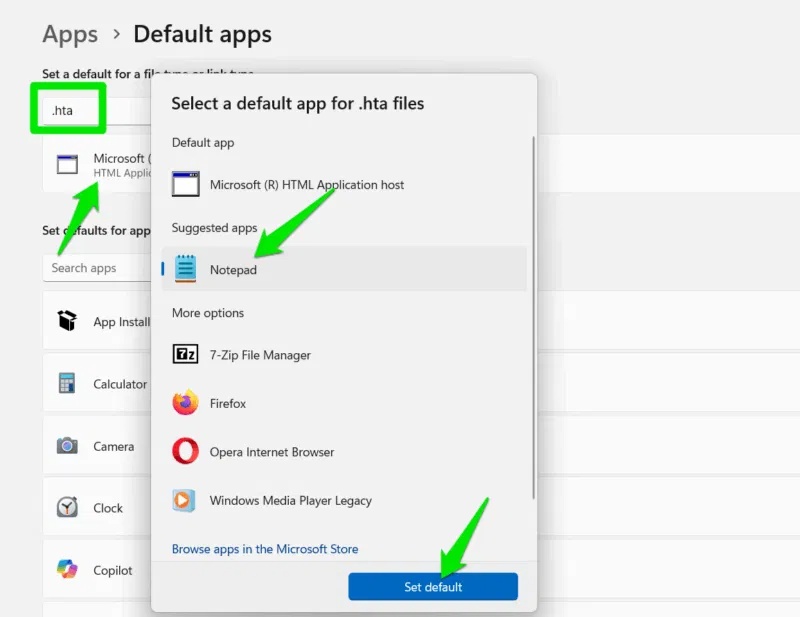
In Windows Settings, go to Apps -> Default Apps and search for '.hta' in the top search bar under Set a default for a file type or link type .
Now, click on Microsoft (R) HTML Application host , select Notepad as the default application and click Set default . Now, all .hta files will open in Notepad.