Web5: SQL injection - Some techniques to bypass the filtering mechanism
1. Truncate the content of the query
In case you want to ignore the scripts in the query. For example, for the following processing, the query requires active=1 condition but we can comment (--, -- -, -+, #, /*, /**/, // , ;%00…) and ignore it. When mining, we often don't know what the rest of the query does, so using comments in this case is very effective.

After commenting, our query becomes:

2. Bypass the filtering of keywords
a. Inline Comments
Inline comments are used very effectively in bypassing whitespace filtering. The following characters can be used to bypass whitespace filtering: /**/, %20, %09, %0a, %0b, %0c, %0d, %a0). For example:

Or bypass keyword filtering (available with MySql). In the example below, the keyword union and password are in the blacklist and have been blocked, we can bypass it by:

b. Replace keywords
When exploiting SQL injection we often use keywords like: union, select, information_schema. In many cases programmers simply replace those keywords:
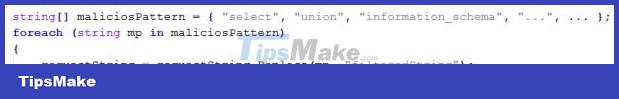
We can easily see that the above processing code is lacking. If it's simply pattern matching, the bypass is extremely simple. Let's apply case sensitive, where uppercase and lowercase letters are interpreted differently.
Now instead of using the keyword:
select, union… We will use:
SeLEcT, UniOn…The basis of this bypass is that database management systems are not case sensitive for keywords.
In some cases, the web application will filter out all or part of certain keywords (union, select.). We will bypass as follows:
id=1+uniunionon+SeLselectecT+1,2,3-- -After the union and select are filtered out by the web application, we will be left with the following correct query:
id=1+union+SeLecT+1,2,3-- -c. Character encoding
We can bypass when WAF (Web Application Firewall) blocks keywords by encoding them. Many WAF applications will only decode the query once and filter out the keywords in the blacklist, then let's encode the request twice so it can be bypassed in this case.
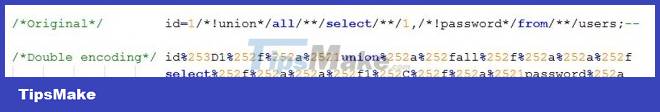
3. Bypass blocks single and double quotes
- Let's look at an example before learning specifically how to bypass this.

In this scenario, we already know a table in the database named users. The next job is to know the column name in the table to get its information. As in the above query, we use the condition: table_name='users'. But if both single quotes (') and double quotes (") are blocked by WAF, we can no longer use 'users' or "users". The built-in database system gives us a very good function to solve this problem, which is the CHAR() function (for Oracle, CHR()). For example, in the above query we will bypass by:
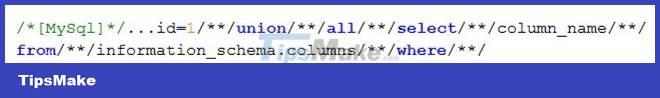
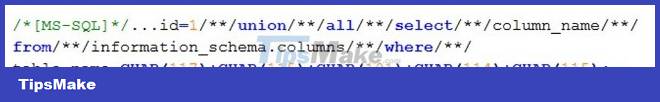
PHP programmers are all familiar with the addslashes() function. The addslashes() function has the effect of prepending special characters such as single quotes ('), double quotes ("), backslash(), NUL (null bytes) character "" to help the database management system not So, when we want to inject the query according to the script: name='someName' or '1'='1'-- the result is difficult and confusing. The results are no longer what we expected.
However, there is a technique to bypass the addslashes() function to inject the apostrophe ('). This technique has been public for quite some time, and to implement this technique is quite difficult because it is tied to the coding style applied to the website.
4. Bypass "illegal mix of collation for operation UNION" error
In some management systems (usually found in MySql), databases and tables when collation is set, when using the UNION keyword, the error "illegal mix of collation for operation UNION" will be reported. The setting of collation (collation font collation) can be intentional by the database designer or by default setting of MySql. In the case of a union, we must ensure that the select value in each field must have the corresponding code type defined. In my opinion, this error is quite common, especially for CMSs running Apache MySql. People can learn more at: http://bugs.mysql.com/bug.php?id=57926.
In this case we can use conversions to the appropriate encoding.
For example in the following case:

In the above query, if column1 has been set to collation as Unicode-UTF8 or _latin1 for example, then what is selected from column2 will have to be converted to the corresponding code. We can force it like this:

Do we see the downside in this bypass that we have to know that the collation code is _latin1. A better way to bypass is to use hex and unhex encoding and decoding functions.

There are many other functions that can be used in place of hex and unhex.
You should read it
- ★ Web6: SQL Injection - Some Exploit Tools
- ★ Web4: SQL injection - Exploitation steps
- ★ Learn about SQL Injection and how to prevent it
- ★ What is Fault Injection Attack (FIA)? Is it worrisome?
- ★ WordPress plugins with more than 300,000 pages that use vulnerabilities are vulnerable to SQL Injection attacks