How to protect your computer from Thunderspy attack
Thunderbolt is a hardware brand interface developed by Intel that acts as an interface between computers and external devices. Many companies now use Thunderbolt to connect to a variety of devices, but according to research at Eindhoven University of Technology, the security behind Thunderbolt can be broken using a technique - Thunderspy.
This technique implements an attack by silently allowing an attacker to access the direct memory access (DMA) function to endanger devices. The danger of this attack is to leave no trace nor execute any malware. It can bypass the best security check and lock the victim's computer. So even if the computer has security features like Secure Boot, a strong BIOS and operating system account password and activates encryption of the entire hard disk, Thunderspy will still ignore everything.
Several ways to protect your computer from Thunderspy
1. Secured-core PC protections
Microsoft's Windows Security provides Windows Defender System Guard and virtualization-based security. However, you need a device that uses Secured-core PCs. This technology uses native hardware security in modern CPUs to boot the system into a trusted state. It helps to reduce the execution of malware attacks at the firmware level.
Therefore, you should not disable the system default Windows Security program to be able to maintain the protection.
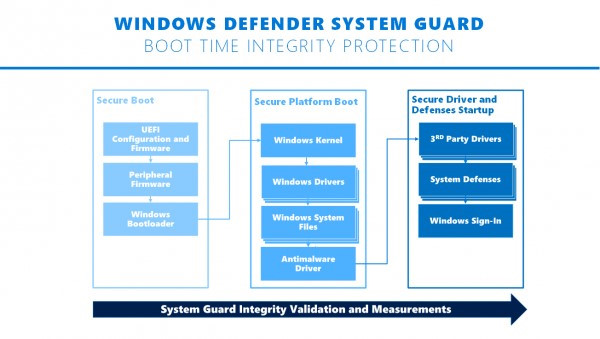
Windows Defender System Guard feature of Windows Security
2. Kernel DMA protection
Introduced in Windows 10 version 1803, the Kernel DMA protection helps prevent foreign devices from Direct Memory Access (DMA) attacks with PCI plug-in devices like Thunderbolt.
That means that if someone tries to copy malicious Thunderbolt software to the machine, it will be blocked at the Thunderbolt port. However, this feature is not effective when hackers have Windows login account and password.
Share by
Micah Soto
Update 16 May 2020
You should read it
- ★ Discovered a group of hackers who use secret code to spy on 21 countries
- ★ Warning: Dangerous new malicious code spills over to Vietnam
- ★ Watch out for new dangerous viruses similar to WannaCry
- ★ 100 hackers were arrested for the super-dangerous BlackShades malicious code
- ★ New weapons against malicious code are 'cloud' computing.