ZIP bomb can protect websites from hackers
Website owners can now use a tool called ZIP bomb to damage the port scanner, hacker website vulnerability and prevent him from accessing his website.
The term ZIP bomb relates to nested ZIP files that, when decompressed into large files, cannot be processed by the victim's computer or stored on the drive.
For example, a 4.5 petabyte file contains only zeros (0), which can be easily compressed to 42 kilobytes, because the ZIP compression system can handle iterative data extremely well.
ZIP bomb has been used in the past to prevent antivirus software
ZIP bombs have been used for decades to prevent antivirus software, preventing them from scanning ZIP files by extracting files and viewing content inside.
Although anti-virus software is improved against ZIP bombs, many other software does not yet have this capability, one of which is web browsers or vulnerability scanners like Nikto, SQLMap, etc.
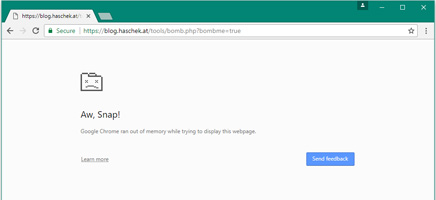
Technology expert Christian Haschek of Austria has put two PHP scripts to scan user-agent strings (the identification string when a browser sends a request to a web server) and sends ZIP bombs to vulnerability or browser scanners. The web tries to access private, protected sites (such as admin pages, backends, or pages with login forms).
These scripts will replace normal pages that hackers expect by ZIP bomb. Once their computers receive ZIP bombs, they will try to process the data and as a result their software will fail.
Most browsers and scanners crash (crash)
Below is the table given by Haschek for details about how the client will react if it encounters a ZIP bomb:
Client Results IE 11 Memory usage increases, IE Chrome errors Memory usage increases, displays error messages Edge Memory usage increases, loads very slowly and then loads forever Nikto Seems to still scan well but no return results about SQLmap Increasing memory usage until Safari fails Memory usage increases, errors, reloads, memory usage increases, then errors, . Chrome (Android) Memory usage increases, displays error messageTwo PHP file templates are needed to set up ZIP bomb for existing vulnerability scanners on Haschek's blog. This is a demo that you can access in your browser, but be careful because it can cause a computer error and lose the current browsing session. See the demo at: https://blog.haschek.at/tools/bomb.php
You should read it
- ★ How to Password Protect a Website
- ★ Anonymous attacked and distributed malicious code on the ISIS website
- ★ What to do when detecting hackers attack websites?
- ★ Many websites were hacked, changing content into gambling advertisements
- ★ Anyone can create a small and simple website with these 10 websites