Manage spam from practical experience
QuanTriMang - The daily activity of a message manager includes many tasks, such as mailbox and sender management, backup management, virus removal, recovery error backup and 'health' monitoring. for mailbox. If all of these tasks are not done, hacker spamming emails can make things worse.
In many companies, the management of spam prevention and isolation is very important. Some companies even set aside an employee to manage spam-related tasks. In businesses without or with little anti-spam technology, it is estimated that their employees will have to spend about 45 minutes a day to delete unwanted emails. One of the common topics in Internet conferences and discussions is spam prevention.
There are many methods and products that help users remove spam from the mailbox. When looking for a suitable method, businesses have many options, including:
- Use software on the client
- Use the software on the mail server or the tool that has been integrated with the mail server's antivirus software.
- Deploy an anti-spam gateway, which operates around the enterprise network
- Arrange for a third party to perform message checking (anti-spam and anti-virus) before the message is forwarded to the enterprise's mail server.
In this article, we will provide information about finding the right anti-spam solution to suit the business needs of the business, for example, the experience of a typical company.
The seriousness of the problem
Company X is a small consulting company, Microsoft Exchange Server 2003 supports their 18 mailboxes. Email is the lifeline of this company. It is estimated that about 25% of their employees use Windows Mobile, Microsoft Office Outlook Web Access devices that are used daily and email from customers to come every day of the transaction.
For a few years, Company X did not set aside a professional IT staff to manage email and ignored the problem of increasing spam every day. Members of the company often install and configure anti-spam solutions on the computer according to their preferences. A company employee reported that every 24 hours, he received 750 junk messages.
Everyone knows this problem is not good, but how bad is it? When the company upgraded its server to Exchange Server 2003 Service Pack 2, they used the built-in Intelligent Message Filter (IMF), IMF system counter and SMTP system counter to determine the severity. of spam problems. They set the IMF gateway threshold at the spam confidence level (SCL) level 5 - the spam level of an email - and configured it to receive email. Within 24 hours, the monitoring system records the IMF parameters as shown in Figure 1.
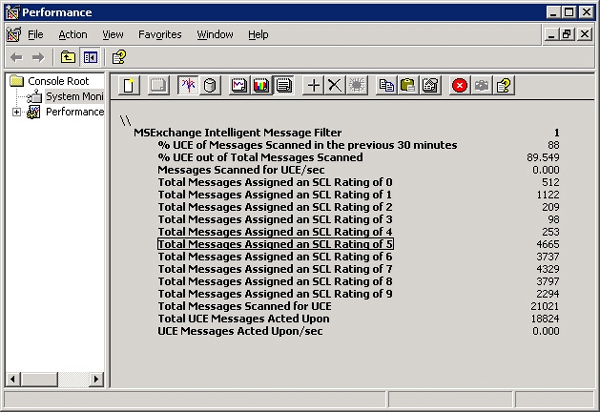
Figure 1. System monitoring parameters within 24 hours of IMF
Within 24 hours, this email server accepts 21,021 messages; Among them, 89.5% (18,824) have SCL 5 or higher. These messages consume about 35MB of hard drive space and about 40MB of Internet bandwidth needed to receive them. This is really an amazing amount of spam emails for a small company.
Some of the original methods were used to fight spam, including real-time blocking lists (RBLs) and recipient filtering.
Within 5 days of testing, the Transport Filter Sink parameter monitored the effectiveness of the RBL provided and how many messages were rejected due to sending the wrong recipient. Figure 2 shows the Transport Filter Sink parameter, of about 211,000 blocked DNS queries, 111,000 connections were rejected because the sender's IP address is one of the blocked DNS lists.
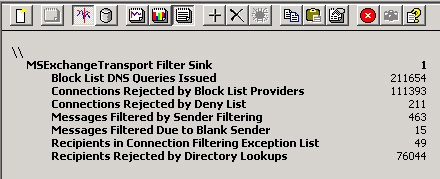
Figure 2. SMTP message transmission parameter
In addition, there are 76,000 messages rejected by recipient filtering because the recipient of the message is not valid in the Active Directory service. Obviously, someone is trying to send a large amount of inbound messages to an invalid recipient. See Exchange SMTP Virtual Server Session Current Sessions (in Figure 3) showing dozens of SMTP inbound sessions at a given time.
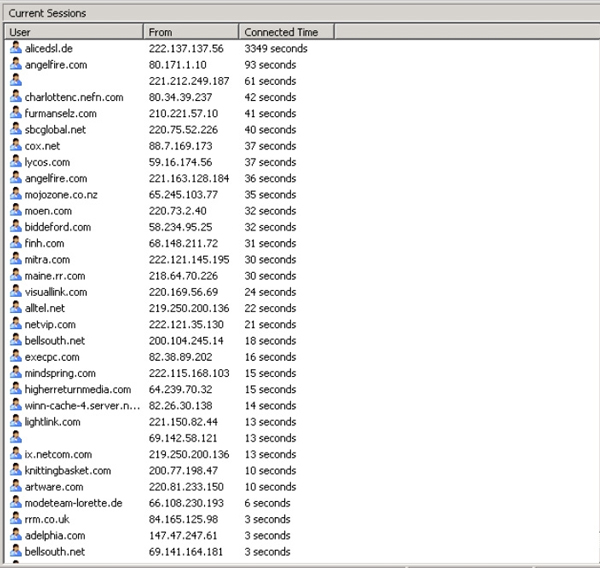
Figure 3. Inbound SMTP sessions
The SMTP protocol log is displayed and it determines almost all of these SMTP sessions that have been sent to the invalid recipient. This type of spam is called ' dictionary spamming ' because the spammer software uses a dictionary of popular names to send. The same record is also shown below:
21:15:14 212.183.55.210 telekom.at EHLO - + telekom.at 250
21:15:15 212.183.55.210 telekom.at MAIL - + From: +
21:15:53 212.183.55.210 telekom.at RCPT - + To:
21:16:08 212.183.55.210 telekom.at RCPT - + To:
21:16:24 212.183.55.210 telekom.at RCPT - + To:
21:16:39 212.183.55.210 telekom.at RCPT - + To:
21:16:54 212.183.55.210 telekom.at RCPT - + To:
21:17:10 212.183.55.210 telekom.at RCPT - + To:
21:17:25 212.183.55.210 telekom.at RCPT - + To:
21:17:39 212.183.55.210 telekom.at RCPT - + To:
21:17:55 212.183.55.210 telekom.at RCPT - + To:
21:18:12 212.183.55.210 telekom.at RCPT - + To:
21:18:27 212.183.55.210 telekom.at RCPT - + To:
21:18:41 212.183.55.210 telekom.at RCPT - + To:
21:18:57 212.183.55.210 telekom.at RCPT - + To:
21:19:12 212.183.55.210 telekom.at RCPT - + To:
21:19:27 212.183.55.210 telekom.at RCPT - + To:
21:19:42 212.183.55.210 telekom.at RCPT - + To:
21:19:57 212.183.55.210 telekom.at RCPT - + To:
Of the nearly 1,000 email sending purposes mentioned in this log file, there is only one valid user. This user may be an indexed case and it is also the way the spammer finds out the domain of this company.
Despite the initial protection methods such as using real-time block list, SMTP tar pit feature (adding delay to SMTP communication links with spam) and Intelligent Message Filter can help reduce significantly the amount of spam users receive, but in fact, such types of spam still find ways to infiltrate the Exchange server. Spam continues to consume the source of the server, the network and the users themselves.
Evaluate solutions
When Company X evaluated the solutions, they had some criteria to choose the solution. These criteria include:
- Reduce the amount of spam that needs to be handled by the Exchange server.
- Reduce the amount of spam that attacks users' mailboxes so that it does not synchronize with Windows Mobile devices, download to mailboxes of remote users and not cause Out Of Office message errors.
- Use solutions that are often updated to detect the latest spam techniques as well as day-zero viruses.
- Protect Exchange server so that it is not directly exposed on the Internet
- Make sure that the solution can change and receive errors so that emails are not lost during the inspection and distribution process.
- Reduce the amount of bandwidth and system resources that spam is consuming.
- Requires little management effort since Company X has no dedicated person to manage this issue.
Company X evaluated SMTP-based solutions as well as management solutions from third-party vendors. Finally, they chose solutions from vendors. Company X redirected public DNS MX records to that provider's data center. This provider is responsible for providing 'cleaning' messages, such as anti-spam, anti-virus. They will then forward the message to company X's Exchange server.