Secure WiFi in enterprise environment from basic steps
Wifi is an entry-point (an entry point) that hackers can use to infiltrate your network without stepping into your company's headquarters, because wireless networks are more vulnerable to eavesdropping than wired networks. This makes network administrators more diligent in the security of Wifi networks.
Although Wi-Fi is vulnerable to eavesdropping and eavesdropping, it can still be secured if you take the time to invest in learning and applying advanced network security measures. So, follow what should and should not be done to make your home wireless network safer. If you are looking for a wifi security solution in an enterprise environment, this article will also meet that demand.
- Top 10 basic network troubleshooting tools that IT people need to know
- Comprehensive network monitoring tool set
Using discreet SSID, should not trust hidden SSID
The SSID (Service set identifier) is one of the most basic Wifi network settings. Using careless SSID can harm the safety of Wifi network. Using common SSID names such as "wireless" or the default name from the provider can make an attacker easily unlock personal mode of WPA or WPA2 security. This is because the encryption algorithm combines with the SSID, and hackers use password-breaking dictionaries with common, common SSID names. Therefore, using the default or too common SSID name will make hacker "work" easier. (However, this vulnerability cannot be exploited on networks using the Enterprise mode of WPA, WPA2 security, one of the many benefits of the Enterprise mode).

Name the SSID normally but don't be too common, don't involve the company
Although it is possible to set the SSID according to an easy-to-remember criteria such as company name, address, room number, this is not a good idea, especially if your company is in the same building with many other companies. or near other buildings and networks. Because when hackers get close to the building, they can quickly target a network with the most easily identifiable identities and also help them guess what they will have when hacking into this network.
One of the rumors about wireless security is that disabling the SSID transmission of access points will help hide your network or at least create a safe SSID that makes it hard for hackers to break. However, this only helps to remove SSID from access point. It is still included in the 802.11 request and in some cases it is also included in network requests and response packets. Therefore, a hacker or eavesdropper can easily and quickly discover hidden SSIDs - especially in busy networks - with legitimate wireless network analysis.
Some people argue that shutting down SSID transmission still provides more security layer for the network, but keep in mind that it has the potential to cause a negative effect on network configuration and performance. You will have to manually enter the SSID into the device, followed by the device configuration. It may also cause increased probe requests and return packets, reducing the amount of available bandwidth.
Don't forget physical security
Even if you have the best encryption method in hand, it can still exist holes. Physical safety is one such hole. Most access points (Access point or AP, hereinafter referred to as AP) have a reset button to restore the default settings, delete Wifi security and allow anyone to connect to the network. Therefore, APs that are distributed throughout your company should also be protected (physically, like putting in locked boxes) to prevent crooks. Make sure only those involved can touch them, considering using the AP vendor's built-in locking mechanisms to restrict access to buttons and ports on the AP.
Another physical security concern with Wifi is when someone adds an unauthorized AP to the network, also known as a "rogue AP" - fake AP. This can be done rightfully, such as expanding wireless coverage or for bad purposes of employees (or even outsiders) who want to access the network. To prevent these fake APs, make sure all unused ethernet ports (wall-mounted or standby ports) are disabled. You can remove ports, network cables or short connections to that power or network cable on the router or switch. If you want to increase security, turn on 802.1X authentication on the wired plug (if the router or switch supports that), then any device plugged into an ethernet port must enter the login credentials to Network Access.
Do not use WEP, WPA / WPA2-PSK
Wired equivalent privacy has long been dead. Its encryption capabilities can be easily and quickly broken by most amateur hackers. Therefore, you should not use WEP at all. If you're using it, upgrade immediately to WPA2 (Wi-Fi protected access) with 802.1X authentication. If new to a wifi router or access point does not support WPA2, try updating the firmware or simply changing the new device.
- Unlock WEP Wifi password with Backtrack

Pre-shared key (PSK) mode of WPA and WPA2 is not very secure to the enterprise environment. When using this mode, it is necessary to enter the PSK key for each wifi transmitter. Therefore, this key needs to be changed every time an employee leaves the company and when a transmitter is lost or stolen - things are still not really focused on most business environments.
Using Enterprise WPA2 with 802.11X authentication
One of the most beneficial Wifi security mechanisms that you can deploy is the enterprise Wi-Fi security mode, because it authenticates each individual user: People can have a Wifi username and password. private. Therefore, if the laptop or mobile device is lost, stolen or the employee leaves the company, you can change or cancel the login of those specific devices / users.
(In contrast, in personal security mode, all users share the same Wifi password, so when the device is lost or employees leave, you'll have to change the password on every device - one The work is not simple).
Another great advantage of the Enterprise mode is that each user is assigned their own encryption key. That means that users can only decrypt their own data traffic without being able to snoop on anyone else's wireless traffic.
To set APs in Enterprise mode, you first need to set up a RADIUS server. This server allows users to authenticate and connect to (or save) a database or directory (such as Active Directory) containing everyone's name and password.
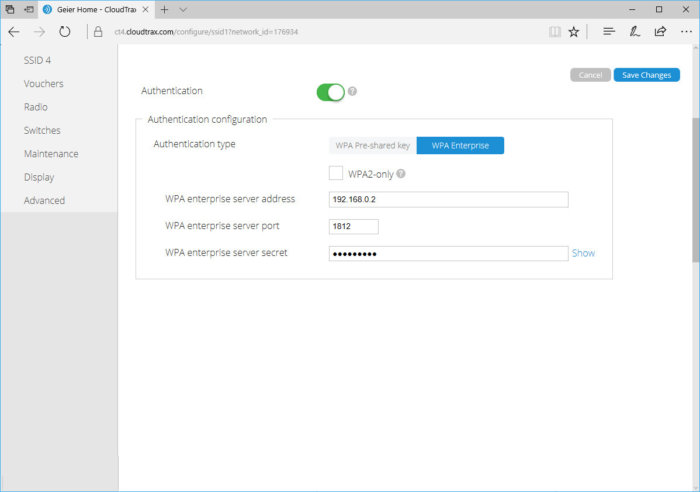
Example of how to configure AP with IP, RADIUS server and secret port
You can deploy a standalone RADIUS server if your other servers (like Windows Server) provide this feature. If not, consider using RADIUS services on the cloud, or stored on a third-party server. Some wireless APs or drivers have a built-in basic RADIUS server, but the performance and features of this type of server are limited, making them only suitable for small networks.
- WiFi - 802.11b, 802.11a, 802.11g, 802.11n and 802.11ac standards
Secure 802.1X settings on the client
Like other security technologies, Enterprise mode still has security holes. One of these is man-in-the-middle attacks, with semi-skilled hackers. They can set up fake Wi-Fi networks with the same SSID or similar networks that they are trying to tamper with, when your laptop or device connects to this fake network, the fake RADIUS server will record the credentials. log in. After that, the hacker can use that login credential to connect to the real Wifi network.
One way to prevent attacks with 802.1X authentication is to use server authentication on the client. When server authentication is enabled on the client, the client will not transfer your Wifi login credentials to the RADIUS server until it confirms that it is connecting to the correct legitimate server. The ability and exact server authentication requirements that you can set up for clients will depend on the device or operating system on which the client is running.
For example, in Windows, you can enter the domain name of the legitimate server, select the server certificate issuer, and enable the option to not allow any new servers or new certificate issuers. So, even if the bad guys have set up a Wifi network and a fake RADIUS server, you are trying to log on to a fake network that Windows will also prevent you from connecting.
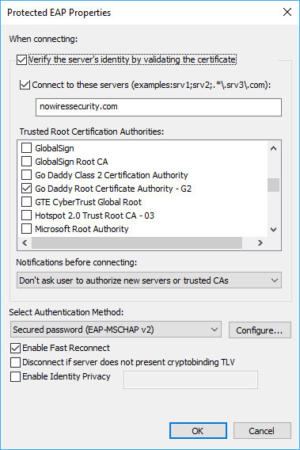
802.1X server authentication feature on Windows when setting EAP settings of Wifi connection
It is recommended to use an unauthorized intrusion prevention system on the wireless network, detecting fake AP
At this point, we have mentioned two of the 3 unauthorized intrusion scenarios on the wireless network: One is an attacker who establishes a Wi-Fi network and a fake RADIUS server and the other is to reset the AP to the default settings. . And the third scenario is that someone can plug their own AP into the network.
These unauthorized APs can last for a long time without IT staff knowing without proper protection. Therefore, you should turn on all the phishing detection features provided by the AP or your wireless controller. Their detection methods and functions may not be the same, but at least, most of them will scan radio waves periodically and send you warnings if new APs are detected within the scope of legitimate APs.
To enhance detection, some AP vendors also have built-in wireless detection systems (WIDS) or intrusion protection systems (WIPS). They can sense attacks on the wireless network as well as suspicious activities from fake APs such as erroneous de-authentication requests, requesting false links (mis- association request) and fake MAC address.
Furthermore, WIPS provides more protection than WIDS (only detected), even WIPS can automatically perform some countermeasures such as disconnecting, blocking suspicious clients to protect the network. being attacked.
If your AP does not have fake AP detection or proper WIPS integration, consider a third-party solution. Some companies such as 7SIGNAL, Cape Networks and NetBeez provide sensor-based solutions that can monitor both Wifi performance and security issues.
NAP or NAC should be implemented
In addition to using 802.11i and WIPS, you should consider deploying the Network Access Protection (NAP) or Network Access Control (NAC). They will provide additional network access management capabilities, based on device identification with predefined policies. They also include a function to isolate problematic and repaired devices so that the device can quickly return to work.
Some NAC solutions are capable of including intrusion detection and prevention, but you will have to check if it provides specialized wireless protection .
If you are running Windows Server 2008 or later and Windows Vista / 7 for the device, you can use Microsoft's NAP function. If not, look for solutions provided by third parties, such as PacketFence.
Do not trust MAC address filtering
Another rumor about wireless security is to enable MAC address filtering to help gain a more secure layer, managing applications connected to the network. This is a bit accurate, but remember that hackers can easily monitor your network to get legitimate MAC addresses, then they will change the Mac address for their machines.
Therefore, you should not deploy MAC address filtering thinking that they will help your security, but can be a way to manage end-user devices and computers brought to the company and connected. connected to the network. You should also pay attention to potential management issues to keep the MAC list up to date.
Should restrict users who can connect to SSID
Many network administrators overlook a seemingly simple but highly dangerous risk: users are aware or unaware of connecting to a neighbor's wireless network or access point. unclear, opening up opportunities for hackers to hack into machines. However, filtering SSID is a way to prevent this. For example, in Windows Vista (or higher versions), you can use the netsh wlan command to add filters to SSID users who want to see and connect. For desktop computers, you can deny all SSIDs except the corporate network. For laptops, IT staff can only deny neighbors' SSIDs, allowing them to remain connected to the access point or home network.
Don't forget to protect mobile devices
The concerns about wireless network security are not just here. Users with smartphones, laptops and tablets can be protected on the spot. However, when they connect to free Wi-Fi hotspots or connect to a wireless home router? You should ensure that other Wi-Fi network connections are also secured to prevent unauthorized intrusion or eavesdropping by hackers.
Still, it's not easy to make sure that external Wi-Fi connections are always secure. You will have to combine the provision, require the use of solutions and educate users about security risks along with prevention methods.
First of all, all laptops and netbooks will have to enable personal firewalls (such as Windows Firewall) to prevent unauthorized intrusion. You can do this via Group Policy (if you're running Windows Server) or use a solution, such as Windows Intune, to manage computers that are not in the domain.
Next, you will have to make sure that the user's Internet traffic is encrypted when they are on another network by providing VPN access to the enterprise network. If you don't want to use VPN in this case, consider other services like Hotspot Shield or Witopia. For iOS devices (iPhone, iPad, iPod Touch) and Android, you can use their VPN application. However, for BlackBerry and Windows Phone 7 devices, you will have to set up and configure server messages with this device to be able to use their VPN.
In addition, you should also ensure that all network-related services are secure, in case users do not use VPN when accessing from a public network or an unreliable network. For example, if you provide email access (via the application or on the web) outside your LAN, WAN or VPN, make sure you use SSL encryption to prevent hackers from eavesdropping and stealing information. Important login or personal messages.
See more:
- Basic information about network equipment
- How to find the IP address of another computer on the LAN
- This is a way to prevent hackers from stealing your data when using public Wifi
- Use Remote Desktop to access computers in the office and home networks