IDS for Web application attacks
Don Parker
In the online world, there is always a world of web application hacking that can be viewed as a wild world. There are many new and always happening things that are not as expected. These attacks often exploit vulnerabilities in web applications or encryption techniques to bypass the network's defense. With such a continuous operating environment, we need to understand the basics of the problem. On top of that, system administrators as well as network security people must be knowledgeable about this issue. If you are an administrator and often see unusual behavior for your network, the difficulty you will feel is how to capture the entire world of web application hacking. There are many areas related to it that you should care about but here we will introduce you to a high-level area that is coding.
What is encryption?
Encryption is a process of transforming information from one format to another. Take an example that is all the words written in this article, they are presented in ASCII format. What happens if it encodes it into HEX format? The exact meaning of the words in the article is still the same but they will now be displayed in HEX format. Make an quick example in this case.

Figure 1
Now we can see in the inner window display, on the left there are some HEX values, and on the right there are some ASCII sentences that this article author wrote in it. Both indicate a content but in different formats. We can assume that there is no value in carrying this document and encoding it into another format. However, in an example that has not yet covered the problem, what would encryption really be like with real web application hacking and what would it look like? This is an interesting question, let's focus and solve this question. What to use for our example is the classic Directory Traversal error. Many of you can guess some of the words in them, what this error allows you to do is navigate to the parent folder of the website.
Analytical environment
The tools and programs that we will use to introduce some web application attacks and can detect them are:
- Snort
- Web browser
- Encoding tool
You can see that there are not many requests to successfully perform hacking detection for some web applications. You can also use additional HTTP proxies for each web browser or whatever you like. If this is done for the client, we will use the BURP HTTP proxy set. We will now start Snort so that it can review and test the packages to the computer where we already have the Apache webserver running.
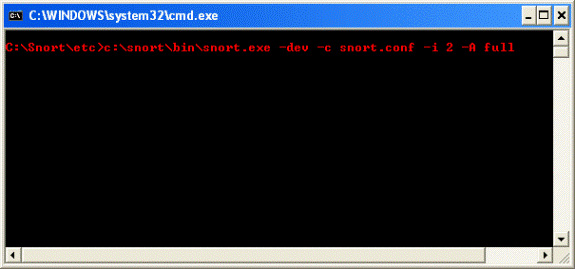
Figure 2
As you can see in the figure above, we have awakened and assigned Snort through the -i 2 switch, which is the interface that makes it possible to track. This is because we are using Snort and Apache webserver in VMware image. That means there will be more NICs for Snort. We have to point out something that Snort will check for us. Now look at the next screen with a very basic example of attacking web applications, and as mentioned earlier it is the Directory Traversal vulnerability.
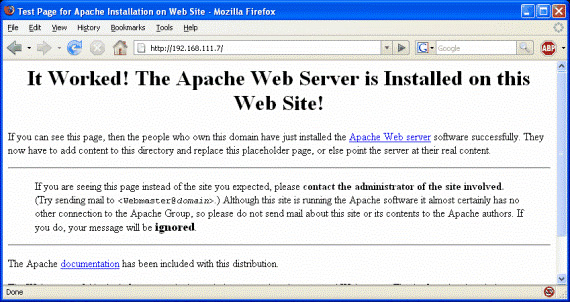
Figure 3
So the Apache webserver is awakened and running. Give the Directory Traversal input its original format and see what happens. Before you do this, make sure you have Snort running to see what happens if it detects an attack attempt.
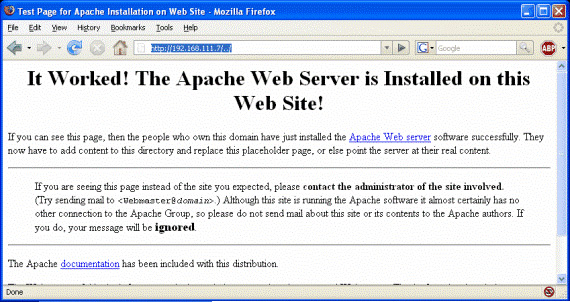
Figure 4
Let's take a look at the screen ./ is what the Directory Traversal shows us. When you send it to the Apache webserver you will find that it itself will not do anything, it seems to ignore. We will briefly review what Snort has discovered. Please encode it in another format.
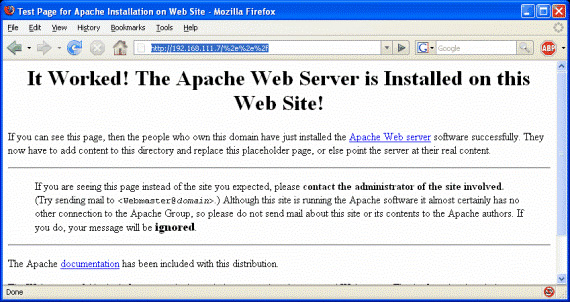
Figure 5
What we have done now is encoding ./ to the equivalent HEX environment.
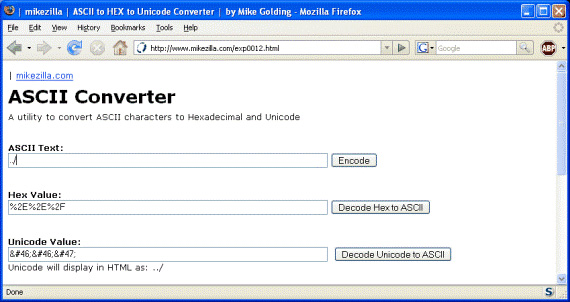
Figure 6
Now when you send the HEX encoded Directory Traversal vulnerability to the Apache web browser, you once again see nothing happening. We will check to see what Snort has seen at the back. Please try it again with UNICODE encoded version.
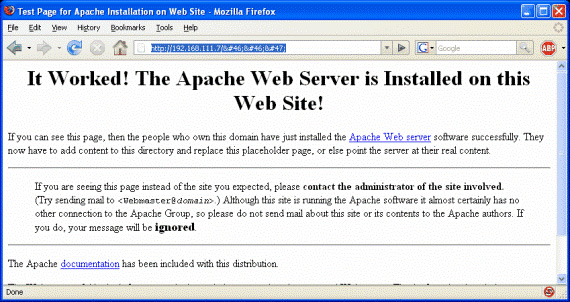
Figure 7
Enter that new version of Directory Traversal and observe what happens. You will see Apache responding to an HTTP 404 status code. That means the URL is not found on the server. So we have to try all three different versions of Directory Traversal and none of them work. Check what Snort announced.
C: Snortetclog> more alert.ids
[**] [119: 18: 1] (http_inspect) WEBROOT DIRECTORY TRAVERSAL [**]
05 / 31-10: 18: 51.262616 0: 17: 31: 8A: 93: 7F -> 0: C: 29: BA: DC: 9E type: 0x800 len: 0x1F4
192.168.111.2:2780 -> 192.168.111.7:80 TCP TTL: 128 TOS: 0x0 ID: 16806 IpLen: 20 Dgm
Wool: 486 DF
*** AP *** Seq: 0x805DCAAC Ack: 0xF13CBB87 Win: 0xFFFF TcpLen: 20
C: Snortetclog>
No problem with Snort
With the sign WEBROOT DIRECTORY TRAVERSAL showing us that this old web application hack was detected by Snort. This has been done without the need to encrypt the original ./ attack in many different formats. Now let us mention the Directory Traversal attack. There is little possibility that this will be avoided for all modern IDS. That means that the world of web application hacking is a huge world. There are many other types of hacks that can threaten us.
The problem when it comes to attacking web applications is that many of these applications are not properly tested or even ignore code validation. Thus they can contain a lot of vulnerabilities for countless attacks. One of the easiest ways to increase your knowledge of web application hacks is to try to replicate them yourself. Nothing helps someone better understand by doing it yourself. Once you've brought yourself, then you might want to do something when IDS is checking traffic. This will give you the idea of developing IDS markers for SQL injection threats or whatever attack you are re-creating. Signs will often not be clear or do not exist, you will want to write yourself, as long as your IDS solution allows. That will give you a quick overview of how to attack web applications and hopefully it will stir your inner search.