Excel continues to be used as a lure for online fraud with complex mechanisms
This attack was developed by the TA505 hacker group (also known as Evil Corp or SectorJo4) specializing in malicious financial campaigns. This group of hackers is no stranger to global cybersecurity organizations after successful campaigns targeting large retail and financial institutions, using the Necurs botnet, causing millions of dollars in damage. . The group is currently working on another campaign using the Excel tool to lure 'gullible' people.
According to findings from Microsoft Security Intelligence, TA505's new offensive campaign will send victims attachments with HTML redirection using malicious Excel documents. Through these malicious documents, the hacker attached a remote access trojan (RAT), as well as a malware downloader that distributes Dridex and Trick malware to the victim's system, targeting the data. Data, financial accounts on the system.
More dangerous, malicious Excel documents distributed by TA505 not only contain Trojans, but also attach malicious ransomware such as Locky, BitPaymer, Philadelphia, GlobeImposter, Jaff.
'TA505's new offensive campaign uses HTML redirects attached to emails. When opened, HTML led to download Dudear, an Excel file containing malicious macros into the victim's system '.
So when opening an HTML attachment, the victim will automatically download the malicious Excel file, and this is what they encountered:
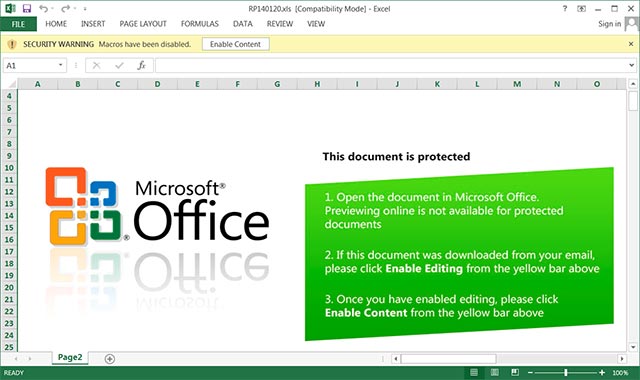
After the victim clicked on Enable Editing and Enable Content as instructed in the document, they accidentally released the malware onto their system.
This malware includes GraceWire - a Trojan designed to steal information, collect sensitive information and forward data obtained via a command and control server (C2 Server).
Until this malicious campaign is stopped, the most effective preventive measure will still be refusing to open strange emails, downloading attachments as well as accessing unauthenticated links.
You should read it
- ★ 25% of 'over-the-counter' phishing emails are the default security of Office 365
- ★ [Infographic] How to recognize and prevent Phishing attacks
- ★ The 4 most popular network attacks towards older people in 2018
- ★ Hacker purged two-factor security just by automated phishing attacks
- ★ GitHub is under strong phishing attack, users pay attention to account security