How to Hide Evidence on a Computer
Method 1 of 5:
Windows
-
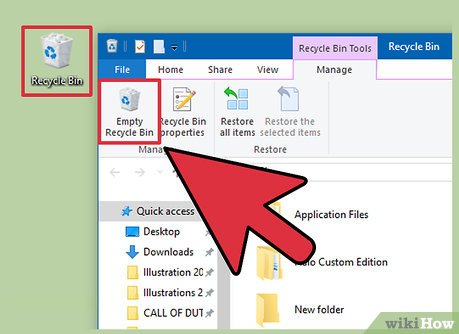
 For Windows users, if you have a folder, put it in the recycle bin and empty the recycle bin.
For Windows users, if you have a folder, put it in the recycle bin and empty the recycle bin. -
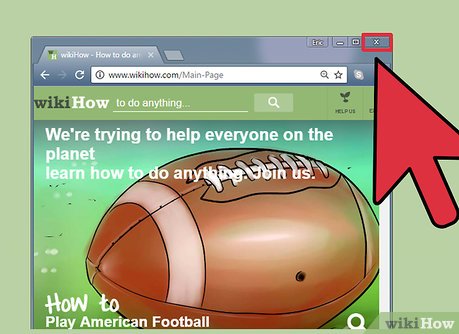
 If you have a browser open (Mozilla Firefox, Internet Explorer, Google Chrome), close it.
If you have a browser open (Mozilla Firefox, Internet Explorer, Google Chrome), close it. -
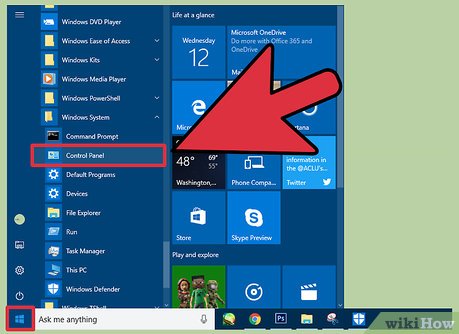
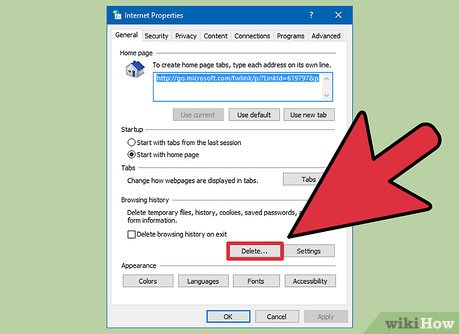
 Click Start, then click Control panel.
Click Start, then click Control panel. -
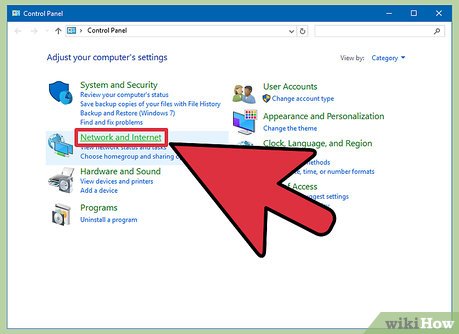
 Click Network and Internet then go to Internet options.
Click Network and Internet then go to Internet options. -
 Click "Delete" to clear up cookies and internet history. If you have a different version, then just click delete all.
Click "Delete" to clear up cookies and internet history. If you have a different version, then just click delete all.- Note: Emptying the recycle bin will not completely erase the file from your system. Its still possible to recover the file. Use a file shredder to completely overwrite the file and make sure that no one is able to retrieve it.
- If you need to destroy all the information on a computer in an emergency, your best bet is to use Darik's Boot and Nuke. This will wipe a hard drive and over write the data to get rid of all possible ways of recovering data.
Method 2 of 5:
Alternative Windows
-
 Use the program CCleaner (freeware) from Piriform Ltd. It removes files like windows logs, temporary folder data, old prefetch data. Not even Bill Gates himself will recover anything. Set the secure erasing to Gutmann, in the preferences page.
Use the program CCleaner (freeware) from Piriform Ltd. It removes files like windows logs, temporary folder data, old prefetch data. Not even Bill Gates himself will recover anything. Set the secure erasing to Gutmann, in the preferences page.
Method 3 of 5:
Mac OS
-
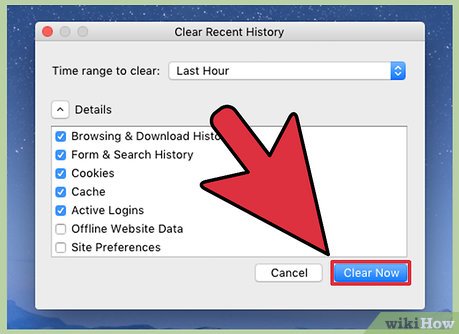
 For Macs, if you use Mozilla Firefox open it up.
For Macs, if you use Mozilla Firefox open it up. -
 Click Clear Private Data
Click Clear Private Data -
 Click Clear All.
Click Clear All. -
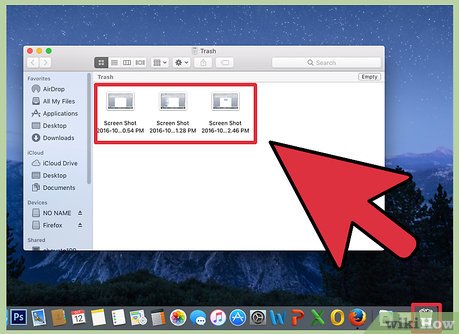
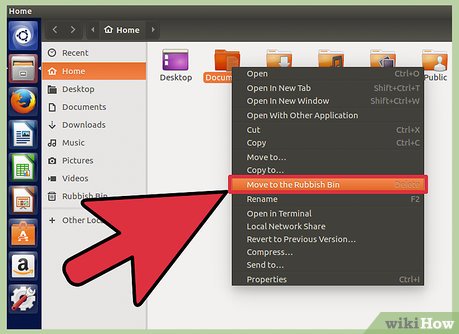
 If you have files and folders put them in the trash.
If you have files and folders put them in the trash. -
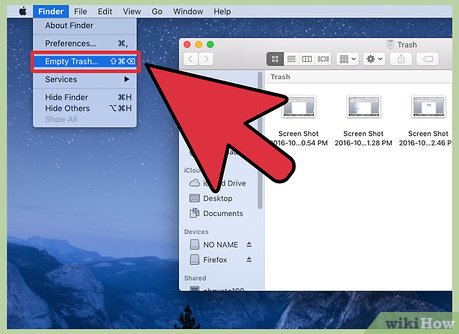
 Empty the trash by clicking finder and emptying trash.
Empty the trash by clicking finder and emptying trash. -
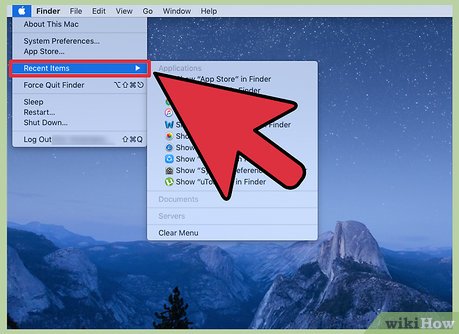
 Click the apple icon and go to recent items.
Click the apple icon and go to recent items. -
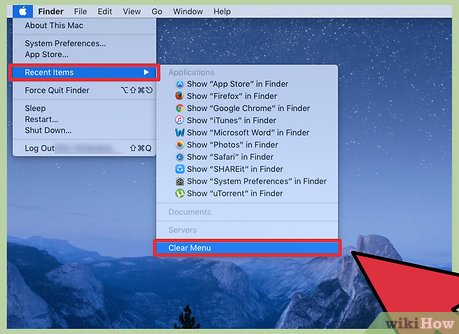
 Click clear all.
Click clear all. -
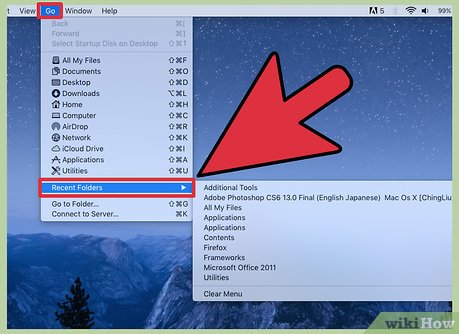
 Go to recent folders by clicking on the go tab.
Go to recent folders by clicking on the go tab. -
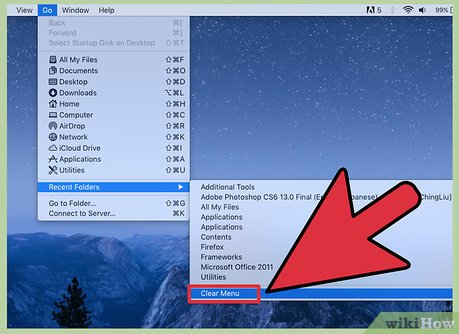
 Clear the recent folders.
Clear the recent folders. -
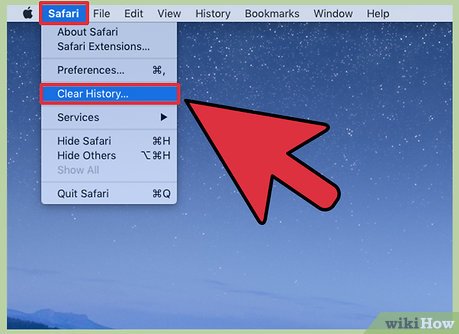
 For Safari users, go to Safari--> Reset Safari--> check all that apply. This operation cannot be undone.
For Safari users, go to Safari--> Reset Safari--> check all that apply. This operation cannot be undone.
Method 4 of 5:
Alternative Mac OS
-
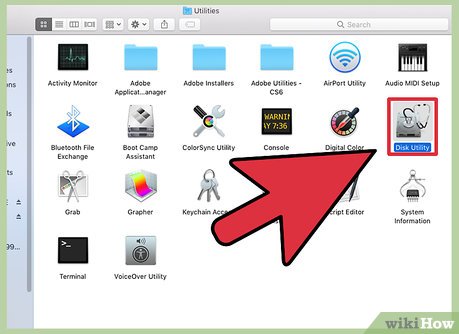
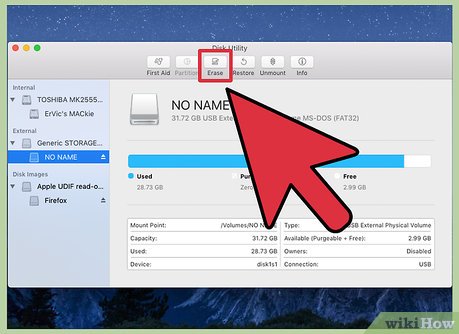
 Go to disk utility, choose the OS and click the erase tab.
Go to disk utility, choose the OS and click the erase tab. -
 Click Erase Free Space.
Click Erase Free Space. -
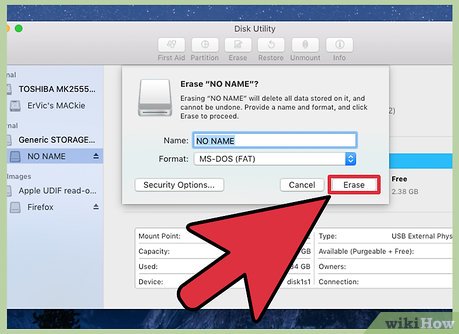
 Click Either 7-Pass Erase of Deleted Files or 35-Pass Erase of Deleted Files.
Click Either 7-Pass Erase of Deleted Files or 35-Pass Erase of Deleted Files.- This means that your computer will erase all the free space and overwrite the date by adding 0's seven or 35 times making deleted files unrecoverable. 7 times is considered DOD (5220.22-M) sufficient and 35 times is considered impossible whatsoever. (Gutmann method). If the government seized your computer, and you used the Gutmann method before it was seized, given the time and proper equipment(which costs thousands of dollars), they would only be able to recover bits and pieces of the data but not the whole data itself. This includes CIA, FBI, National Security and other government agency that cannot fully restore the data.
Method 5 of 5:
Linux
-
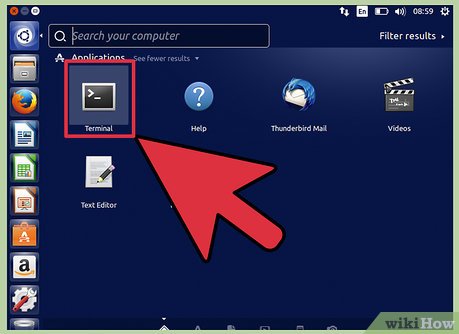
 Open console and type shred file_to_delete. Shred will overwrite the file content many times, making it near impossible to recover even by the most experienced hackers.
Open console and type shred file_to_delete. Shred will overwrite the file content many times, making it near impossible to recover even by the most experienced hackers. -
 shred also works with hard drives (shred /dev/hdc, for instance). Shredding the hard drive is a long task, so be sure you have enough time. Also, be sure you are shredding the correct drive and partition.
shred also works with hard drives (shred /dev/hdc, for instance). Shredding the hard drive is a long task, so be sure you have enough time. Also, be sure you are shredding the correct drive and partition. -
 Never use any "user friendly" tool like file manager to delete the secret information. Files, deleted with such programs, can usually be easily recovered by the specialist even after a long time.
Never use any "user friendly" tool like file manager to delete the secret information. Files, deleted with such programs, can usually be easily recovered by the specialist even after a long time.
Share by
Samuel Daniel
Update 24 March 2020