How to access TPM Diagnostics tool to query security data on Windows 11
At the launch of Windows 11, Microsoft announced that the operating system would only support computers with the TPM 2.0 security chip. According to Microsoft, TMP 2.0 is a key component to providing security with Windows Hello and BitLoker. This helps Windows 11 better protect users' identities and data.
In order to help users and administrators easily control the data stored on TPM, Microsoft has added a tool called TPM Diagnostics. This is an additional tool, so to use it, you need to install it first.
To install and use TPM Diagnostics on Windows 11 follow these instructions:
Step 1: Press Windows + I to open Settings then access Apps in the left sidebar
Step 2: Click Optional features

Step 3: Click View features at Add an optional feature

Step 4: Enter tpm in the search box then click next to the TPM Diagnostics tool shown below and then click Next > Install to confirm the installation

Step 5: After waiting for the system to finish installing, you can use TPM Diagnostics through the Windows Terminal (Admin) command window (the new name of Command Prompt)
Step 6: You press Windows + X to open the Power User menu then select Windows Terminal (Admin)
Here you can enter TPM Diagnostics control commands. For example, the TpmDiagnostics.exe GetCapabilities command will list the capabilities and settings of the TPM chip on your machine as shown below:
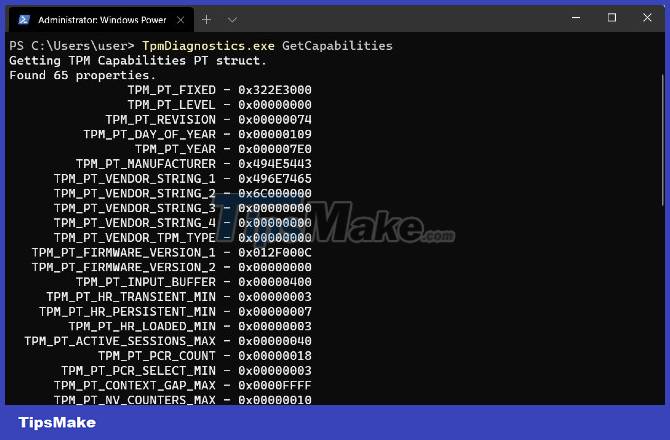
In addition to querying stored security keys and other information, you can also use TPM Diagnostics to encrypt/decrypt Base64, Hexadecimal, and Binary files.
With TPM Diagnostics, you can learn a lot of information about Windows 11's basic security mechanisms. However, we recommend that you don't "play around" too much on this TPM Diagnostics tool if you don't know it. clear about it. If misconfigured you may lose the keys necessary for the operations on your machine.
Here is a list of all the commands available in the TPM Diagnostics tool:
Flags: PrintHelp ( /h -h ) PromptOnExit ( -x /x ) UseECC ( -ecc /ecc ) UseAes256 ( -aes256 /aes256 ) QuietPrint ( -q /q ) PrintVerbosely ( -v /v ) Use the 'help' command to get more information about a command. Commands: TPmInfo: GetLockoutInfo IsOwned PlatformType CheckFIPS ReadClock GetDeviceInformation IfxRsaKeygenVulnerability GatherLogs [full directory path] PssPadding IsReadyInformation TPMTask: MaintenanceTaskStatus ShowTaskStatus IsEULAAccepted ProvisionTpm [force clear] [allow PPI prompt] TPmProvisioning: PrepareTPM CanUseLockoutPolicyClear CanClearByPolicy AutoProvisioning: IsAutoProvisioningEnabled EnableAutoProvisioning DisableAutoProvisioning [-o] EK: EkInfo ekchain EkCertStoreRegistry GetEkCertFromWeb [-ecc] [cert file] GetEkCertFromNVR [-ecc] [cert file] GetEkCertFromReg [-ecc] [ output file ] GetEk [-ecc] [key file] CheckEkCertState InstallEkCertFromWeb InstallEkCertFromNVR InstallEkCertThroughCoreProv EKCertificateURL WindowsAIK: InstallWindowsAIK [-skipCert] WinAikPersistedInTpm UninstallWindowsAIKCert GetWindowsAIKCert [cert file] IsWindowsAIKInstalledInNCrypt EnrollWindowsAIKCert GetWindowsAIKPlatformClaim ["fresh"] [output file] OtherKeys: PrintPublicInfo [ srk / aik / ek / handle ] [-asBcryptBlob / -RsaKeyBitsOnly / -RsaSymKeyBitsOnly] [-ecc] TestParms [ SYMCIPHER | RSA ] [ algorithm specific arguments ] EnumerateKeys NVStorage: EnumNVIndexes DefineIndex [index] [size] [attribute flags] UndefineIndex [index] ReadNVIndexPublic [index] WriteNVIndex [index] [data in hex format | -file filename] ReadNVIndex [index] NVSummary NVBootCounter: CheckBootCounter ReadBootCounter [/f] PCRs: PrintPcrs PhysicalPresence: GetPPTransition GetPPVersionInfo GetPPResponse GetPPRequest TPMCommandsAndResponses: CommandCode [hex command code] ResponseCode [hex response code] Tracing: EnableDriverTracing DisableDriverTracing FormatTrace [etl file] [output json file] DRTM: DescribeMle [MLE Binary File] Misc: Help [command name] DecodeBase64File [file to decode from base 64] EncodeToBase64File [file to encode] ReadFileAsHex [file to read] ConvertBinToHex [file to read] [file to write to] ConvertHexToBin [file to read] [file to write to] Hash [hex bytes or raw value to hash] GetCapabilities