Deploy Data Protection Manager 2007 (Part 2)
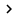 Deploy Data Protection Manager 2007 (Part 1)
Deploy Data Protection Manager 2007 (Part 1)
Anderson Patricio
In the previous section, we deployed the DPM server and before we started to learn about DPM administration interfaces, we had to configure three main points :
- Understand the location and how DPM uses media to protect data (disk, tape or both).
- Add more discs to the archive
- Add agents to the protection server
After the above three topics, we will look at each of DPM 2007's main areas.
Save backup data in disk, tape or both
One of the interesting features of DPM 2007 is the ability to save protected data in various ways such as disk-based, tape-based or a combination of both as shown in Figure 1.

Figure 1: Three methods to store data information (Disk, tape and both)
This flexibility is set at the Protection Group level. By using these methods, we can configure the short-term data cycle to be stored on a disk because when performing a restore from a disk much faster than a tape. We can also define long-term cycles for data that can be transferred to tape. All of these options are defined when creating Protection Groups to protect servers.
Add more discs to the archive
DPM uses a set of storage disks called Storage Pool, which is a place to store protected copies and restore points. We need to have at least one disk in this repository to start the server protection process.
If there is a basic disk, DPM will convert it into a dynamic disk to add to the Storage Pool repository. In DPM Beta2, we can add any physical disk and it will only use the unspecified space of the selected disk. We will add the disk as shown in Figure 2 to the DPM repository.
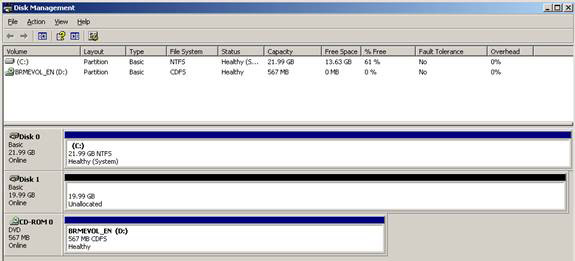
Figure 2: Disk will be added to the repository
To add a disk to the archive, follow the steps below:
1. Open Microsoft System Center Data Protection Manager .
2. In the control window, click the Management area.
3. In the Display panel, click the Disk tab
4. In the Actions panel, click Add .
5. Add Disks to Storage Pool . In the left pane, all available disks that can be used by DPM will appear here. Click on the disk and click the Add -> button as shown in Figure 3. This disk will be moved to the right frame and we can see the disk name and capacity and have data on the disk or not. Click OK .

Figure 3: Select a disk to add to the repository
6. Now we can see the newly added disk to the repository (Figure 4). We can also see the disk state, how much of a split is for protection, and how much space is still unallocated and which protection versions are used on this disk.
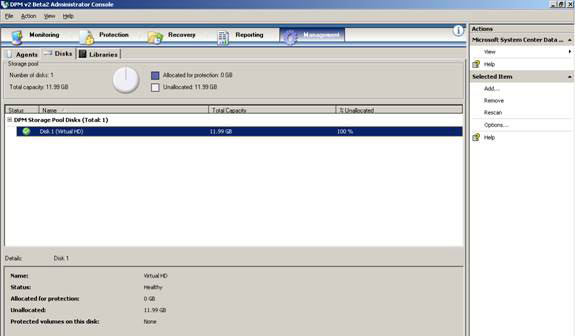
Figure 4: Disk Management with the recent initialization disk will be added to the DPM repository
Deploy DPM agents
Let's install agents on DPM protected servers. Agent installation can be done manually or via the DPM administration interface. The agent will be installed as a service called DRMA on protected servers.
1. Open Microsoft System Center Data Protection Manager .
2. In the window, select the Management area
3. In the Display panel, click the Agents tab
4. In the Actions panel, click Install .
5. Select one or more servers to install the agent as shown in Figure 5, and then click Next .

Figure 5: Select the server to install the DPM agent
6. Enter Credentials . Specify the user name and domain name and password as well as the installation rights on the server that DPM Agent will be installed, click Next .
7. Choose Restart Method . Install Agent and automatically restart the server or install agent and restart the server automatically. Click Next .
8. Summary . If the server is valid, it will receive the Agent and click Install .
9. Now, click Close , the installation status will be shown in Figure 6
Figure 6: New installed agent - valid version, status and group of the agent
Use the DPM 2007 administration interface
We can work with DPM through the administration interface or through the DPM management utility that allows PowerShell to be used.
The DPM administration interface has 5 different areas that can be managed. These areas are: Inspection, protection, restoration, reporting and management. We will go into each region specifically to see what can be done in it.
DPM 2007 administration interface
Check (Monitoring)
This area allows them to check the status of DPM operations, it is divided into 2 different tabs: Alerts and Jobs.
Alerts : This tab shows notifications about agents, backups, and recovery procedures. We can group these alerts using the Group by feature (Figure 07).
Jobs : Shows the status of jobs and tasks associated with them. We can also group jobs using the Group by feature and Filter names. The jobs listed in this area are set automatically during the process of creating a protection group (Figure 8).
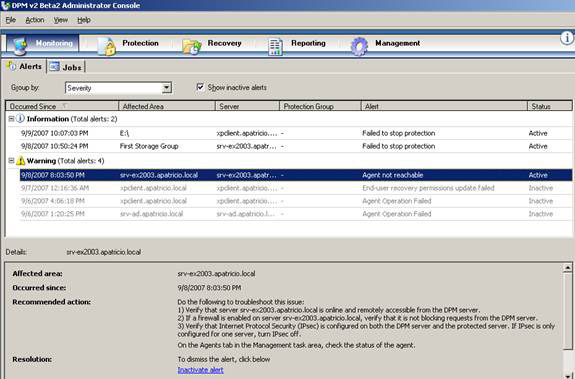
Figure 7: Active and Inactive DPM notifications
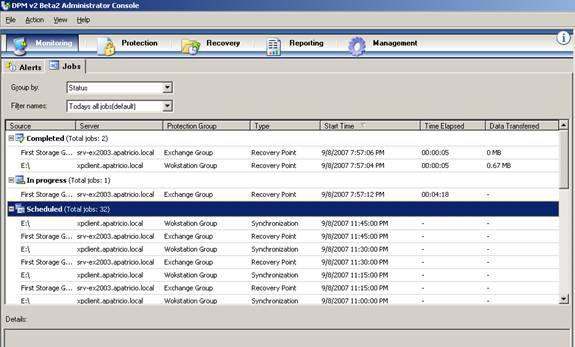
Figure 8: Jobs
Protection (Protection)
In this area we can manage protection groups, protection schedules, disk locations, etc. Also, we can synchronize and create Recovery Points. Can view all servers in the Protection Group (Protection Groups). It is possible to click on a special item and validate a number of points like how many available restore points, the latest, longest restore points and indicate how much disk space is in use to protect the item. somehow as shown in Figure 9.
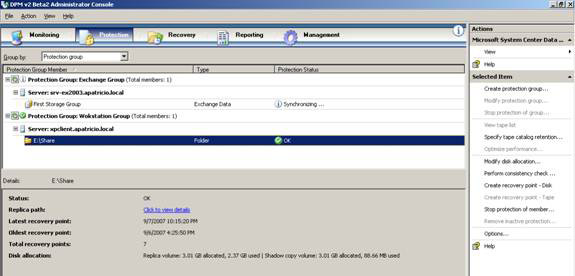
Figure 9: Protection groups
Recovery (Recovery)
In the recovery area, we can restore data protected by protection groups. It is possible to observe all protected servers and items in one view and no need to switch out of this screen to perform an Exchange, SharePoint, SQL or Windows File Server recovery procedure. It is possible to use the schedule to see the specific date and time we have a restore point available. You can also see which media has a selected restore point (disk or tape) as shown in Figure 10.
We can use the Search tab to find available restore points with variables such as: file name or directory, restore point range and root location.
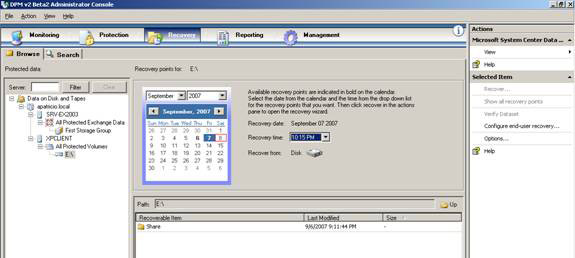
Figure 10: Recovery zone allows us to recover data from DPM Agents
Report (Reporting)
The reporting service has a number of reports that allow administrators to measure a number of items such as: statistics, performance that can help plan hardware resource calculations. We have the reports listed below and can be seen in Figure 11.
- Disk UtilizationProtection
- Recovery
- Status
- Tape Management
- Tape Utilization
Figure 11: DPM's available reports
We can also configure reports generated on a regular platform and sent to an email address that has been selected. Click Report, in the Details Panel, we have two options: Schedule and Email, both have editing links below.
In the Schedule (Figure 12), we can configure the report and frequency parameters. It is also possible to define how many versions will keep in history.
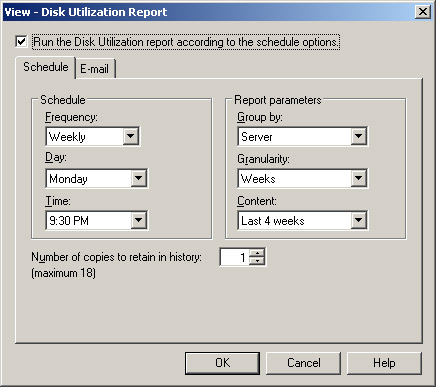
Figure 12: Schedule definition to create a Disk Utilization report
In the E-mail tab, we can define who will receive the scheduled report. To add more mail you just need to add a semicolon between the email addresses (Figure 13). We can also configure the format of the attachments that will be included in notifications such as HTML, Excel or PDF.
Figure 13: Specify who will receive the report
We can right-click on the report and click view to see it. You can see a sample report in Figure 14.
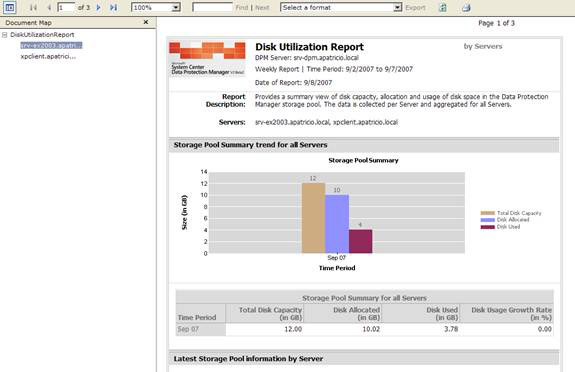
Figure 14: Report has extracted based on DPM Activity - Create schedule report
Or watch it in real time.
Management (Management)
In the Management area, we can use DPM Server components, which are components that interact with the server and store data. These items are Agents, Disks and Tape library
The management of disks and agents was done to prepare DPM for use.
To use the tape library properly in DPM 2007, we must make sure the device is configured in the Device Management section. We can refer to the list of hardware tested with DPM Beta2 here: http://www.microsoft.com/systemcenter/dpm/partners/tapelib.mspx
DPM Management Shell
DPM 2007 can be managed through Windows PowerShell using DPM Management Shell. In the DPM Management Shell, some tasks that are not executed through the DPM administration interface can be done here. Scripts can also be created to facilitate daily tasks. To see a list of all available DPM cmdlets, use: get-DPMCommand.
Figure 15: DPM Management Shell
A useful scripting source and tips on the DPM Management Shell are provided on the DPM team blog, you can find them here: http://blogs.technet.com/dpm/.
Conclude
In this article, I have shown you how to end the DPM deployment process by adding a disk to the repository and installing agents on Windows Server. In the next section, we will show you how to create a protection group and how to recover data in a Microsoft environment protected by Data Protection Manager.
Note :
This article was written using DPM 2007 Beta 2. In the final release (RTM) there may be some features different from what we covered in this article.
 Deploy Data Protection Manager 2007 (Part 3)
Deploy Data Protection Manager 2007 (Part 3)
 Deploy Data Protection Manager 2007 (Part 4)
Deploy Data Protection Manager 2007 (Part 4)