Backup for Exchange Server with DPM 2007 - Part 3: Backup process
 Backup for Exchange Server with DPM 2007 (Part 1)
Backup for Exchange Server with DPM 2007 (Part 1)
 Backup for Exchange Server with DPM 2007 (Part 2)
Backup for Exchange Server with DPM 2007 (Part 2)
Rui Silva
When the first replication of DPM server of Exchange databases is performed, the synchronization problem will appear at a certain frequency, which is configured for short-term restore points. The protection status of each storage group is displayed in the DPM 2007 Administrator Console (Figure 1).

Figure 1: Synchronizing Exchange Protection Group
The Exchange server we are using has two storage groups: the Storage Group's first storage group is composed of 3 mailbox databases from the relevant previous articles that have been introduced and the second group only has Public Folder Database (Figure 2).

Figure 2: Storage Groups and Mailbox Databases
Since this is not a production environment, all Exchange data files (log files and databases) are placed in the C: drive (Figure 3). Note that there are more than 300 log files here.
When an Express Full Backup appears, all log files are truncated when synchronization is successful, because this is actually a full online backup (Figure 4).

Figure 3: Exchange data files

Figure 4: Exchange data files after Express Full Backup
In part one of this article, we mentioned that the synchronization process uses the Exchange VSS Writer. If you look closely at the event log application - Application Event Log - of the protected Exchange server, we need to pay attention to some events related to VSS Backup (Figure 5, Figure 6 and image 7).

Figure 5: ShadowCopy Event
Figure 6: Exchange VSS Writer Event
Figure 7: Exchange VSS Writer Event
How many restore points?
Concerned about the synchronization frequency, we think that setting a minimum cycle (15 minutes) will be overkill. One of the expressions Microsoft uses to introduce that is ' DPM 2007 is capable of providing over 344,000 consistent data restore points for Exchange ' (512 x 7 days x 24 hours x 4). Our advice is to start by setting up your current backup policy and then gradually increase the number of restore points. I think 1 or 2 Express Full Backup is done every day plus a synchronization frequency of 2 hours is a very nice number.
Obviously, no size fits all, you need to include a data drive account, the performance impact on your servers (DPM reduces this effect but it still There are some other influences) and the drive has asked to save the copies.
If you follow these instructions, as long as you practice the best way to save the Exchange database on a drive and the records on other drives are noted, you can be sure. that the possibility of data loss here is very low.
Remember, you can also create a restore point 'manual'. In DPM Administrator Console , in the Protection area, panel Actions , click Create recovery point ¨C Disk (Figure 8).

Figure 8: Create restore point
Copy paths
If you open Computer Management, you can see the names of the drives created by the Protection Group (Figure 9), which are configured settings. If you right-click one of them and select Change Drive Letter and Paths , you'll see the full path where these drives are located (Figure 10). The same information is also displayed in DPM Administrator Console , in the Protection area, select a storage group and click on the Replica Path hyperlink in the bottom pane (Figure 11).
Using Windows Explorer, you will be able to browse to the locations of those copies (Figure 12).

Figure 9: DPM Disk Allocation
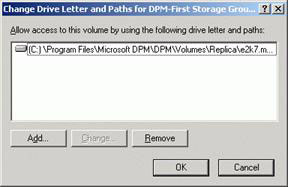
Figure 10: Drive letter and paths
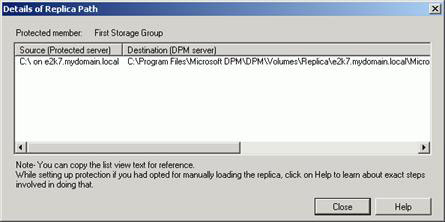
Figure 11: Details of the copy path
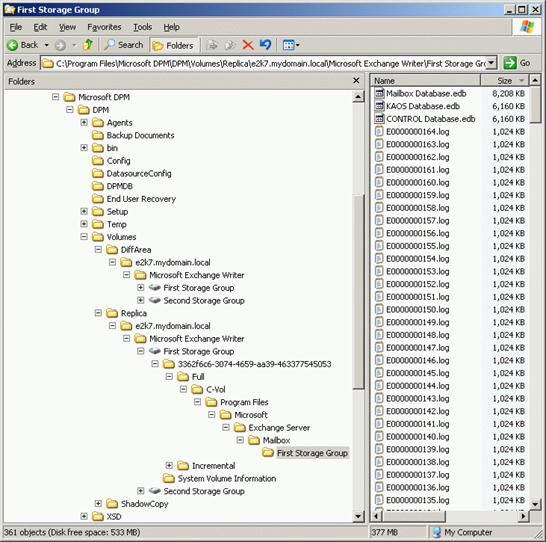
Figure 12: Browse the drive mount point
Additional options
When using DPM protection of Exchange servers, you will have the following additional options:
• Performance optimizations for slow network links . After creating the protection group, you can configure additional performance settings such as adjusting network bandwidth traffic for each protected server and compression issues on the line.
• Adding database mailbox to máy phục vụ . If you create or add mailbox databases to a protected group in the Exchange server, these databases will automatically be added to DPM replication and protection.
• Tập tin thêm thêm vào máy phục vụ If you create or add new storage groups to the Exchange server name, these storage groups will not automatically be added to the DPM protection group. You must change the Protection Group to include these new storage groups.
• thay đổi lưu trữ group hoặc thư mục cơ sở dữ liệu tập tin . If you relocate files that are related to a protected storage group or mailbox database to a new path, the protection will not continue and the copy will become inconsistent. You must run a consistent check on the copy to regain protection.
• Dismounting mailbox databases . If you remove a protected mailbox database, that protected job for that database will be corrupted. The copy will be marked as unsuitable when the next full backup is performed by DPM.
• Renaming storage groups and mailbox databases . If you rename a protection group or a mailbox database, you don't need to take any special steps to ensure that protection continues.
• Moving databases between storage groups . If you move the database from a protected storage group to another group, it will continue to be protected. If you move the mailbox database from a protected storage group to an unprotected storage group, the database will not be protected when a unified test is performed. If the database is transferred from an unprotected storage group to a protected group, it will automatically become protected when the integrity check is performed. In all of these cases, you must run a unified check on all protected storage groups involved in the migration process when the mailbox database transformations are successfully performed.
• End-user recovery . End-user recovery is not supported for protected data in Exchange Server, although it is supported for server data.
SMTP notifications
You can configure DPM 2007 to send notes with email alerts or directives and instantiation recovery states. If you plan to enable this feature, you must first configure the SMTP Server.
Follow the procedures below to register notifications
1. In DPM Administrator Console , on the Action menu, click Options .
2. In the Options dialog box, the Notifications tab, do the following:
- Select the types of alerts you want the person to receive notifications from
- In Recipients , type in the email address of each recipient (Figure 13).
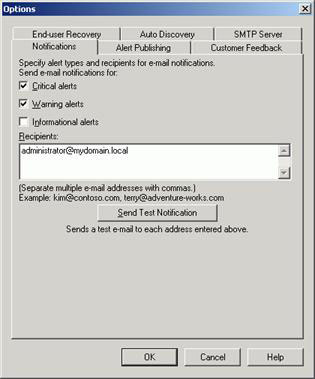
Figure 13: Configuring notifications
3. Go to the SMTP Server tab (Figure 14), type SMTP server name , SMTP server port , and the email address you want to display. In the Authenticated SMTP server area , type in the username and password in the appropriate boxes. User Name must be a user name in the domain (eg domainuser name). The "From" address must be the user's SMTP address.
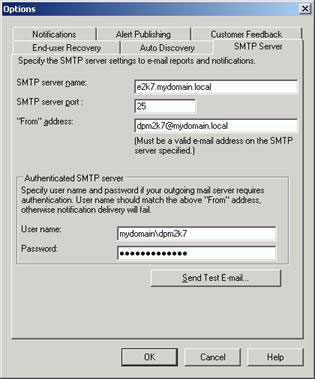
Figure 14: Configure SMTP server
4. To check SMTP server settings, click Send Test E-mail , type the email address where you want DPM to send the test message, and then click OK .
If the user you have selected as the sender does not have administrator rights on the DPM server, you will get an error like Figure 15. If the SMTP server is specified as Exchange Server 2007, you may encounter an error like the one shown below. Figure 16. This is indeed a bug with DPM 2007's current release and Microsoft is working hard to fix this. One alternative is to specify another server such as the IIS SMTP server.
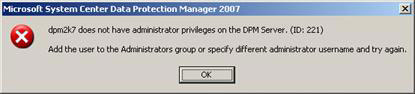
Figure 15: User rights error
Figure 16: Authentication error
Report
DPM has 6 standard reports that you can create, review and analyze. The table below lists their reports and definitions.
Report type Description Status Report The status group creates restore points and recently restored jobs. The report shows the trend according to the frequency of errors that occur and lists the number of warnings. Disk Utilization Report Provides an overview of disk space and location as well as disk space usage for the DPM storage pool. The data is collected on each computer and gathered for all computers. You can use this report to realize the costs associated with backing up other protected computers in addition to recognizing the tendency to take advantage of the drive to plan disk space. . Protection Report Provides statistics comparing available restore points for long-term and short-term protection issues. You can use this information to identify whether backup jobs have been successfully performed and to identify vulnerabilities in backups. Data is collected on each computer or protection group and gathered for all protection groups. Recovery Report Provides detailed information about recovery times and recovery job statistics in recovery performance check issues. Data is taken from each computer and the protection groups are then aggregated for all computers. Tape Management Report Provides detailed information on the management of storage tape rotation and the replacement of these tapes. The report also shows which tapes need to be recycled. Data taken from each library is then gathered for all libraries. Tape Utilization Report Provides trends in tape usage to support capacity planning and make decisions about additional tape positioning.
Table 1: DPM report types
Figures 17 and 18 show an example of the Disk Utilization report.

Figure 17: Disk Utilization Report - page 1
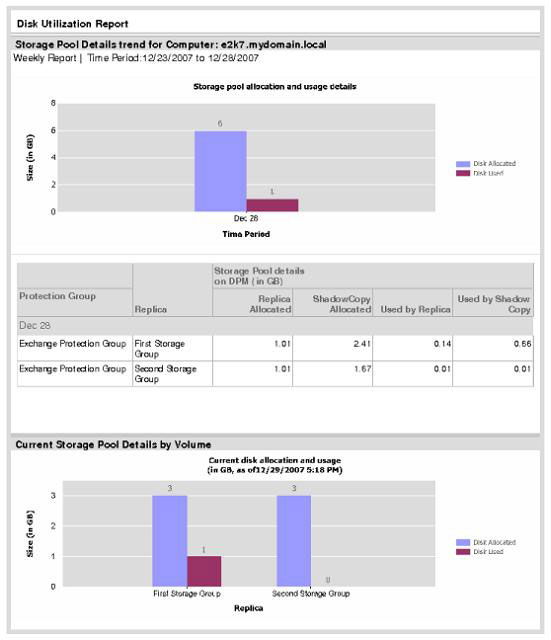
Figure 18: Disk Utilization Report - page 2
Conclude
One of the biggest advantages of using DPM 2007 that I mentioned in Part 1 of this series is that it does not require any special "Backup Administrator" skills.
The next section and the final part of this series will be focused on the recovery process, the most important feature of any backup solution.