6 steps to have a safer computer
This article, gives readers a new and more complete view of security. From there, people can build a safe strategy for their computers at the lowest cost, even for free.
Step 1: Secure your computer for what?
Sometimes when we listen to the mass media or security companies that threaten this security risk, there is a risk of security, so we become too serious about making computers secure. However, have we ever asked ourselves to make computers safer to do, to protect something. When we can correctly answer these questions, we have initially succeeded in establishing a reasonable computer safety mechanism in every way. We have some sample answers for readers to refer to:
- To help your computer run faster and cleaner because there are no adware, spyware, viruses
- Do not want to be stolen personal information, do not want to lose mail account, game account.
- Do not want to turn on every IE browser again to be pushed to a strange page
- Do not want to be hijacked by hackers using computers for bad purposes
- Want to control internet usage for children in the family
Step 2: Consider between security and usability
When you use a computer at home, you often have to use it with other family members. If you are too concerned about safety, you can install enough things to protect the machine. They use it, they hardly understand the functions of the things you think are necessary for security. Not only that, they also feel extremely troublesome when using them because doing something also pops up. from personal firewall ask Yes or No.
So you need to consider security and ease-of-use for all users of the same computer. Also, you should instruct those who do not know the computer of sports features and usage. Basic work with software and security features available on the machine. There is such a goal of creating a secure computer with the opportunity to achieve
Step 3: Have a secure operating system first
Before you decide to install something like anti-virus software or personal firewall or something to protect your device, be aware that there are things you must do first to reconfigure the system. I am using it to be really safe and create a good foundation for security software installed on it. You should take the following steps to have a safer operating system.
+ Account security :
- Set a harder password. You can use tips to get the first letters of a sentence or more verse than seven words to create a hard password
- Transfer all currently used accounts to Users user group. Create a new admin account and only use this account for installation and configuration tasks. This way you minimize the risk. virus and trojans infiltrate critical areas because they cannot borrow rights from accounts with administrative rights on the computer
- Do not share admin passwords for many people.
- When leaving the computer, it is recommended to lock the computer or log out of the account
+ Lock services not used on the Operating System (OS) :
You imagine your OS is a multi-storey house, each floor has many windows. If you open too many windows, the thief will have many access and exit. You need to close unused services. You can find out about each service and consider whether to turn it off or not.
+ Windows operating system without copyright = Windows operating system is not secure :
We have no intention of advertising the sale of Microsoft for Microsoft Vietnam. We just want to emphasize one point if you are using an unlicensed operating system, 99% of that OS is facing a lot of security risks. .
The simple reason is that these operating systems not only don't run stably but they also have a lot of security flaws because they are not updated with official patches from Microsoft. We often talk funny if you don't want to give up 130 $ to buy a copy of the copyrighted copy goes to Redhat Linux, which is the strongest
+ Have you updated the patch completely or not :
In order to have an operating system against the risk of attacks based on system errors from viruses and hackers, you must immediately update the patches as soon as possible. The simplest way to do this is to turn on Automatic Updates function. Follow these steps:
- Click Windows + Break to turn on System Properties
- In the System Properties window, select Automatic Updates tab
- Select Automatic mode (recommended)
+ Check and re-evaluate the security of the entire operating system automatically :
Countless times, we need to have a review and review every time. Microsoft provides us with a completely free tool to test the security of the whole operating system, MBSA. 2.0.1 (Microsoft Baseline Security Analyzer).
This tool allows you to control and report the necessary security configurations on any Microsoft operating system. This tool is easy to use, can be downloaded here.
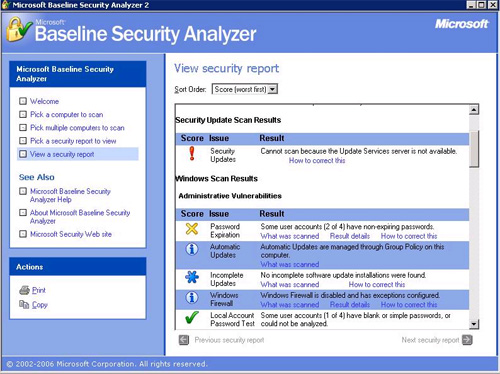
Figure 1
Step 4: Security for all applications
+ Update the patch for the application
When we have a secure operating system, it is not enough to give us a really secure computer because in addition we have a lot of different software installed on it and of course they also have full of security flaws. So what we need to do here is to check for the latest update or version for the software on the computer.
If this is done manually, it is really hard and not easy for most users. Fortunately, we have a tool to perform security check for software on Personal computers. Software Inspector of Secunia.
With a database of 4200 applications on the computer, it allows you to check most of the software updates you can on your computer. This software is easy to use and especially free for you. Personal users, you can download here.
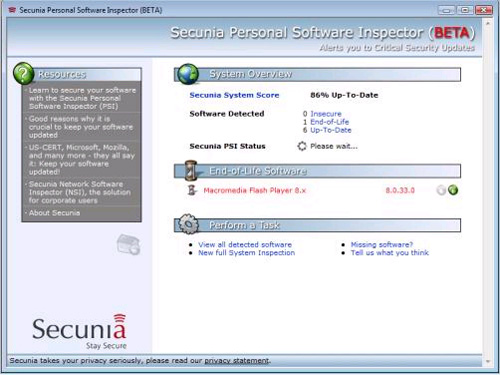
Figure 2
+ Armor for Internet Explorer browser
One of the applications that could be used to infect viruses and Trojans on personal computers is the browser. The famous browser is infected and the security weakness is Internet Explorer (IE). this is the most used browser. So to increase IE protection classes we use Haute Secure's free Haute tool.
The tool allows to prevent unauthorized downloads of malicious files from malicious sites, preventing websites that contain malicious code that can be used by hackers to take control of the computer. With each site, Haute Secure will prevent or warn users. You can download the software here.
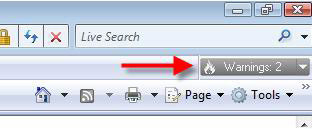
Figure 3
+ Protect personal information
Information that you seem to be harmless like browsing habits, websites that are often visited are saved as cookies and temp files. This information can be collected again and then will be send to you via spam or web.
To ensure that this personal information is not unauthorized use, you should use the free CCleaner tool. The tool gives you many options to remove all personal information, bookmarks on the web like Temp, Cookies, history . files You can download here.
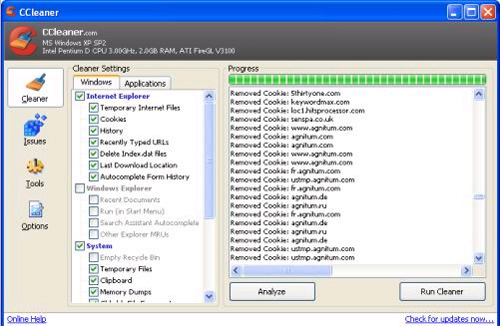
Figure 4
Step 5: Prevent Malware
Here we use phonetic Malware to be used only for all types of viruses, trojans, spy-ware, adware, keyloggers and rookit. You might ask why there are so many types and there is a lot of need. tools for each type or not, we will need at least two tools for all of these types of malware and they have a variety of reasons for the nature of the operation and the different ways of infection.
+ Prevent Virus, spyware, trojans :
Featured among the free antivirus tools are AVG and Mcafee Virus Scan Plus American Online versions. By testing we found that Mcafee Virus Scan Plus is better at killing viruses, spyware and especially recognizing Internal viruses such as Yahoo Messenger virus, USB virus infection. Not only that, but Virus Scan Plus Mcafee also shows a superior advantage over AVG colleagues in that it consumes less computer resources and protection features. You can download the Online Mcafee Virus Scan Plus American version here: http://www.activevirusshield.com/antivirus/freeav/index.adp?
Figure 5
+ Prevent Rootkit :
Rootkits are a type of Malware whose level runs at the OS level so it may be out of control of existing Virus software so we need to equip ourselves with a dedicated Rookit scanning tool.
- The tools AntiRootkits need and should be in the system
Figure 6
+ Advertising software and annoying software :
If you get into adware and other annoying software, you should use the free PC Decrapifier tool to scan and remove these software. You can download here

Figure 7
Step 6: Control content and prevent intrusion
Imagine your computer is a rampart. To protect your stronghold you need to build a deep moat to prevent enemies from entering the castle, and then there must be guards on the ground and walls. City to check the passersby.
Also on a computer, a firewall is used to do the same to protect computers, operating systems. It serves to control applications that access to the internet as well as applications or people outside the internet to access. Update inside the computer.
In addition, it also allows us to set policy rules to allow or not allow an application, connection to enter or exit.
Since Windows XP SP1 onwards, Microsoft has equipped a personal firewall for computers, but this is only a one-way firewall. Only allow connection control from inside out. However, in Vista version, Microsoft has overcome this feature by introducing a personal firewall version that can block information filtering at both ends (see Figure 8).
Figure 8
However, not everyone is using Vista, so we recommend using a free fire-trust product called Zone Alarm from Checkpoint (see Figure 9). Zone Alarm allows you to control two-way connections. In addition, it allows you to monitor and set policies for applications on the computer. Zone Alarm also has 3 configuration levels that allow you to loosen or lock up the computer with a firewall at 3 levels High, Medium and Off .To download Zone Alarm you go to: http://download.zonelabs.com/bin/free/1025_update/zaSetup_en.exe
Figure 9
Nguyen Vu Cao Son (Microsoft Security Specialist)