How to use Trend Micro RansomBuster blocks ransomware
Along with viruses, ransomware is also a dangerous threat to computer systems and the speed of spread worldwide. To prevent that kind of attack, antivirus or ransomware software is a necessary tool on every computer.
Trend Micro RansomBuster is a tool to detect suspicious files or software on your computer to notify users. Besides, the tool also has the feature to block the spread of ransomeware, if the computer is infected with important folders. The following article will guide you how to use Trend Micro RansomBuster on your computer.
- How to get rid of root virus * .OSIRIS - Ransomware Locky?
- Enable ransomware Controlled Folder Access on Windows 10
- How to use Kaspersky Free antivirus software
How to prevent ransomware on computers
Step 1:
Click on the link below to download and install Trend Micro RansomBuster software on your computer.
- https://ransombuster.trendmicro.com/

Step 2:
Wait for the system check, then click Agree and Install to agree to the terms.

Wait for the installation of Trend Micro RansomBuster software to complete.
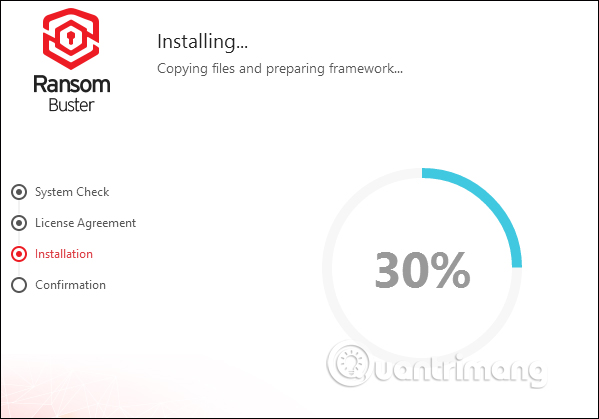
The tool will ask the user to enter an email address to confirm the account as well as receive new information from the manufacturer. Enter the email address and click Finish below.
Step 3:
The program will run automatically at startup and located on the system tray of the computer.
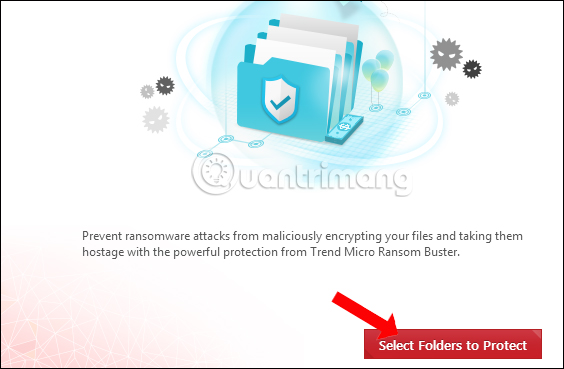
In the main interface of the software, press Select Folders to Protect . By default the software will protect all files and folders located within the Documents folder.
To add new folders click Manage Folders .
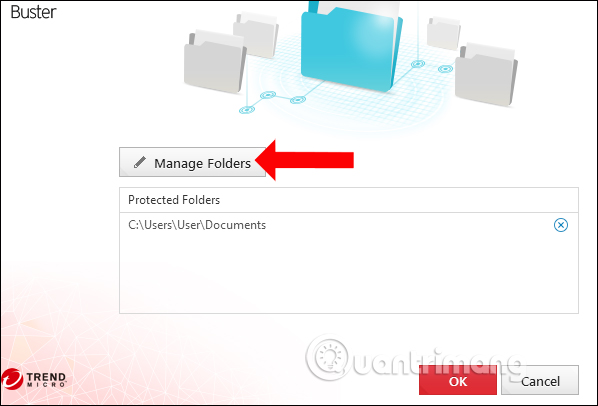
Step 4:
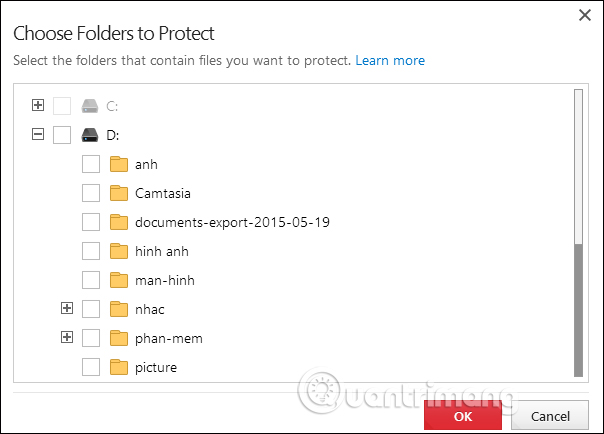
Display interface to select the folder. Click the plus icon to expand the selected content.Check the box to select the folder you want to protect and click OK below.
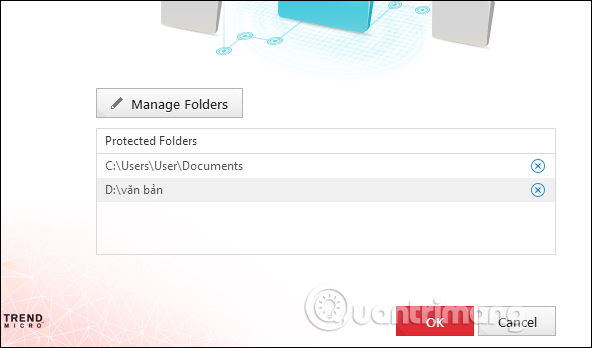
The results will see the folder displayed in the Trend Micro RansomBuster interface. If you want to cancel the folder you want to protect, click the X icon. Click OK to continue
Step 5:
The tool will then proceed to set the security mode for the selected folder.
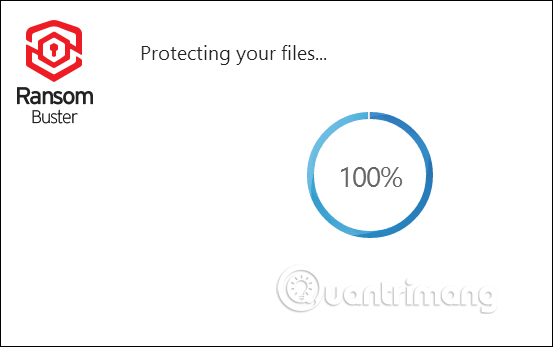
The total number of files in the secured folder will be displayed on the software interface.
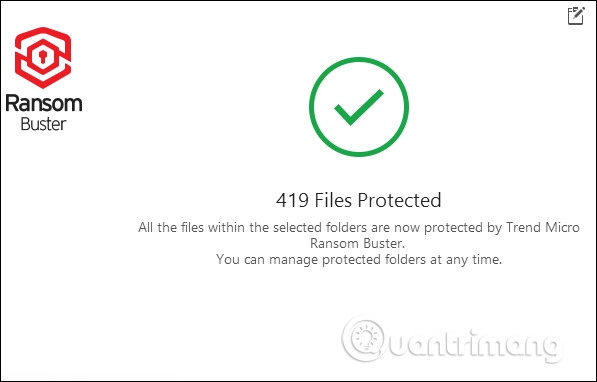
Step 6:
Also, if you trust certain applications , you can add permissions that allow these applications to access the protected files or folders in the Trusted Program List section .
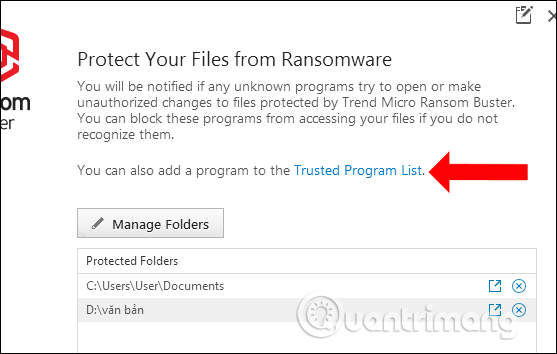
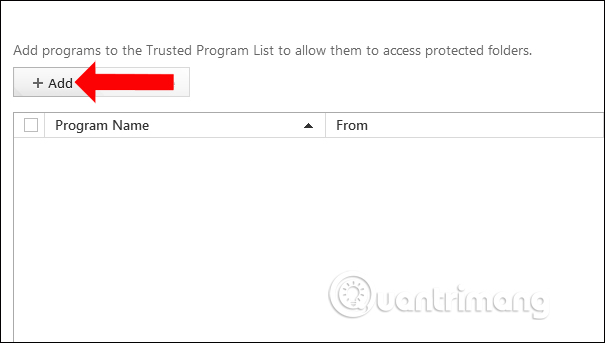
Step 7:
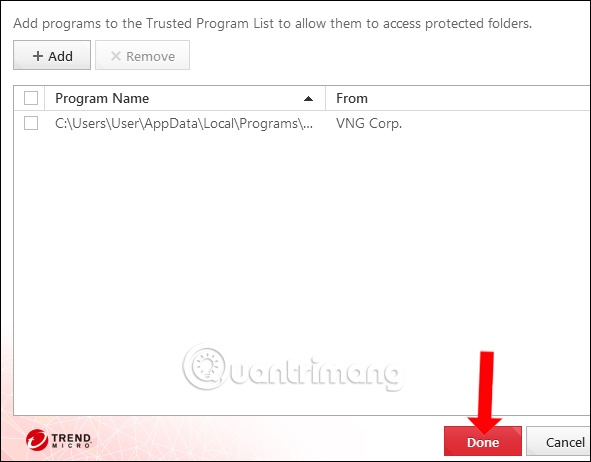
Display the interface to add the application, click the Add button .
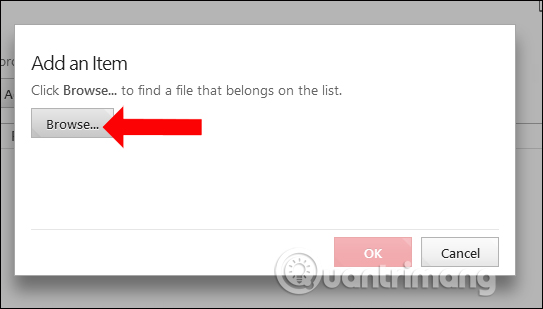
Click the Browse button to find the application installed on your computer.
The user will then see the application installation file displayed in the directory. Click Done to save. In case you want to delete a trusted application, check the file and click Remove to delete the file.
Trend Micro RansomBuster will automatically operate the background on the system to search for strange software accessing the protected file or folder. You will then have the option to block the access of the application, or to bring it into a trusted application to access.
See more:
- Some ways to check the safety of links
- Risks from malware and how to prevent it
- Remove root malware (malware) on Windows 10 computers
I wish you all success!