These Anti-Rootkit tools should and should be in the system
TipsMake.com - There are many types of malware, in which, software using rootkit technology is the most annoying because they are difficult to detect and remove.Rootkits are capable of potentially destructive, sophisticated camouflage and cloaking.Rootkit technology can hide its presence in the most basic tools integrated on Windows like Task Manager, to the most reliable firewall or even in antivirus software, and you don't even find So what are they on the machine?This happens when installing and downloading drivers with kernel-mode that can allow malware to run with higher priority.
Most rootkits spend all their time hiding and finding ways to gain control of the system without being detected. Typically, if you use the Task Manager tool of Windows, Anvir, Process Explorer or any similar program, it is impossible to detect the behavior of rootkits, it is also capable of hiding all files and messages items in Windows Explorer even if you have a mode to display hidden files and systems.
Recently, there have been many remote trojan control tools that have the option to create file servers along with rootkits, but fortunately, they are rarely used because these features are extremely sensitive, plus if programmers or controllers do not 'make sure' they will cause instability on the victim's computer or may not gain control as well as other resources as desired.
Although the 64-bit Windows operating system is basically safe from rootkit infections because by default the operating system only accepts digital signatures, but there are cases where valid digital certificates are hacked. stealing and using them for pirated drivers to bypass security software and Windows. Anti-virus software doesn't work much with rootkits because the Stuxnet worm has been infected on computers for years before it was discovered by VirusBlokAda, VBA32 antivirus software developer.
Because normal anti-virus software is hard to detect and completely remove rootkits on your computer, in this article we will check out some specialized anti-rootkit tools to check and see if they can play. There are 3 different types of keyloggers available (All In One Keylogger, KeyLogger Stealth Invisible, Elite Keylogger). These keyloggers all use rootkit technology and are installed on the computer. And this is the result:
avast! ANTIROOTKIT
This is a free anti-rootkit and no installation tool . It has been quite outdated and has not been updated since 2008 because it has been integrated into Avast's antivirus software. However, you can still download directly from Avast server. This tool can detect All In One Keylogger and cannot detect the other two types. After scanning, just click Fix Now to completely delete the files after restarting the computer.

Kaspersky TDSSKiller
This tool can detect and remove Alureon, TDSS, TDL rootkits and some other rootkits including bootkit. But with 3 rootkits in this test, Kaspersky TDSSKiller did not detect.
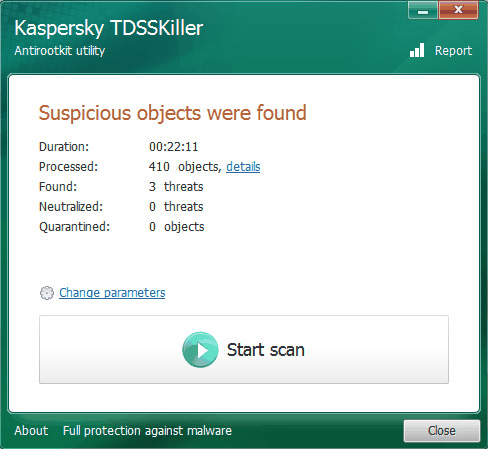
McAfee Rootkit Remover
This tool runs on the command line interface, which is quite light, it can detect and remove ZeroAccess and TDSS rootkit lines. But it doesn't recognize the three types of rootkits that are testing.
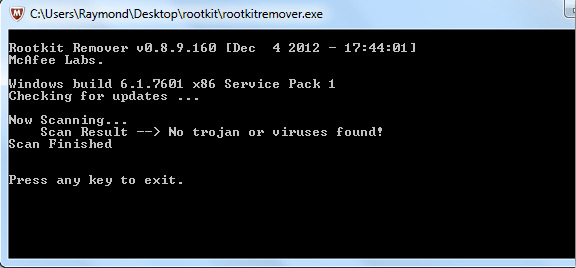
Norton Power Eraser
This tool is only about 3MB. Its rootkit scanning option is enabled by default. Norton Power Eraser detects All In One Keylogger and Invisible KeyLogger Stealth. For Elite Keylogger, a DLL file is marked as Unknown.
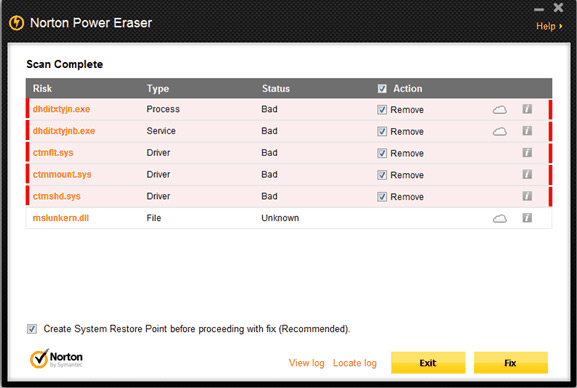
Trend Micro RootkitBuster
Trend Micro RootkitBuster is a free tool that can check multiple locations on your computer, such as the Master Boot Record, files, registry entries, drivers, processes, services, etc. to determine if a rootkit exists. at or not. Unfortunately, this tool only detects All In One Keylogger.
UnHackMe
UnHackMe detects that All In One Keylogger and Invisible KeyLogger Stealth ignore Elite Keylogger.
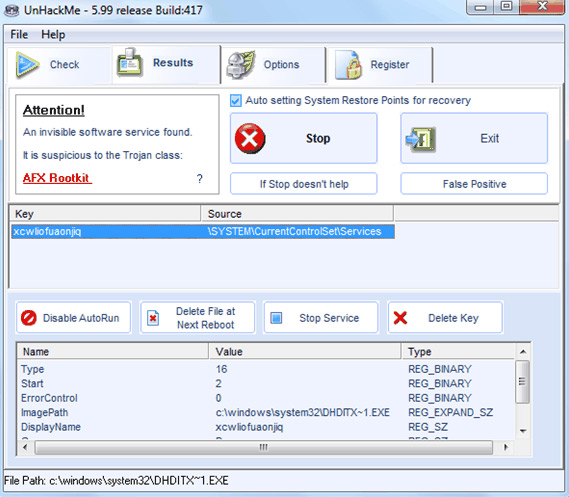
We also check out some other tools such as COMODO Cleaning Essentials, Dr.Web CureIt !, F-Secure Safe Easy Clean, Sophos Virus Removal Tool, VIPRE Rescue, Virit eXplorer Lite, AVG Anti-Rootkit, Bitdefender Removal Tool ( Rootkit Remover), Malwarebytes Anti-Rootkit but unfortunately they can't detect 3 trial rootkits.
You can see that rootkits are a very difficult type of "play", big security vendors all release rootkit detection and removal products, but most can only detect two of the three types we are testing.
Note: Whether you are familiar with anti-rootkit tools or not, use them carefully to avoid disabling an important process or driver, making Windows unable to boot properly. Find out more information about the process, the driver on the network before deciding whether to disable it.