6 free security tools needed
We will not let you wait anxiously but go straight to the problem and name of these tools. These 6 free security tools are tools that all IT workers should know and use. These tools are MetaSploit, Splunk, Google (this is true), KeePass, Helix and Netwox. Now let's find out why .
MetaSploit
This tool has a very strange name, but MetaSploit is a very good development platform that can support IT security experts in creating tools and exploiting vulnerabilities. Using the framework (its built-in tools), you can perform tests, verify patch settings and even perform regression tests. Written by Ruby, the current version of 3.1 has up to 450 modules, including 265 remote vulnerability exploits that can be targeted at the release of Windows, Linux, BSD and Mac operating systems. If that isn't enough built-in functionality for you, you can use MetaSploit to create your own modules or modify some of the built-in functions.
It can be said that this is a great tool and when in the hands of system administrators it can perform security tests for the organization. However, there are also two aspects of the problem. MetaSploit is also an effective tool for performing attacks.
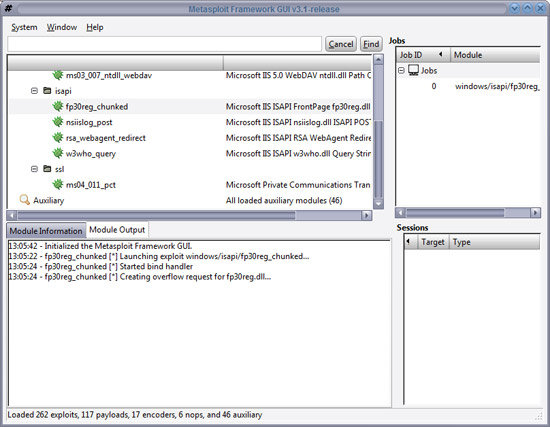
For more information about MetaSploit you can visit the website www.metasploit.com
Splunk
Splunk has a similar approach to Google, the main purpose is search engine. However, developers have focused their efforts on making Splunk a collection of information related to IT and events. Splunk differs from SIEM (Security Incident and Event Manager, it can provide a foundation for analysis and correlation. With some hidden methods, Splunk acquires data and provides rankings. In view. Our ability to show different record structures (allowing you to provide Splunk data through known base text) is a very powerful feature of this tool.
Note : Splunk is not an open source tool, but you can download it for free under the free software subscription from its software developers.
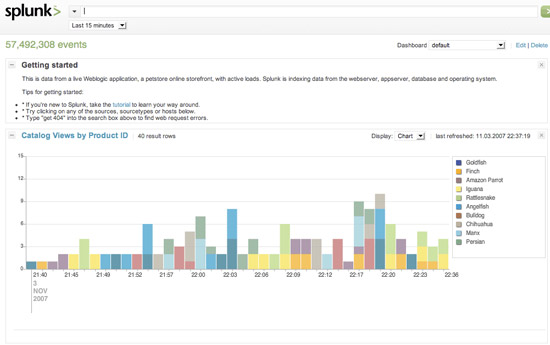
For more information about Splunk, you can visit the website www.splunk.com
Google
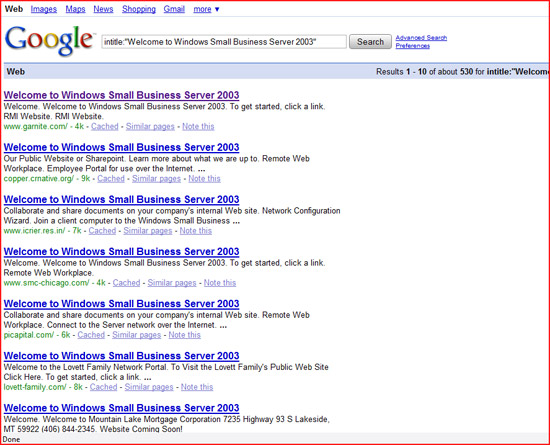
You can laugh when we talk about Google, what you currently know about Google is probably a huge search engine? But really it is also a great security tool for us. Like Splunk, Google is also a collection of information. The main difference between these two tools is that Google provides you with a large amount of publicly available information. The things that you can use Google for security purposes here are:
- Gather information about your target
- Perform basic intrusion tests
- Search for sites that allow indexing of directories
- Search for pages by certain phrases by title
- Search for specific pages through phrases
- Or even get Google to cache the necessary information.
KeePass
This is a program that I really like. KeePass is a completely free, open source password management application. Using KeePass you can save all important information in a secure database so that you can access only one master password, key (one file), one master key +, or information. Important of Windows. Here are some reasons for using this utility:
- The database is encrypted with AES and Twofish
- Portable and no installation required
- Easy database transmission
- Support password groups
- Safe and intuitive Windows Clipboard management
- Search and sort support
- Support multiple languages
- Strong random password generator
- Plugin Architecture
- The last and most important thing for KeePass is open source.
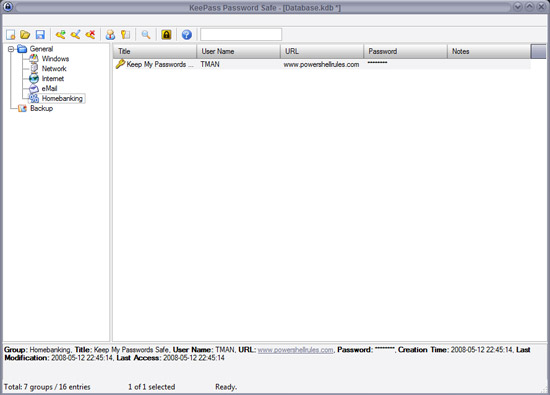
For more information about KeePass you can visit the website www.keepass.info
Helix
In the context of your CEO's request to perform an analysis of the CEO's computer to find evidence of data theft. Besides taking other obvious steps to manage things (depending on your organization), how can legal evidence be found?
One method can buy and use it is EnCase (just a little money). Another method here is to be able to hire a legal firm (this is much more expensive). Or you can use a utility called Helix, which is provided in the Knoppix Live Linux CD. By using Helix and the boatload of that tool you can easily create an investment without having to change the server in any way.

For more information on EnCase, visit www.e-fense.com/helix
Netwox
Netwox is a utility with over 222 different tools. The tasks you can perform using this utility are:
- Trace data packets
- Collect files via HTTP
- Perform brute force attack on FTP server
- Use Netwox as the back door on the system
- Fooling data packets
- Encrypt computer files
For more information about Netwox you can visit the website http://www.laurentconstantin.com/en/netw/netwox/
 Overview of Windows Server 2008 Firewall with advanced security features
Overview of Windows Server 2008 Firewall with advanced security features Top 5 security settings in Group Policy of Windows Server 2008
Top 5 security settings in Group Policy of Windows Server 2008 Overview of Windows Server 2008 Firewall with advanced security features - Part 2
Overview of Windows Server 2008 Firewall with advanced security features - Part 2 Top 10 free online antivirus programs
Top 10 free online antivirus programs Overview of Windows Server 2008 Firewall with advanced security features - Part 3
Overview of Windows Server 2008 Firewall with advanced security features - Part 3 Delete temporary Internet files with Group Policy Preferences
Delete temporary Internet files with Group Policy Preferences